Urgent Citrix NetScaler Zero-Day Vulnerability: How to Protect your Digital Ecosystem
As we are all consistently reminded, zero-day vulnerabilities exploited in the wild wreak havoc on companies with weaknesses in their supply chain. The latest is CVE-2023-3519, a critical vulnerability affecting any company using the associated Citrix NetScaler products at risk (Citrix NetScaler ADC or NetScaler Gateway.)
This vulnerability is known to be currently actively exploited by threat actors, and is marked with a Base Score of 9.8 Critical by NIST.
What is the CVE-2023-3519 Vulnerability and its Potential Impact?
CVE-2023-3519 is a zero-day, unauthenticated remote code execution vulnerability. This kind of vulnerability allows an unauthenticated attacker to remotely execute arbitrary code on a vulnerable server, especially when appliances function as gateways or authentication virtual servers. For the vulnerability to be exploited, the vulnerable appliance needs to be set up as either a gateway or an authentication virtual server.
At this time, no public proof of concept (PoC) has been released, though there are claims by Citrix noting that the vulnerability is indeed being exploited at this time.
**There’s speculation that this vulnerability might be linked to a zero-day exploit offered on a hacker forum earlier in July. This zero-day was said to work for Citrix ADC versions up to 13.1 build 48.47.
Vulnerabilities like this can provide the initial access needed for threat actors to conduct future ransomware attacks on weakened organizations. Discover which industries are most frequently targeted in our latest Ransomware Threat Landscape Report.
What are the first steps organizations should take?
Given the widespread nature of this security issue, Citrix has advised an immediate update to the newly released versions. It would be prudent for organizations to conduct checks for signs of unauthorized access, like new web shells and unusual HTTP error logs.
Citrix has observed exploits of this vulnerability and is strongly recommending its customers to update their systems to the following versions:
- NetScaler ADC and NetScaler Gateway 13.1 before 13.1-49.13
- NetScaler ADC and NetScaler Gateway 13.0 before 13.0-91.13
- NetScaler ADC 13.1-FIPS before 13.1-37.159
- NetScaler ADC 12.1-FIPS before 12.1-55.297
- NetScaler ADC 12.1-NDcPP before 12.1-55.297
Citrix also mentioned that version 12.1 of NetScaler ADC and Gateway has reached its end-of-life, prompting users to switch to newer product versions.
**The Citrix notice only applies to customer-managed NetScaler ADC and NetScaler Gateway. Customers using Citrix-managed cloud services or Citrix-managed Adaptive Authentication do not need to take any action.
To detect potential compromise, organizations can look for newer web shells than the last installation date, check HTTP error logs for unusual patterns, and monitor shell logs for uncommon commands.
Apart from the main vulnerability, the updates also resolve two other vulnerabilities:
- CVE-2023-3466, a reflected XSS issue with a severity score of 8.3.
- CVE-2023-3467, which lets an attacker escalate privileges to root administrator level, with a severity score of 8.
Technical details about these vulnerabilities are not public yet, but organizations using the affected Citrix products are advised to prioritize their updates.
The Third-Party Cyber Risk Due to CVE-2023-3519
The CVE-2023-3519 vulnerability is particularly concerning from a third-party risk management (TPRM) perspective. A widespread use of both Citrix NetScaler ADC and NetScaler Gateway indicate a substantial potential risk within your vendor ecosystem. A single unpatched vulnerability could be an entry point for threat actors into not only the affected company but also the businesses associated with it, including your own.
Given the scale and severity of this issue, it is crucial for organizations to adopt a proactive stance to safeguard their operations and ensure the security of their vendor ecosystem. But how can you ascertain which of your vendors might be using these products? Let’s explore this in the next section.
How Can You Identify Vendors Using the Vulnerable Products?
Identifying which of your vendors are using potentially vulnerable products is a crucial step in managing this risk. Here, in-platform capabilities like those provided by Black Kite (FocusTags™) can greatly facilitate this process.
