5 Ways Automation is Revolutionizing Third Party Risk Management
Written by: Black Kite
5 Reasons to Automate Third-Party Risk Assessments
Your threat landscape is an ever-changing environment. Your cyber risk exposure today may not be the same tomorrow. The integration between your company, its sensitive data and your vendors is at an all-time high, and every second counts when it comes to understanding critical vulnerabilities throughout your digital environment. In light of this, we know that the future of third-party cyber risk management is streamlined, automated, and verifiably continuous. Here’s why.
1. Automation shortens the risk assessment process from weeks to minutes.
The average time between an attack and the disclosure date was 75 days in 2021, with many incidents taking up to 200 days for disclosure. In a world where breaches seem to come out of nowhere, this kind of delay is unacceptable. Reactive approaches to fighting risk promote a behavior that can only act after an incident, rather than proactively build defenses before.
With an automated tool that can streamline your digital supply chain’s assessments, you can have a platform, like Black Kite, up and running in a day’s time. Compared to the old way of monitoring, which includes spreadsheets, manual assessments and grades, and intense manpower, automated rating platforms cut all of that down. Manpower can be reallocated (which is extremely important with today’s employee shortages), funds can be reallocated, and months of legwork can be removed from the equation.
Not only is the set up fast and simple, so is the assessment itself. Each vendor’s full assessment includes ratings, ransomware susceptibility, quantified risk, and compliance standings – with a continuous look at the status. As we’ve seen over the past few years, point-in-time monitoring is outdated and unrepresentative. While it might be the only feasible solution for a manual process, automation removes the impossibility of having full visibility at all times.
So what are the goals of robust risk management? Decrease in business disruption, protection of data, and low probable quantified risk.
2. Automated risk analysis is more accurate than manpowered assessments.
According to IBM, human error accounts for 95% of information security errors. In an automated third party risk management process, removing the manual aspect removes this high risk of human error. Instead, vendors that pose the largest risk to your company are brought to the surface, and teams can spend their time tackling the improvements that need to be made based on trustworthy cyber intelligence.
The most trustworthy assessments and intelligence are backed by the world’s standards, such as NIST, MITRE, Open FAIR™, and SharedAssessments. Here at Black Kite, we follow and apply commonly-used frameworks developed by the MITRE Corporation to calculate ratings in a consistent, flexible, and transparent manner. In an automated platform, each threat within a vendor’s report can be quickly and easily compared against these standards to confirm its criticality.
3. Automation prioritizes threats by criticality level, freeing up your resources.
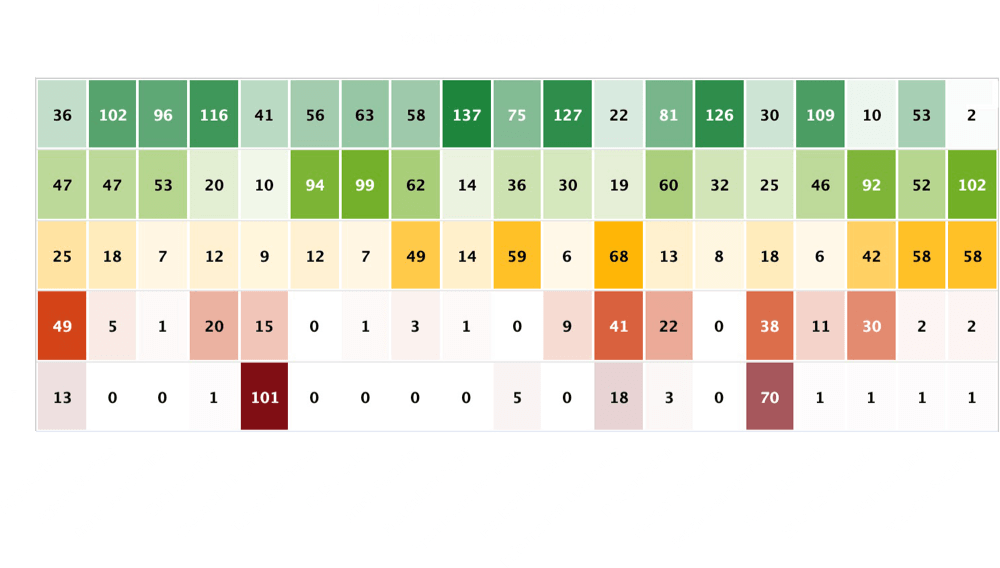
A pain point of non-automated monitoring is often data overload. Once the time is put in to gather all of the data on the vendors in your cyber ecosystem, what do you do with it? In an automated platform like Black Kite, threats and tasks can be prioritized based on criticality level, and using a strategy report, the proper action steps can be taken.
No more need for time-consuming and inefficient searching for what steps to take based on an ambiguous score. Taking it one step further, Black Kite is the only cyber risk monitoring platform with a strategy report that includes remediation for compliance and financial impact.
