Impact of Microsoft Exchange ProxyNotShell Vulnerabilities on the Supply Chain
Written by: ceren
Written by Ferhat Dikbiyik
Edited by Haley Williams
Recently discovered 0-day vulnerabilities called ProxyNotShell on MS Exchange Servers have become a nightmare for cybersecurity professionals. The vulnerabilities exploited in the wild allow hackers to gain access to email servers and can be used to infiltrate the vendor ecosystems of target companies.
MS Exchange vulnerabilities are commonly used by threat actors, especially ransomware groups, to gain access to target systems. Recent examples include:
- AvosLocker using MS Exchange ProxyShell vulnerabilities as reported by the FBI
- BlackKat exploiting MS Exchange ProxyLogon vulnerabilities as reported by Microsoft 365 Defender Threat Intelligence Team
What are ProxyNotShell vulnerabilities?
Officially tracked as CVE-2022-41040 and CVE-2022-41082, these vulnerabilities were initially discovered by GTSC, a Vietnamese security company, and later published by the Zero Day Initiative on September 28, 2022. GTSC claimed that the vulnerabilities had been exploited in the wild since August of 2022.
Microsoft confirmed the vulnerabilities the following day. One of the vulnerabilities is a Server-Side Request Forgery (SSRF) vulnerability, while the other allows remote code execution (RCE) when PowerShell is accessible to the attacker.
When exploited, adversaries could access the systems, make lateral moves in the network and deploy web shells. It is important to note that, for successful exploitation, attackers require authenticated network access. Threat actors with enough resources, such as ransomware groups, can get access from Initial Access Brokers (IABs) or through credential stuffing attacks.
What Microsoft products are currently affected?
The Microsoft-published Customer Guidance on the vulnerabilities states that MS Exchange 2013, 2016, and 2019 are the products affected by ProxyNotShell vulnerabilities. Considering how commonly these products are used, the scale of the exploitation risk is significant.
How many companies are currently affected by ProxyNotShell?
According to a recent market share report, more than 100,000 companies use MS Exchange. 54% of said MS Exchange customers are US companies, with Information Technology and Services (16%) and Computer Software (6%) being the top segments. These companies are usually technology and software vendors of large organizations such as financial institutions, manufacturing companies, etc.
A basic Shodan search also shows more than 180,000 servers publicly visible, where 41,000 of them are in the United States.
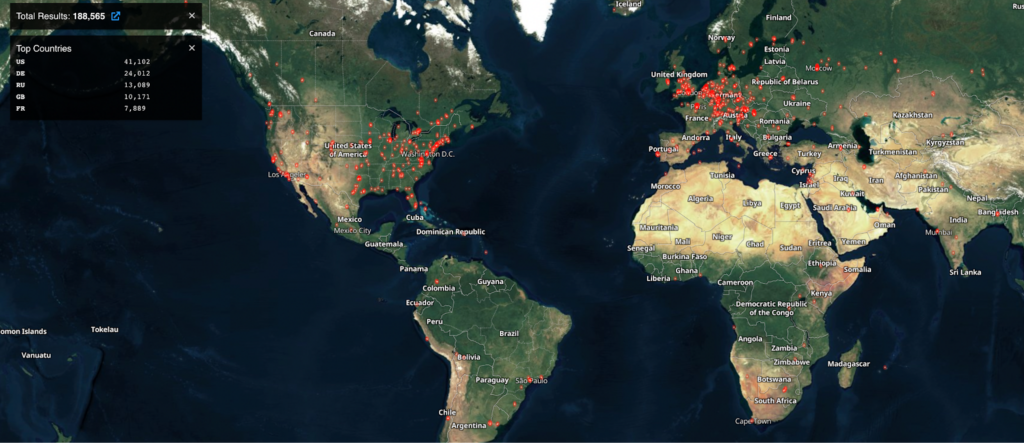
Supply Chain Risk Caused by ProxyNotShell
Companies that do not use MS Exchange are not exempt from ProxyNotShell vulnerability risk. Threat actors can exploit the ProxyNotShell vulnerability on one or more vendors to gain access and navigate through the vendor ecosystem to attack larger organizations.
—
Vulnerability Software Identifier
Within the Black Kite Platform, the Vulnerability Software Identifier (VSI) gives a quantified risk assessment over a vendor. Black Kite identifies the vulnerable software with the impact analysis of a software vendor by estimating the probability and impact of a cyber incident on your organization because of a vendor. In addition to the technical rating, VSI produces a digestible, easy-to-understand classification of software vendors to determine the vulnerable software more thoroughly.
Based on the impact and probability of an incident caused by a vendor, the analyzed software vendor falls into one of the four quadrants in the Impact Matrix.