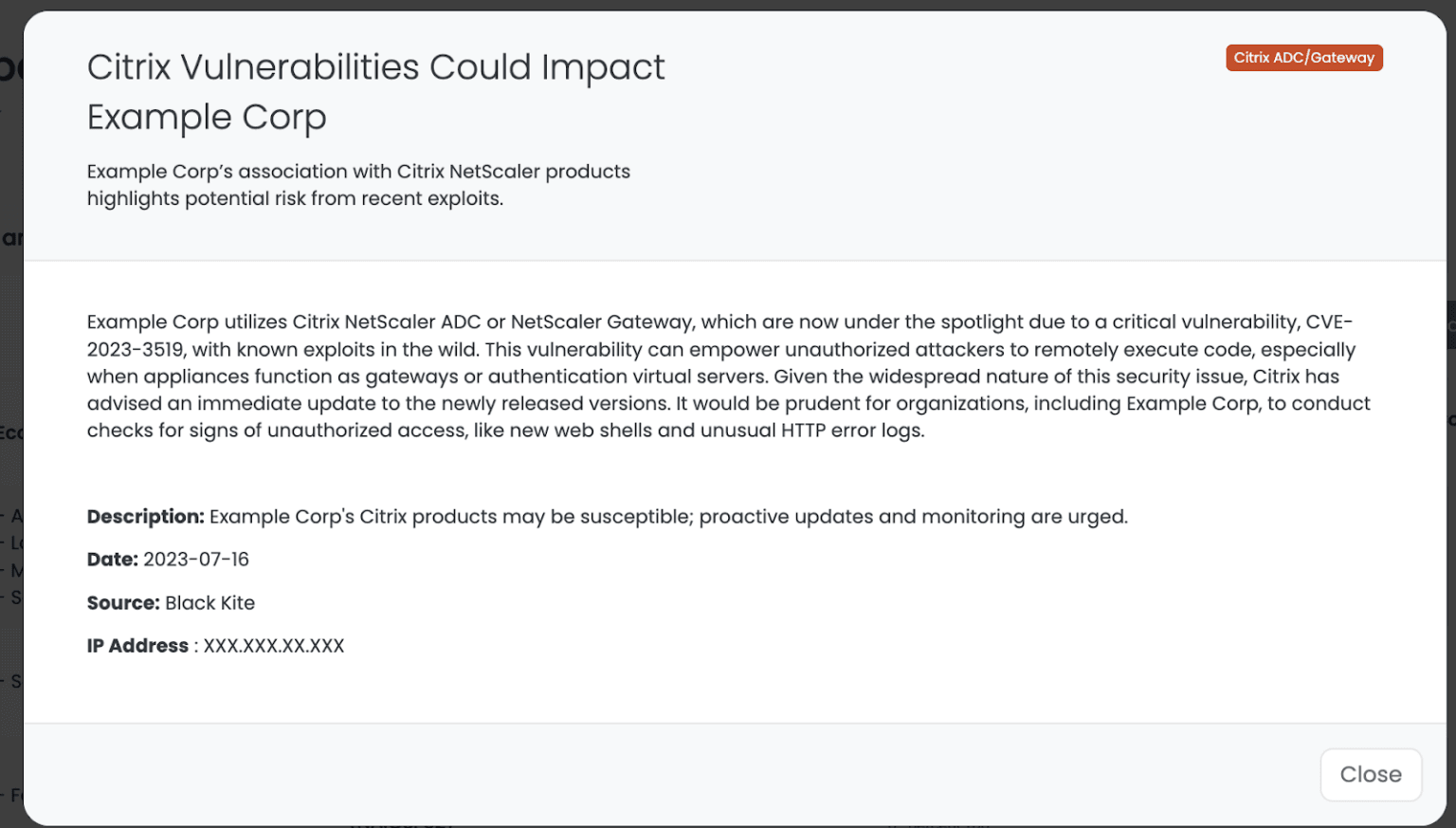
Black Kite customers have the ability to filter vendors using vulnerable servers via the Tag filtering feature found on the Company List page. Below is a step-by-step guide on how to utilize this feature within the platform:
- Navigate to the Company List page.
- Click on the Filter button.
- Select the Tag and type ‘Citrix ADC/Gateway’.
- Add any other filter options as needed.
- Click on the filter.
