Ciox Health breach impacts 30+ institutions: Why does healthcare continue to be targeted in 2022?
Written by: Black Kite
A data breach aimed at Ciox Health this summer was recently disclosed to the patients of Ciox’s providers this January: 6 months later. The disclosure announced that an employee’s email account was compromised between June 24 and July 2, 2021. Ciox Health is a clinical data technology vendor working directly with many healthcare institutions across the United States.
Once again – eyes are turned towards the healthcare sector. Why is it such a common target for cybercriminals? What did the third-party attacks of 2021 tell us about how threat actors find their way into different healthcare organizations? With the growing cybersecurity challenges of 2022, is there a way to increase the healthcare sector’s immunity to such attacks?
Timeline of the Ciox Health Breach
- A Ciox employee’s email account was compromised and accessed between June 24 and July 2, 2021.
- On September 24, Ciox determined that the emails and attachments contained patient information relating to the billing inquiry.
- Ciox began working with its customers to notify impacted patients on December 30, 2021.
- Patients were notified in early January 2022.
The Ciox Health breach disclosure hits 6 months later: What happened?
On September 24, Ciox Health determined that the compromised email account allowed access and downloads of emails and attachments containing patient and billing information from the account. The information included names, dates of birth, providers, history of service, Social Security numbers, driver’s license numbers, insurance information, medical records and treatment details.
They began notifying the customers of the healthcare providers about the incident in November and December. However, the healthcare beneficiaries waited until the last week of January 2022 to inform their impacted patients.
Some of the affected healthcare organizations in the digital supply chain of Ciox were:
- AdventHealth – Orlando
- Baptist Memorial Health Care
