The CIA Triad: A Key Part of Your Cyber Security Program
Written by: Black Kite
By Haley Williams, from the perspective of Bob Maley, CSO
In a society where data is being transferred constantly each day, it is imperative that fundamental objectives surrounding the security of that data are set in place.
What is the CIA Triad?
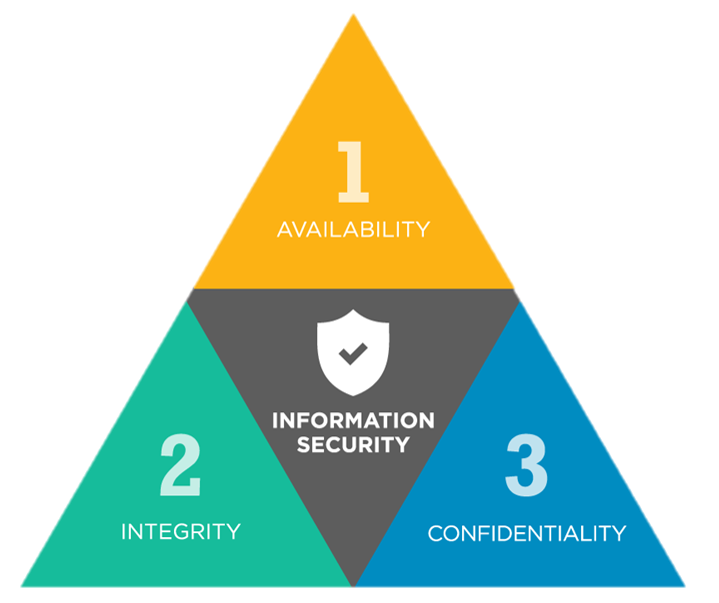
A model that has been trusted and developed over the last 50 years, the CIA Triad is comprised of three key components:
- Confidentiality
- Integrity
- Availability
In each instance of a data breach, phishing attempt, or other security incident against a company, it is guaranteed that one of the triad principles has been violated.
Confidentiality
Confidentiality refers to the efforts to keep data locked down. Data should only be accessed by authorized users and there should be barriers to prevent any unauthorized parties from gaining access to the data.
Because of this, it is reasonable for a customer of an organization to trust that their data, whether PII or e-commerce information, is actively protected from unauthorized and outside access.
Confidentiality can be infracted through direct measures, through a series of planned attacks, or capitalization of vulnerabilities. This was exemplified by the Log4j attack in late 2021, when sudden access and control to systems was granted due to exploiting a zero-day vulnerability. However, direct measures are not always the cause for a breach of confidentiality. Human error, poor security practices (or none at all) can lead to exposure of sensitive information in the blink of an eye.
As threat actors have gained agility and skill in jumping on exposed data, having a stringent security program for a company is imperative for keeping employees vigilant and aware of the risks and responsibilities they hold as a keeper of the data.
Three steps to better ensure confidentiality:
- Implement MFA
- Data Encryption
- Risk Assessments of Vendors
- Employee Education and Training
Integrity
The principle of Integrity refers to the guarantee that all data, information and systems are complete, untouched, whole and accurate. Violating integrity would mean that the data had been tampered with and altered in a way that nullified the authenticity and reliability.
In a world where both everyday data and sensitive data are trusted to cloud companies for storage, individuals must be able to trust that the data is remaining untouched and unaltered. Similar to confidentiality, integrity can be violated both intentionally by an outside (or internal) threat actor, or by accidental error and poor procedures.
Three steps to better ensure confidentiality:
- Digital Certificates
- Regular Systems Audits
- Automatic Update Requirements
Availability
Last but not least, availability refers to the accessibility of all platforms and data, and the guarantee that they will be up and running at all necessary times.
During the majority of ransomware attacks, until a ransom is paid or other methods of re-securing systems are used, data is locked down. One of the biggest losses companies face during ransomware attacks is downtime due to unavailable systems. This can cause a ripple effect of problems, like a drop in reputation and customer satisfaction.
Additionally, DDoS, or distributed denial-of-service attacks are one of the most common attacks primarily focused on reducing the performance of systems or taking a web-based service offline entirely.
Three steps to better ensure confidentiality:
- Software Patching Updates
- Backups of Systems
- Web Application Firewalls (WAF)
How Black Kite can help
Maintaining a perfect information security program using the CIA Triad is a continuous and difficult task to master. We believe that Black Kite’s program is one giant step in the right direction as a tool to start making sure your systems and data, whether that data is in your hands or in the hands of a vendor, is secure and available.
At Black Kite, we often talk about how important it is to maintain a strong defense strategy against your cyber and third-party risks. Merely putting a checkmark next to a technical cyber rating is not sufficient. A more holistic approach to your vendor risk management program is worth the investment, especially when you have a tool that automates previously manual efforts.
Security teams using spreadsheets and frustrating software cannot keep up with the hundreds or thousands of vendors holding an organization’s invaluable data. Cyber criminals know that. They also know the false sense of security cyber rating can provide for an organization.
With more companies outsourcing aspects of their business and relying on suppliers and partners, understanding third party risks above and below the surface is a must-have rather than a nice-to-have. Between vetting new vendors and keeping track of existing suppliers, vendors and partners, third-party vendor risk management is difficult to stay on top of and can be very time consuming.
Let Black Kite’s automated platform do the heavy lifting for you.
Schedule a Demo Today
