The OWASP Top 10 2021 Highlights Changes in Cybersecurity
Written by: ceren
Written by Gokcen Tapkan
Edited by Haley Williams
The new Open Web Application Security Project (OWASP) Top 10 has had the cybersecurity community buzzing since its release. OWASP celebrated its 20th anniversary in a big way with the new list that provides a comprehensive summary of what’s changed over the past four years with feedback from hundreds of security companies and experts.
What’s New Since 2017?
Of the comparisons made since 2019, a more quantified risk approach is what quickly grabbed our attention as the Black Kite Research Team. In the past year alone, lessons learned from software supply chain attacks like SolarWinds also inspired the list to add the Software and Data Integrity Failures category. We also see the effects of the “Security by Design” mindset dictated by the many new regulations including GDPR lead to the addition of a brand-new category; “Insecure Design.”
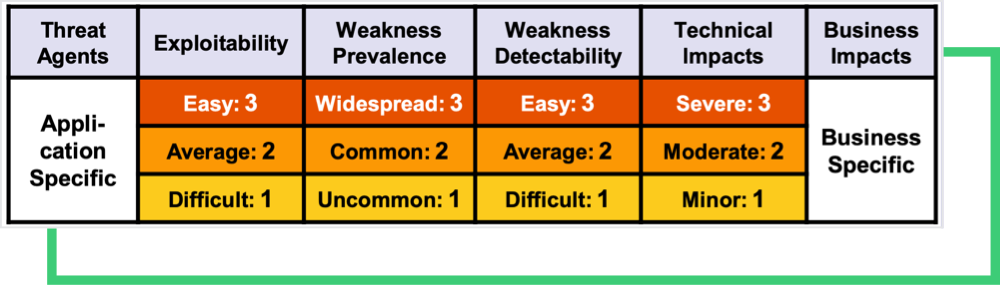
I. A Quantified Risk Approach
The 2017 OWASP Top 10 used a risk rating system to rate the categories: Exploitability, Detectability (also likelihood), and Technical Impact were the criteria in selection and ordering.
| CWEs Mapped | Max Incidence Rate | Avg Incidence Rate | Avg Weighted Exploit | Avg Weighted Impact | Max Coverage | Avg Coverage | Total Occurrences | Total CVEs |
|---|---|---|---|---|---|---|---|---|
| 40 | 24.19% | 3.00% | 6.46 | 6.78 | 77.25% | 42.51% | 262,407 | 2,691 |
Source: OWASP Top 10 2021 Risk Rating Methodology
However, the 2021 edition leveraged a more complex and data-driven approach. Each category in the list is mapped to several of MITRE’s Common Weakness Enumerations (CWEs). For example, the first category, A01 Broken Access Control, is linked to 34 CWEs, including:
- CWE-22 Improper Limitation of a Pathname to a Restricted Directory (‘Path Traversal’)
- CWE-23 Relative Path Traversal
- CWE-35 Path Traversal: ‘…/…//’
- CWE-59 Improper Link Resolution Before File Access (‘Link Following’)
- CWE-200 Exposure of Sensitive Information to an Unauthorized Actor
- CWE-201 Exposure of Sensitive Information Through Sent Data
- CWE-219 Storage of File with Sensitive Data Under Web Root
The second stage groups related Common Vulnerabilities and Exposures (CVEs) under the CWEs. The Exploit and (Technical) Impact of CVEs are then collected and averaged with regards to CWEs. The incidence rate is then leveraged to calculate the risk rating.
OWASP is Data-Driven (to an Extent)
The OWASP community phrases the process as “data-driven, but not blindly.” Eight of the risk categories were selected by the submitted data (See Methodology) and two were selected from the community survey. According to the OWASP community:
“[Application Security] researchers take time to find new vulnerabilities and new ways to test for them. It takes time to integrate these tests into tools and processes. By the time we can reliably test a weakness at scale, years have likely passed. To balance that view, we use a community survey to ask application security and development experts on the front lines what they see as essential weaknesses that the data may not show yet.”
II. Software Supply-Chain Security
One of the new categories named A08 Software and Data Integrity Failures is introduced to the list due to the abundance of Software Supply-Chain attacks such as the SolarWinds incident. An insecure CI/CD pipeline can potentially introduce unauthorized access, malicious code, or system compromise. This is one reason why auto-update functionality is included in many applications. Updates without sufficient integrity verification can be bound to the previously trusted application version, thus inducing a chain of cyber attack vectors.
III. Security-by-Design Mindset
The language of the new list incorporated “Failures” in 4 categories, which is an indication of the “Security by Design” mindset. Although it has been prevalent for a decade, this mindset was consolidated by the enforcements of GDPR, CCPA, and NIST standards. This mindset is also visible for the newly added category, A04 Insecure Design.
