THE SOLARWINDS ATTACK FROM A HACKER’S POINT OF VIEW
The attack SolarWinds is a perfect demonstration of a critical caveat in cyber risk management: Organizations can only uncover the information they’re looking for.
Companies are so busy locking down their own house doors, they ignore the tunnels accessible via third parties. Although 79% of firms have a third-party risk management (TPRM) program, most practitioners only focus on moderate and highly critical vendors.
Attackers know this all too well. They use advanced techniques to get in, cover their tracks, and create a new backdoor. At that point, it’s already too late. As was the case with the SolarWinds breach, they gain access into larger organizations through their weaker links.
While doubtful it could have been prevented, the SolarWinds attack could have been detected by looking for signals the hacker community capitalizes on.
SIGNALS THAT WENT UNDER THE RADAR
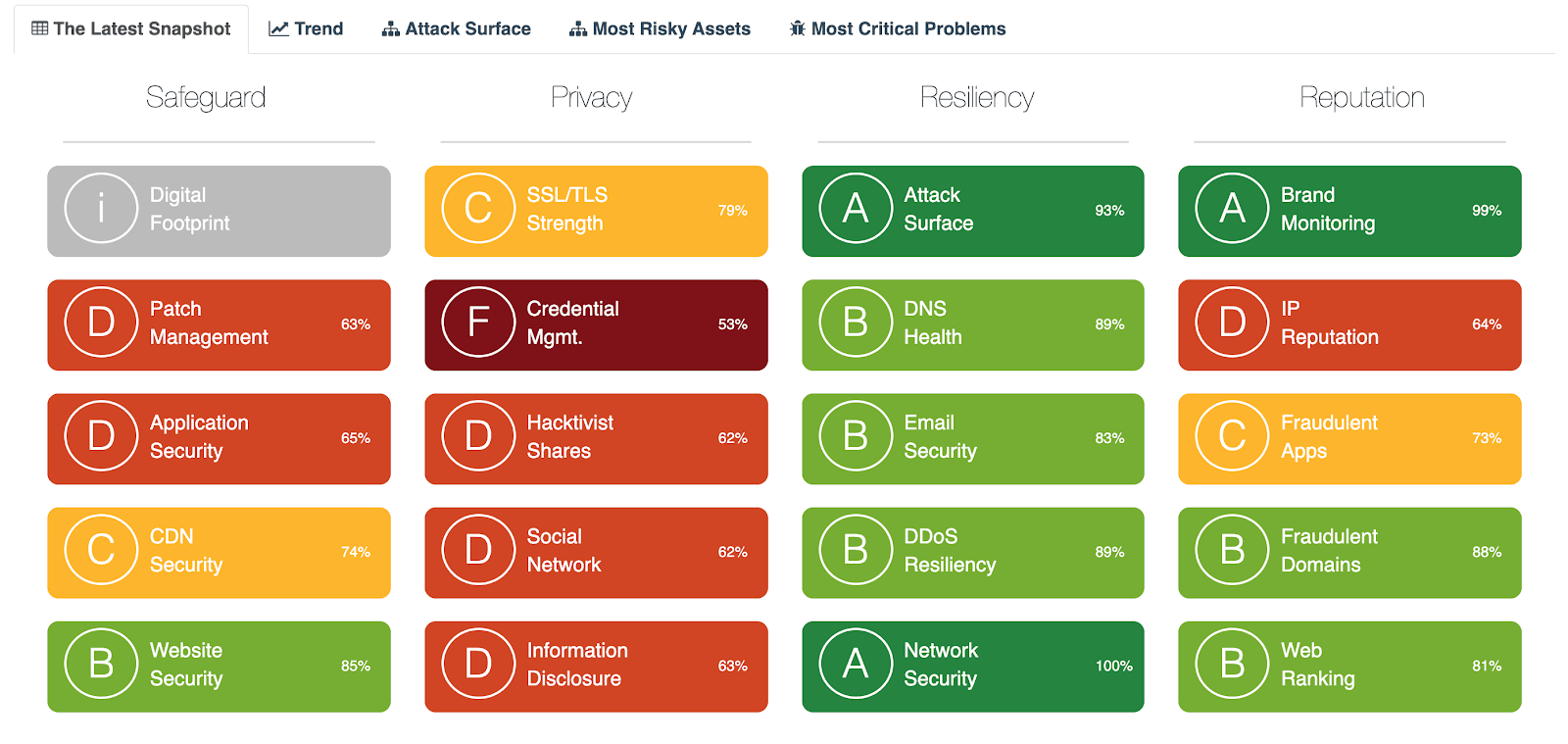
Reconnaissance, one of the top two elements of the MITRE ATT&CK®Matrix for Enterprise Reconnaissance and Resource Development, includes active scanning, gathering victim host information, and other data that might be notable for further analysis.