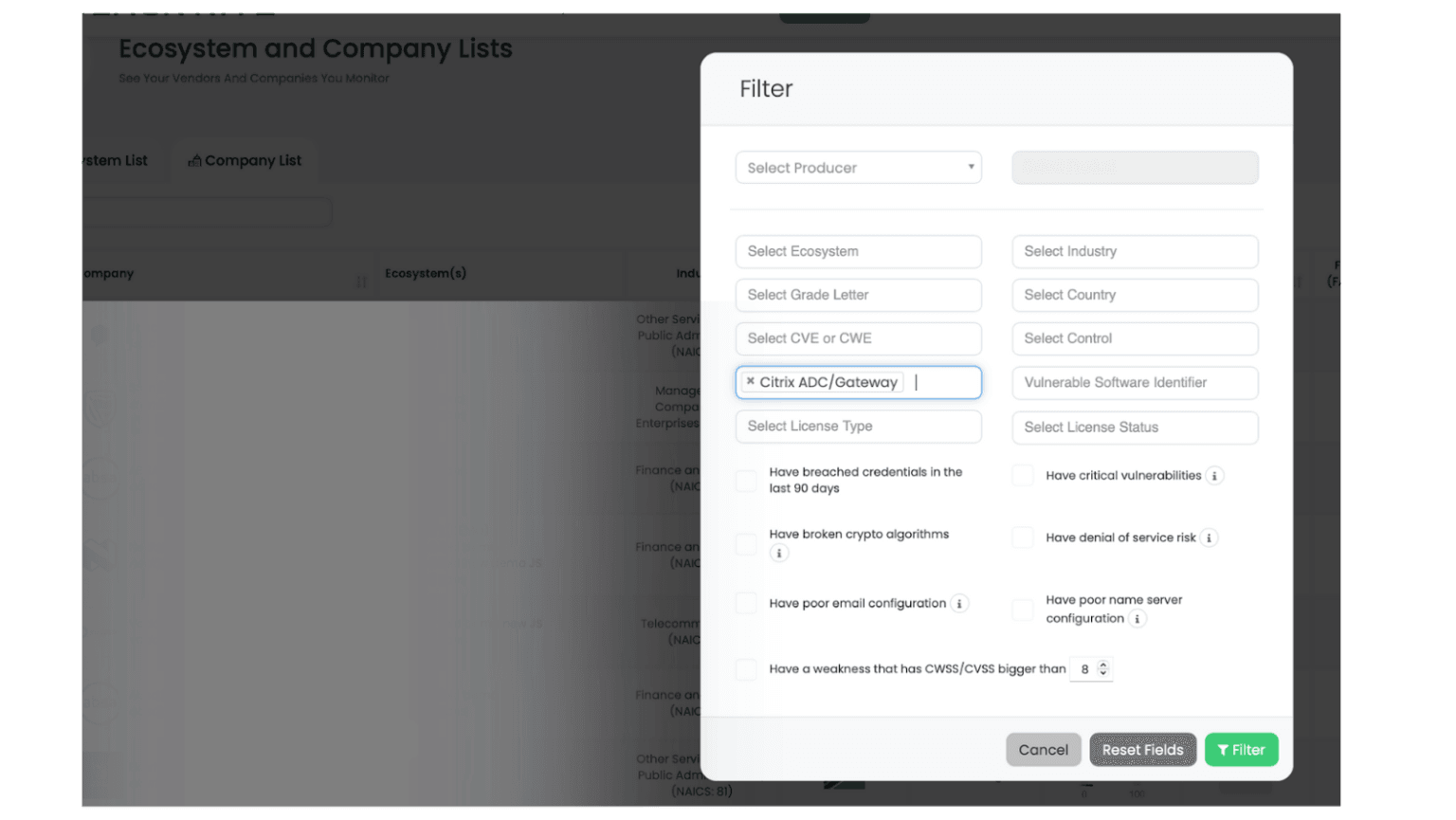
After executing these steps, the platform will display a list of companies that may be using vulnerable products. For better prioritization, you can sort the results by various metrics, such as companies’ cyber rating, Cyber Risk Quantification (FAIR™) scores, or Ransomware Susceptibility Index™ (RSI™) scores.
This efficient identification process will allow you to better manage and mitigate the risks associated with this vulnerability in your vendor ecosystem.
Conclusion
By prioritizing updates, completing continuous vulnerability assessments, and using advanced tools like Black Kite, businesses can significantly mitigate risks like this. In doing so, they protect not only their own infrastructure but also contribute to a safer and more secure digital landscape for all.
As we continue to rely on technology and third-party services in our daily operations, the mutual understanding and joint effort in handling these vulnerabilities are crucial. CVE-2023-3519 is a timely reminder of this fact, providing an opportunity to re-evaluate and strengthen our cybersecurity measures.