Supply Chain Cyber Risk are Finally Part of the NIST Cybersecurity Framework!
Written by: Black Kite
Recently, National Institute of Standards and Technology (NIST) released new version of its Cybersecurity Framework (v. 1.1), which includes several additions such as cyber risk originated from supply chains.
The version 1.1 is a risk-based framework to improve cybersecurity of critical infrastructure in the US. However, it is used by many companies as a guideline to assess their cyber risk and some public or private institutions are looking for compliance to this framework.

A new section called Section 4.0: Self-Assessing Cybersecurity Risk describes how the framework can be used to assess cyber risk by using certain measurements. Supply-chain attacks are one of the key parameters on cyber-risk assessment.
What is Supply-Chain Attack?

Supply-chain attacks (aka value-chain attacks or third-party attacks) are attacks originated from one of your third parties that has access to your system, which includes data management companies, law firms, e-mail providers, web hosting companies, subsidiaries, vendors, subcontractors, any external software or hardware used in your system (even the javascripts added to your website to collect analytics) and list goes on. These are usually the weaker links to access to your system. A recent study conducted by Ponemon Institute shows that 56% of the companies have experienced a 3rd-party breach in 2017.
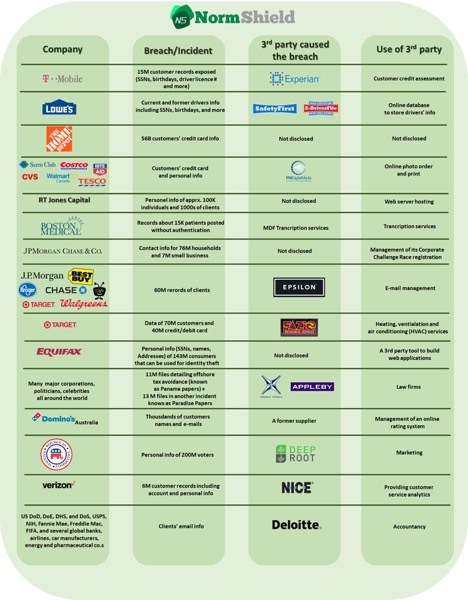
Supply-Chain attacks are on the rise
Some of the major breaches caused by supply-chain attacks are shown in the figure below. The consequences of those breaches cost hundreds of million dollars to the companies. As seen from the figure, the attacks may even come from an HVAC system. Even IoT devices in a company can be source of a breach. Very recently a casino was hacked through its Internet-connected thermometer in an aquarium in the lobby. Some supply-chain attacks come from the software used. Some major software supply-chain attacks in 2017 are listed below.
- An open-source video conversion tool for MacOS, called Handbrake, hacked. Hackers created a backdoor through Handbrake to disseminate a remote access toolkit, Proton.
- A popular Ukrainian software updating its products helped spreading a ransomware called XData in May 2017. In June, another ransomware called NotPetya used the same method.
- In August, NetSarang products were abusively used by attackers to deliver a malicious code to their customers through a backdoor inserted by hackers. This attack, called ShadowPad, exploited a date-based Domain Generating Algorithm (DGA).
- In September, another date-based DGA-using attack performed with a backdoor inserted in CCleaner, an ad-removal tool.
What NIST says about supply chain cyber risk?
The Section 3.3 of NIST updated cybersecurity framework defines the supply chain as follows;
Supply chains are complex, globally distributed, and interconnected sets of resources and processes between multiple levels of organizations. Supply chains begin with the sourcing of products and services and extend from the design, development, manufacturing, processing, handling, and delivery of products and services to the end user. Given these complex and interconnected relationships, supply chain risk management (SCRM) is a critical organizational function.
Further in the Section, cyber SCRM is described in a full-duplex manner with cybersecurity effect an organization [that] has on external parties and the cybersecurity effect [that] external parties have on an organization.

Source: NIST Cybersecurity Framework v1.1
NIST also lists following cyber SCRM activities;
- Determining cybersecurity requirements for suppliers,
- Enacting cybersecurity requirements through formal agreement (e.g., contracts),
- Communicating to suppliers how those cybersecurity requirements will be verified and validated,
- Verifying that cybersecurity requirements are met through a variety of assessment methodologies, and
- Governing and managing the above activities.
Learn your supply-chain risk before it’s too late

Supply-chain risks are usually invisible to companies and the discovery of those risks requires gathering data of your third parties and providing a risk assessment. With NIST new cybersecurity framework, companies would be more aware of supply-chain attacks. However, self-assessment of supply-chain risk is very challenging. Using services such as Black Kite Cyber Risk Scorecard would ease the activities listed by NIST Framework. Learn your cyber risk score, create your ecosystem, and discover your supply-chain risk before it is too late. To schedule a demo, visit https://www.blackkite.com/request-a-demo/