4. Automated platforms provide visibility and by accessing large data sets.
An automated platform can inevitably access thousands if not millions of additional data sources than a human resource ever could, not to mention hours saved in the process. Those hundreds of hours only grasp a small percentage of the raw data that AI can handle and parse through. If you look at the Black Kite platform, our non-intrusive, powerful scans tap our data lake of OSINT data, accessing information from 1000+ resources on 34 million companies, 4x the competition. We also access, in minutes:
- 400M Domain Names
- 4B Subdomains
- 4B Service Fingerprints
- 10B SSL Certificates
- 100B DNS & Whois
- 100B Web Pages
5. Scalability of vendor ecosystem
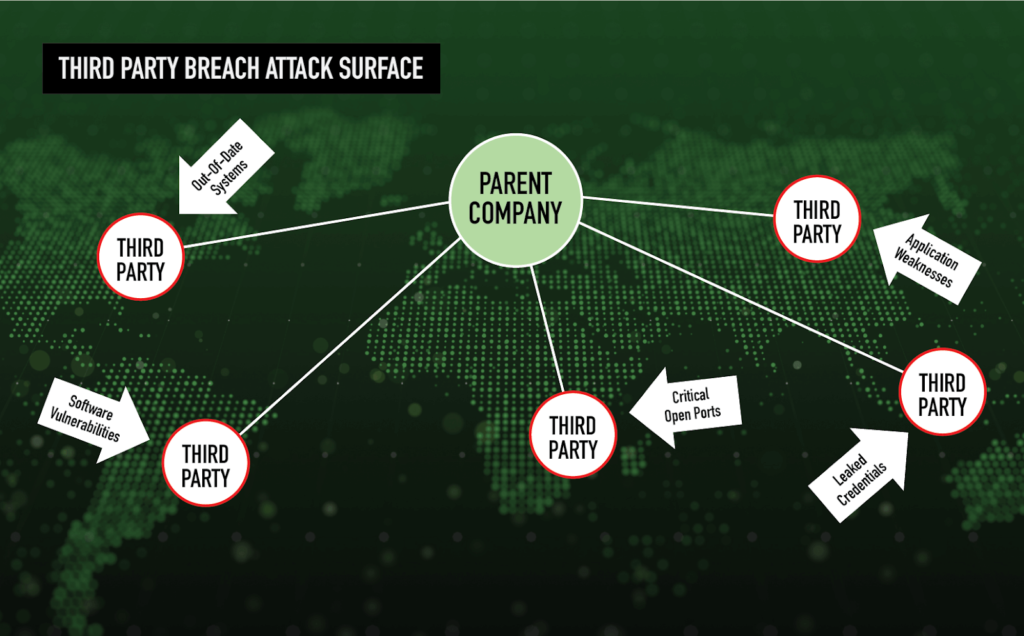
As your digital supply chain grows, and as compliance requirements change, there is an extreme need for adaptability and flexibility. Without automation, suddenly you are benchmarking your compliance verification against outdated controls – or forgetting about that vendor you signed on yesterday to manage your sensitive data. You have too much at stake not to be proactively aware of your cyber health. At Black Kite, you can scale your vendor ecosystem effortlessly in the platform, adding or subtracting companies as necessary.
Your Path to Automated Vendor Risk Management
Part of your journey towards scalable reliable monitoring is getting started and gaining visibility on that very first third party and using an automated risk management tool for yourself. There is so much to be discovered about your vendor ecosystem – findings that can be revealed as quickly as the duration of your lunch break. Let us take it a step further, and give you a free look at your first five vendors of choice.
In minutes, you can have a full vendor risk assessment of your selection of companies, which includes:
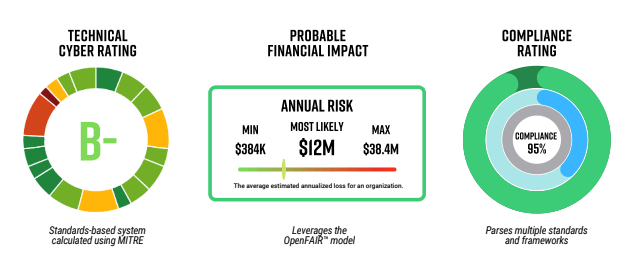
- Technical letter grades that provide easy-to-understand ratings calculated using MITRE standards against 20 powerful, contextual categories.
- Financial impact analysis using Open FAIR™ to measure the probable financial impact in the event of a breach.
- Compliance ratings that calculate the level of compliance with regulations such as CMMC, GDPR, PCI-DSS, and HIPAA.
- Ransomware Susceptibility Index™ ratings that determine the probability of a ransomware attack against each vendor using key indicators and ransomware controls.