- Butler Health Systems
- Cameron Memorial Community Hospital
- Centra Health
- Copley Hospital
- DeSoto Memorial Hospital Health System
- EvergreenHealth
- Hoag Health System
- Huntsville Hospital Health System
- Northwestern Medicine
- Ohio State University Health System
- OrthoConnecticut
- Prisma Health – Greenville Health System
- Sarasota County Public Hospital District
- Trinity Health
- Union Hospital Healthcare System
Ciox claims that they continued to collaborate with their clients to facilitate the communication to the impacted patients, and no theft or tangible evidence of fraud was discovered due to the delay. But as you can see, communication tends to delay significantly between each party down the line.
As a post-breach response, Ciox claimed within the warning issued on their website that they will work to improve their cybersecurity training measures for staff, as well as strengthen email security.
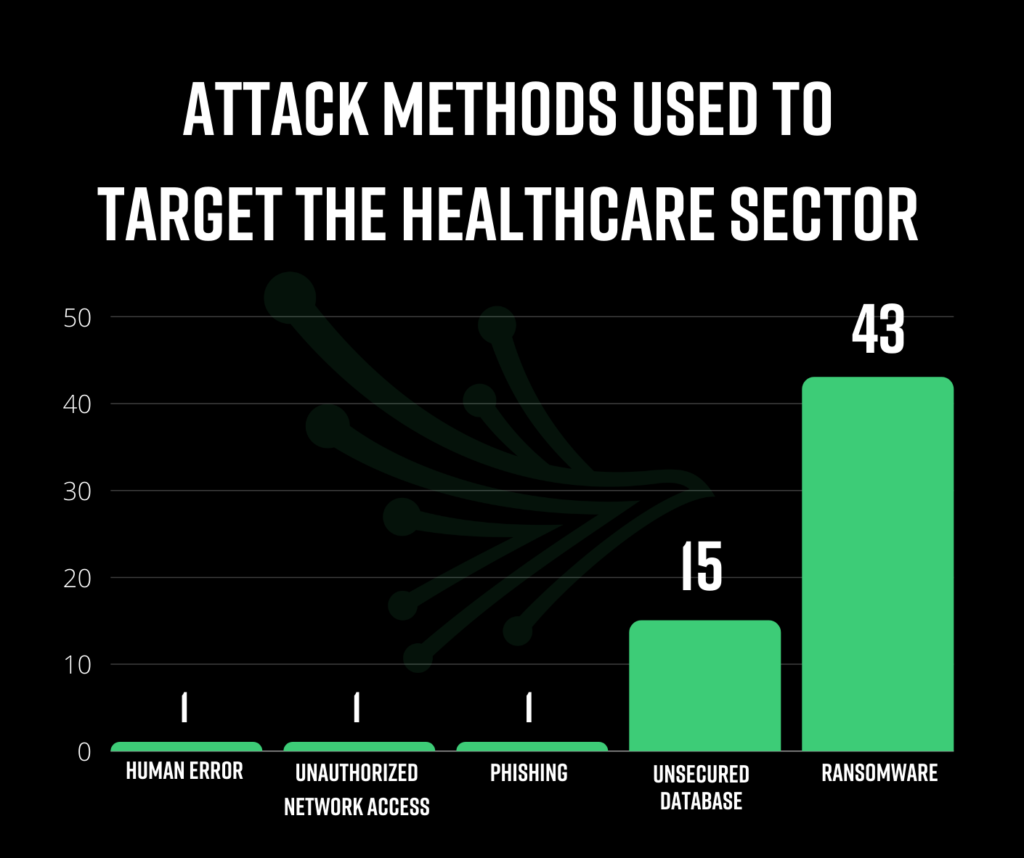
What attack methods are being used to target healthcare?
Ransomware was the most frequent attack method on the hunt for PHI data in 2021, accounting for 43 of the 51 headline breaches. When ransomware is the method of attack, the continuity of life-critical operations are threatened, as well as the privacy of individuals. As long as threat actors see this attack method as the quickest way to monetize data, we will continue to observe heightened ransomware attacks on healthcare institutions.
Unsecured servers and databases accounted for 15 of the studied breaches. Companies with large amounts of PHI are at higher risk for this attack method. Our studies confirm that the boundaries are blurred when third parties begin to manage such sensitive patient data. Often, companies served by the database/server vendor take the false sense of security for granted, forgetting to monitor these vendors until it’s too late.
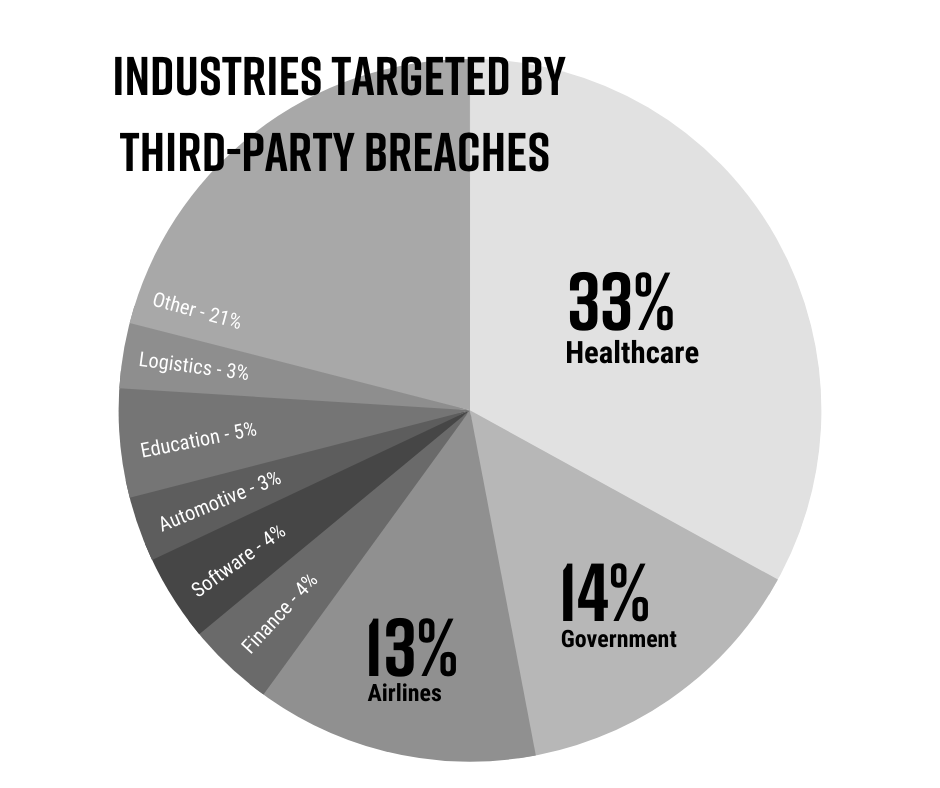
The Black Kite Third-Party Breach Report 2022 tells us that 33% of headline third-party breaches last year were aimed directly at the healthcare industry.
