Devil in the Details: How to Address Third-Party Risks
Written by: Black Kite
Imagine that you are prospecting a new IT vendor and you are using a security ratings service to vet their overall cyber risk posture. The resulting “B” rating is considered “Good” in the space, so you move ahead with the relationship and begin sharing data with this company. Two weeks later, you discover that this vendor has suffered a ransomware attack and your sensitive data is compromised. What happened? How was this missed? This scenario is all too familiar.
Vendor risk assessments are vital to starting and maintaining relationships with third-party companies. If you spend even a few minutes reading the news from the last twelve months, you’ll quickly see that big name corporations often fall victim to cyber attacks because of smaller, more easily-targeted organizations.
Gaps in Vendor Risk Management
In our 2022 Third Party Breach Report, we conclude with a discussion on gaps in vendor risk management. The industry’s default focus on compliance checklists results in a static approach to cyber risk rather than a dynamic approach.
Let’s take a look at how to be dynamic in the Technology space. Black Kite Research analyzed the top 250 technology vendors to uncover the industry’s cyber risk posture and potential areas of concern.
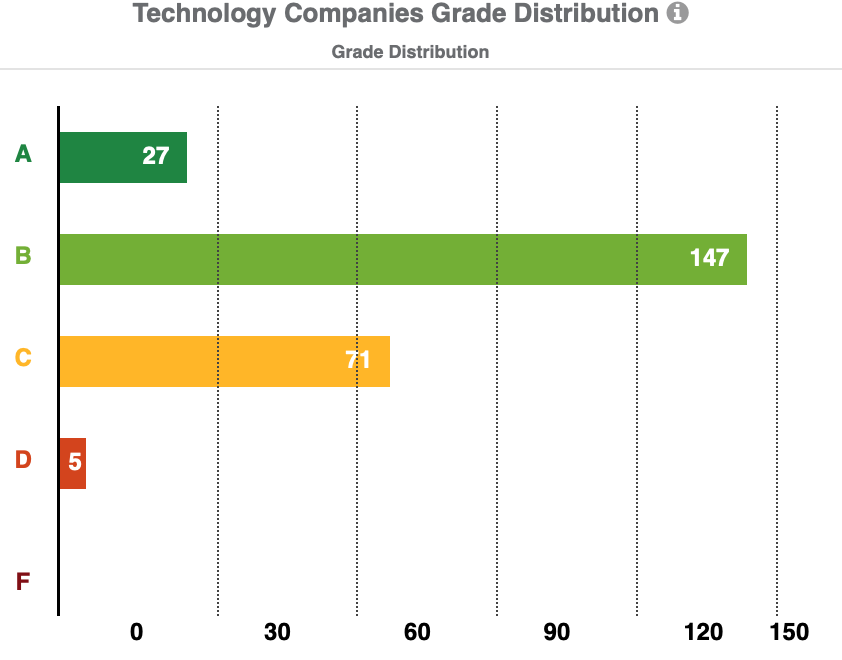
Technology vendors have a “Good” technical rating of 82 (Grade B). 27 vendors have an A-grade, 147 have a B-grade, and 71 vendors have a C-grade. Technology vendors have an average Ransomware Susceptibility Index™ rating of 0.27.

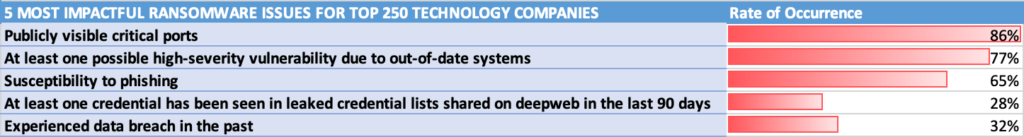
While this RSI™ rating isn’t above the critical threshold of 0.6, ransomware risk still exists across the technology sector. The five most critical ransomware susceptibility indicators for technology companies are:
- Publicly visible critical ports (86% of vendors)
- At least one high-severity vulnerability due to out-of-date systems. (77% of vendors)
- Susceptibility to phishing (65% of vendors)
- At least one leaked credential on the deep web in the last 90 days (28% of vendors)
- Experienced data breach in the past (32% of vendors)
66% of tech companies have at least one possible critical vulnerability due to out-of-date systems. Out-of-date systems are an obvious, but often overlooked issue that creates access points for hackers to exploit. Consider the recent and ongoing Log4j incident of 2021.
Due to the zero-day vulnerability, ANY Java-based system running on the out-dated Log4j versions susceptible to the vulnerability became a sitting duck to RCE from cyber criminals. Users had to update (and continue to update as the incident progressed) in order to combat the risk. More often than not, seemingly simple updates that slip through the cracks allow for detrimental breach opportunities.
96% of the top 250 technology companies have an invalid or expired SSL Certificate. Leaving an expired certificate live prevents a secure connection to the server from being established. 90% of these companies have leaked credentials, which is easy and free access to gain access to company data and platforms.
Maintain a robust monitoring process
For tech companies, according to Institute for Internal Auditors (IIA) (OnRisk 2021: A Guide to Understanding, Aligning, and Optimizing Risk,) the two biggest risks faced in 2021 were cyber security as a whole and third party risk management. Even with investments in security tools and working to maintain a strong cyber posture, the threat of breaches continues to remain high.