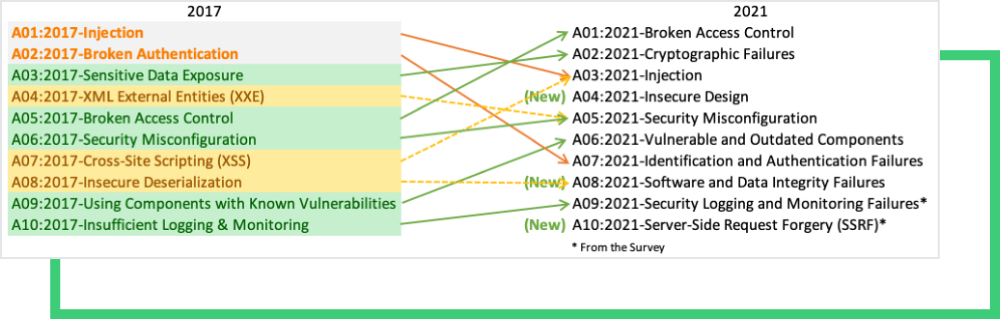
The OWASP Top-10 Newcomers and Shifts
Three additions were made to the Top 10 OWASP Security Risks for 2021:
- A04:2021-Insecure Design is a new category for 2021, focusing on risks concerning design flaws. Being in the pre-coding space, Insecure Design is at the core of software security problems. It should not be mistaken for the insecure implementation, which is related to the coding phase. OWASP recommends application developers leverage OWASP Software Assurance Maturity Model (SAMM) to help structure the secure software development efforts.
- A08:2021-Software and Data Integrity Failures is one of the highest impact categories focused on integrity flaws related to software updates, critical data, and CI/CD pipelines. Looking back at the software supply chain attacks and how malicious updates can deliver malicious payloads, this category made it to the Top 10 list this year. (See our Third-Party Data Breach page). The older A8:2017-Insecure Deserialization is now a part of this larger category.
- A10:2021-Server-Side Request Forgery is one of the two categories from the community survey (#1). It is in tenth place due to a relatively low incidence rate. This category represents the scenario where the security community members reported that this is important, even though it was not illustrated in the data.
The two most prominent upwards shifts are in the Broken Access Control and Vulnerable and Outdated Components categories:
- A01:2021-Broken Access Control moves up to the first position from the fifth position as the category with the most severe web application security risk. Users cannot behave outside of their intended permissions because of access control. Failures frequently result in unauthorized information disclosure, modification, or destruction of all data, as well as the execution of a business function outside the user’s capabilities. CWE-200: Exposure of Sensitive Information to an Unauthorized Actor, CWE-201: Exposure of Sensitive Information Through Sent Data, and CWE-352: Cross-Site Request Forgery. Are among the mapped CWEa
- A06:2021-Vulnerable and Outdated Components which had previously been titled “Using Components with Known Vulnerabilities,” came out as #2 in the Top 10 community survey. This category is closely related to timely software patching. Through 2020 and in 2021, organizations are dealing with unpatched components.
OWASP: A Standard or a Starting Point?
OWASP is a non-profit organization dedicated to improving software security. For more than two decades, it has proved a valuable source of information for developers and technologists, as well as provided valid documents regarded as de facto security standards among the software community.
Among this trove of information sources, the OWASP Top 10 comes out as a referential document for outlining the most critical software vulnerabilities for web applications. Although most companies regard OWASP Top 10 as a de facto standard, the OWASP community calls it an “awareness document,” refraining from its usage as a full coverage standard document. As covered below, some of the security vulnerabilities are not testable, making it hard to use as a standard document.
The OWASP Methodology & Black Kite
OWASP develops this list with input from hundreds of contributors, e.g., a team of security experts and security companies.
OWASP remained transparent about the data collection, processing, and risk scoring methodology in. OWASP published a call for data through social media channels, listing the data elements and structure they were looking for and how to submit them. An essential aspect of this work was mapping CWEs to the relevant risk categories.
OWASP retrieves data from organizations testing vendors by trade, bug bounty vendors, and organizations that contribute internal testing data. The data is loaded together and runs a fundamental analysis of what CWEs map to risk categories.
Similarly, Black Kite correlates and maps each control item to CWEs, making it easy to filter the controls by CWEs.
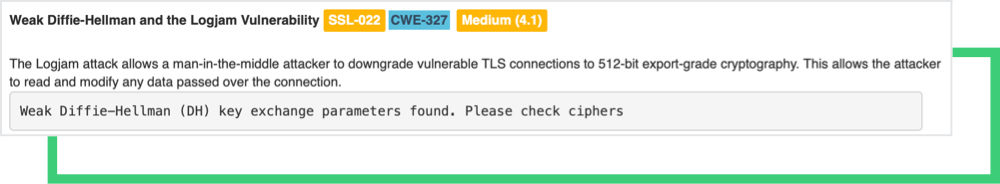
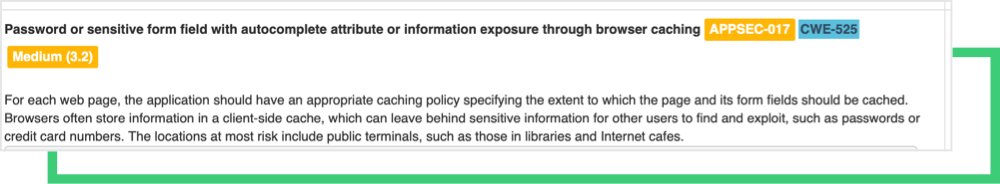
Black Kite’s cyber risk categories can be mapped to the Top 10 OWASP vulnerabilities, as shown below:
- Black Kite SSL/TLS Strength → OWASP Top 10 A02:Cryptographic Failures, A07:Identification, and Authentication Failures
- Black Kite Patch Management → OWASP Top 10 A06:Vulnerable and Outdated Components
- Black Kite Application Security → OWASP Top 10 A01:Broken Access Control, A05: Security Misconfiguration, A07:Identification and Authentication Failures
- BlackKite Network Security → OWASP Top 10 A05: Security Misconfiguration
Want to see our award-winning I’m risk management platform in action? Request a demo today.