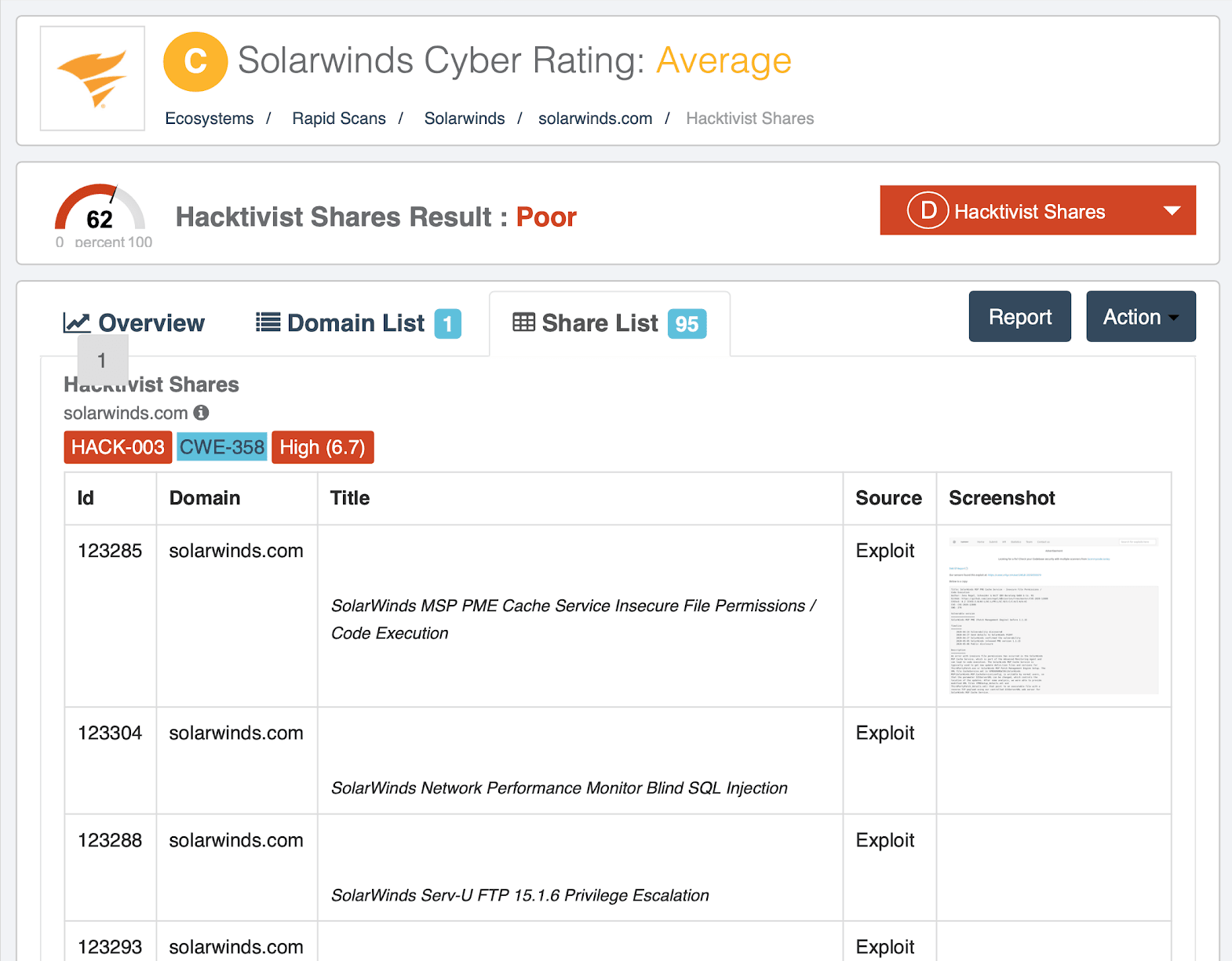
Identified through Black Kite scanning, we revealed three types of reconnaissance data which dated all the way back to 2018:
- SDLC Hacker Share Results show multiple exploits, including SQL injection.