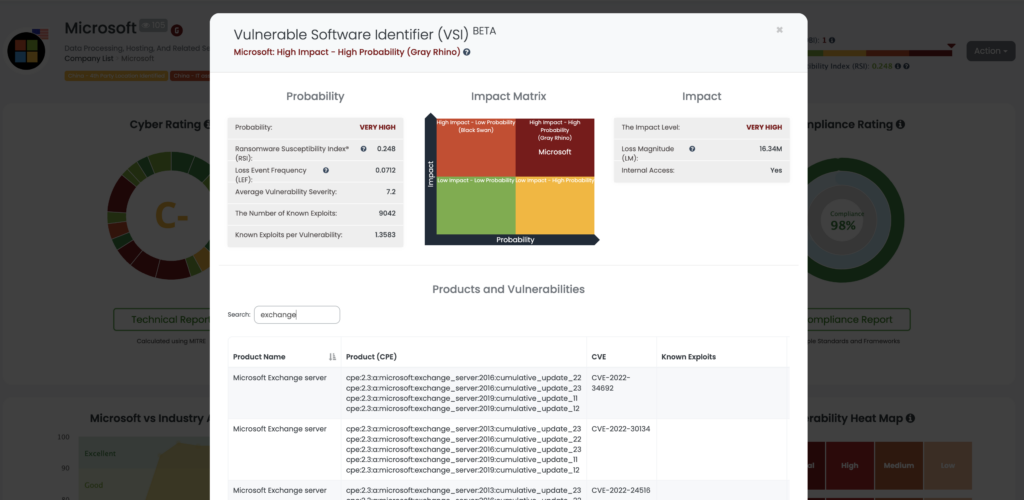
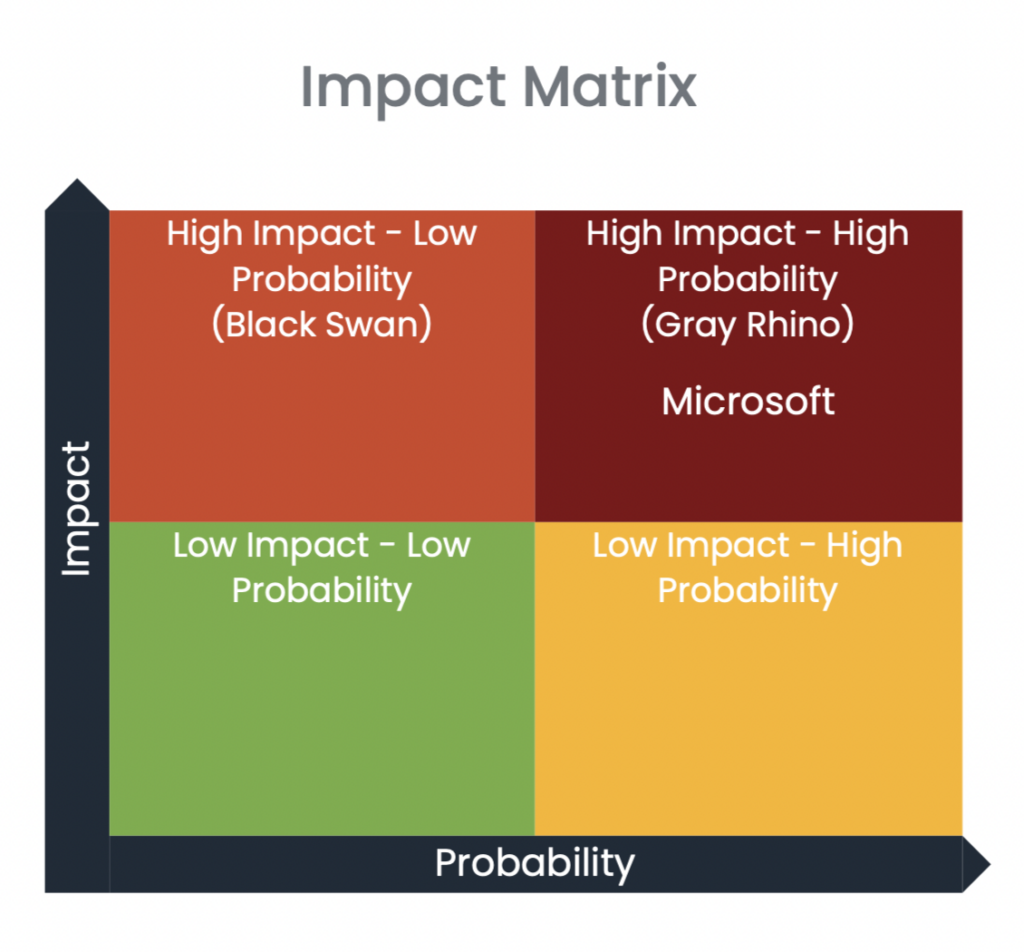
According to the Black Kite findings, Microsoft is a High Impact – High Probability (Gray Rhino) vendor. In this quadrant, the probability of experiencing a cyber event and the impact of an event is high.
Any software vendors that fall into this category are also critical to the organization. These high probability, high-impact threats are called Gray Rhinos, “like a two-ton rhinoceros aiming its horn in our direction and preparing to charge.” A Gray Rhino is a slowly emerging, obvious threat often ignored or minimized. At the same time, the potential impact of the event itself is dismissed, as it happened in the SolarWinds breach.