What makes healthcare such a susceptible target is both the value of PHI data and the characteristics of the industry’s workers. In the healthcare industry, doctors and nurses are constantly moving from workstation to workstation, each with varied system privileges. This makes safeguarding data and computer systems difficult and inconsistent. To add to that, often outdated software opens up hundreds of access points for threat actors to infiltrate and gain access to a company’s data.
The nature of PII and PHI data, plus the criticality of operations, raises the stakes in healthcare. PHI is more valuable sold on the black market and can often be offered for higher ransomware demands.
Disclosure times: Why 74 days vs. 100 days matters
According to the Black Kite report, the average time elapsed between an attack and the disclosure date in 2021 was 74 days. This data is based on third-party breaches that were transparent about the who, what, and when of the attacks. 44% of the affected companies were above this average time lapse value.
When it comes to healthcare data breaches, the time lapsed was much higher – reaching 100 days on average. The Ciox email incident is an example of a late disclosure and release of information – taking 6 months.
What can you do to stay as agile as the adversary and improve security posture?
Our study tells us that attempts to manage third-party cyber risk in a meaningful way are being often thwarted by the complexity of vendor ecosystems and the fast-changing threat landscape. Lack of resources and continued reliance on manual, point-in-time operations clouds visibility of the vast and varied makeup of the digital supply chain.
- Stick to a Business Associate Agreement.
Ensure that each third party who has access to an electronic system has signed a Business Associate Agreement. The HIPAA Final Rule mandates the use of such an agreement. - Erase hard drives when the owner changes.
Only transfer end-point devices to other staff after erasing any existing/remaining data from the hard drive. In many cases, especially in healthcare, IT teams are understaffed, untrained, and have not taken the time to examine all asset distribution or management processes. Wiping all endpoint devices before provisioning them to another person should be an industry standard to ensure HIPAA compliance and PHI data protection. - Encrypt the data on any hard drive.
With so many data breaches, the necessity of encryption goes nearly without saying. - PHI should not leave the protected network.
Any endpoint with the capacity to leave the building falls under this category. Healthcare organizations should evaluate their current practices that allow PHI to be saved to hard drives, mobile devices, and similar devices. By removing PHI from devices that leave the protected environment, the danger of data theft and compromise, and hence the chance of a data loss incident, are reduced significantly. - Assess third-party risk.
Vendor risk assessments are becoming more prevalent nowadays. When compared to historical levels of third-party suppliers in healthcare, engaging with third parties at an exponential rate is a key component of the digital healthcare ecosystem. When you add more vendors to the ecosystem, you have to look at the risk environment.
Additional Resources
1. CISA’s advisory on ransomware
a. A generalized, sector-free set of best practices and recommendations from CISA. Therefore any sector, including healthcare, can adapt this set of control items to increase its cyber security maturity and immunity to ransomware attacks.
- Preventing the ransomware attack,
- Protecting sensitive and personal information, and
- Responding to ransomware-driven data breaches.