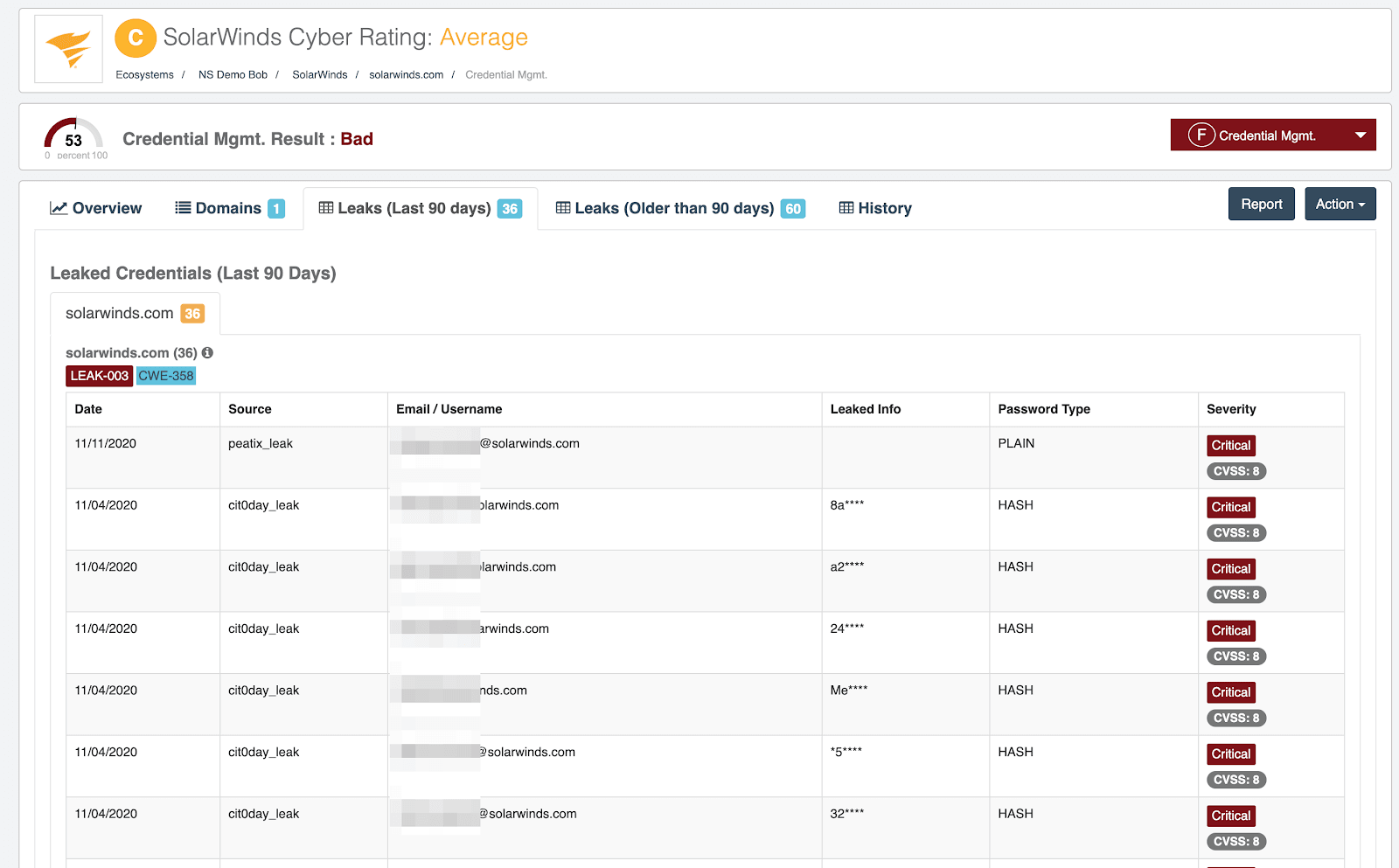
- Credential Management reported as deficient.
- Related domains purchased by hackers were registered mostly by China.
LETTER SCORES ARE NOT SIGNALS
There is no magic bullet. Just as a poor cyber hygiene score is not an indicator a company has been hacked, an ‘acceptable’ score does not mean the red flags aren’t there. At first glance, SolarWinds’ cyber hygiene wouldn’t necessarily call for immediate action. However, given their full access to an outsourcer’s network, SolarWinds is an extreme vendor from a risk viewpoint. Human analysis and intervention is key to getting healthy, preventative, detective information and using it proactively to support solid processes.
Understanding your landscape—which includes the extent of your partner ecosystem, business and incident response capabilities—will help you quickly identify and reduce the potential impact of a cyber attack.
Companies should bring forth a much deeper level of analysis and a more agile response. Integrating the right risk mitigation tools that account for real-world potential impact is essential. Just as importantly, choosing the right companies to examine closely is key. Without that view, insights simply become noise.
CLEAR THE NOISE
Built from a hacker’s perspective, Black Kite combines three types of assessments to holistically assess third-party risk from a technical, financial, and compliance perspective.