Cascading Supply Chain Cyber Risk
Outside of Microsoft, organizations should look into other vendors using vulnerable MS Exchange servers. Considering the product’s everyday use among IT companies and software vendors, organizations should focus more heavily on these vendors, as they will be the primary target for motivated threat actors.
Any attacker who exploits the ProxyNotShell vulnerability on a software vendor can access the source code and insert malicious code into the software product to create a backdoor on the systems of software customers. The cascading effect of such an attack can spread to other companies in the vendor ecosystem.
—
How to Mitigate Supply Chain Risk of ProxyNotShell
Microsoft published formal guidance, and step-by-step instructions can be found here. The first steps include:
- Determining the vendors that use MS Exchange 2013, 2016, or 2019
- Making sure that those vendors follow the instructions provided by Microsoft
- Monitoring your third parties patching cadence
- Continuously monitoring their overall general cyber security posture
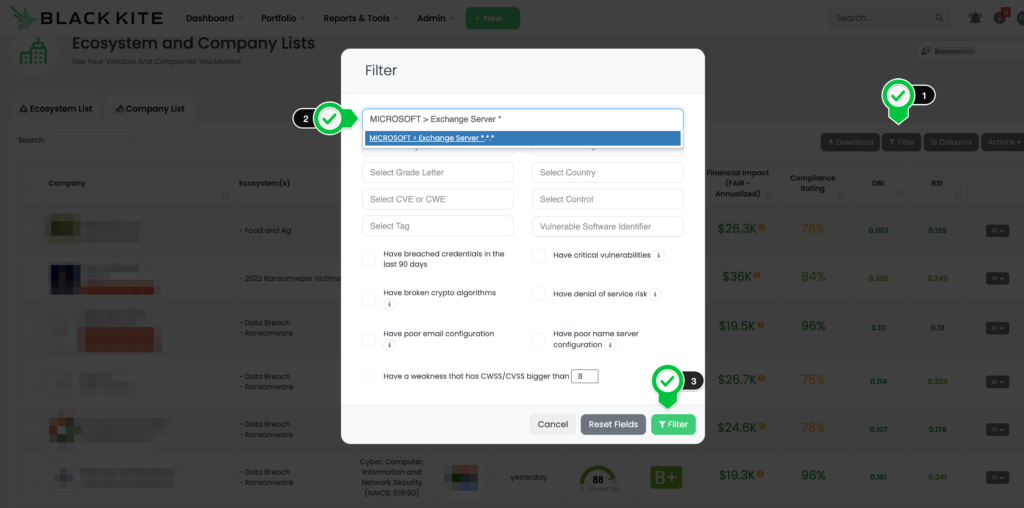
How does Black Kite help determine vendors with a ProxyNotShell vulnerability risk?
Black Kite allows its customers to determine which vendors use specific versions of MS Exchange. Black Kite customers can use this filter by product options on the monitored vendor list to list their vendors that use affected products.
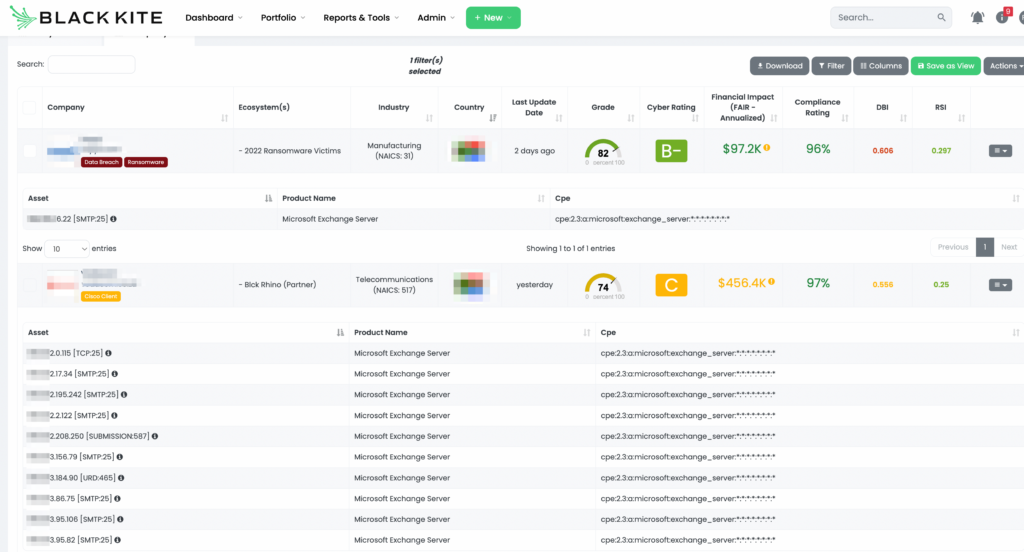
The first step in monitoring vendors for vulnerabilities like ProxyNotShell is to have continuous visibility into your supply chain. Start with a demo on the only security ratings platform built for third-party risk: Black Kite.
Schedule a Demo