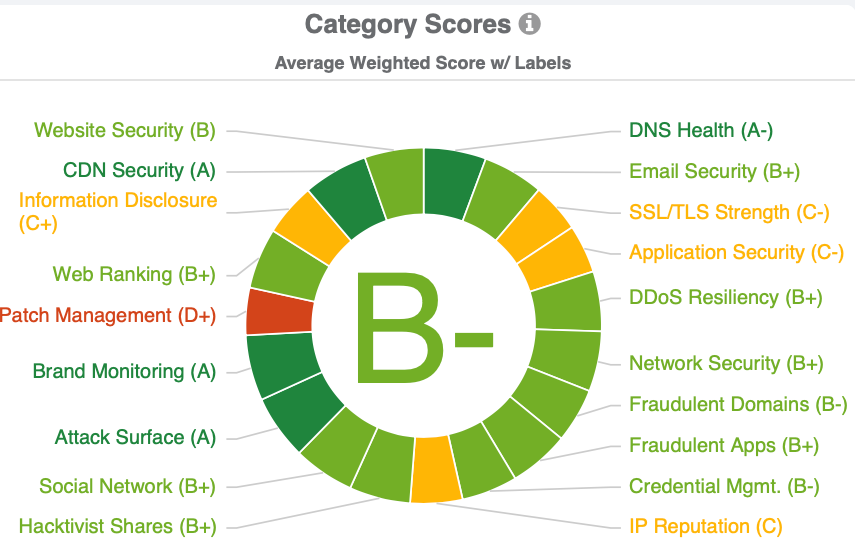
As mentioned, checklists do not satisfy the need for being dynamic in an approach to cyber risk. In the technical category breakdown within the Black Kite platform, Patch Management stands out at a D+ across companies in the technology sector. Application Security, SSL Strength, and Information Disclosure follow closely behind in the C-range.
Each month, hundreds of vulnerabilities are published. Without a robust patch management program, that opens up hundreds of avenues for cyber criminals to gain access to a vendor, and therefore gain access to sensitive data. While the bird’s eye view shows a decent cyber rating, the weeds reveal a massive opportunity for bugs, CVE codes, and severities to thrive.
As we’ve elaborated on in other blogs and reports, more than 50% of common security vulnerabilities exploited by criminals are over a year old. IT teams become overwhelmed and miss critical updates. Lazy patch management protocol allows for immediate exploitation in each instance of outdated software staying outdated.
Learn more about practicing strong patch management.
What we learned from ransomware in 2021
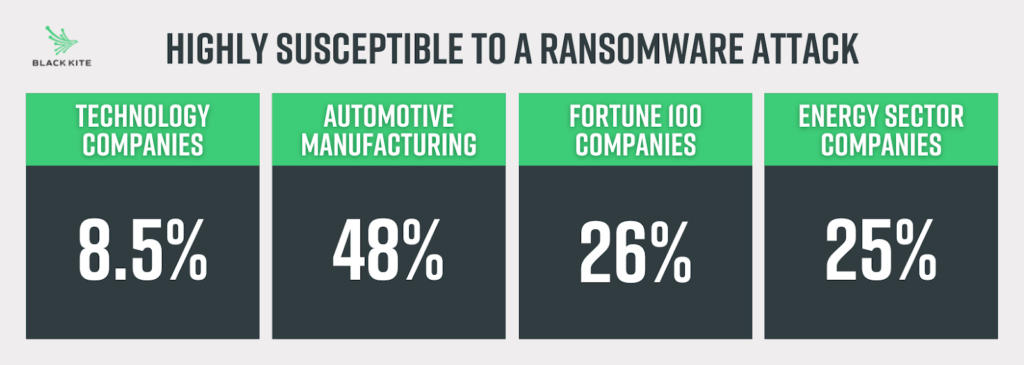
Ransomware accounted for 27% of the breaches in 2021 according to our 2022 Third Party Breach Report. And while the average RSI (Ransomware Susceptibility Index) for tech companies was .27, 28% of the technology companies are still above the average, with 8.5% above the critical threshold of .6.
To benchmark against other analyzed industries, you can see that Technology companies actually compare quite well to the Automotive, Fortune 100 and Energy industries, with only 8.5% being highly susceptible to a ransomware attack.
Use these cyber risk details to your advantage
At Black Kite, we often talk about how important it is to maintain a strong defense strategy against your cyber and third-party risks. Merely putting a checkmark next to a technical cyber rating is not sufficient. A more holistic approach to your vendor risk management program is worth the investment, especially when you have a tool that automates previously manual efforts.
Security teams using spreadsheets and frustrating software cannot keep up with the hundreds or thousands of vendors holding an organization’s invaluable data. Cyber criminals know that. They also know the false sense of security cyber rating can provide for an organization.
With more companies outsourcing aspects of their business and relying on suppliers and partners, understanding third party risks above and below the surface is a must-have and not just a nice-to-have. Between vetting new vendors and keeping track of existing suppliers, vendors and partners, third-party vendor risk management is difficult to stay on top of and can be very time consuming. Let Black Kite’s automated platform do the heavy lifting for you.

