WHAT THE SALESLOFT DRIFT INCIDENT MEANS FOR TPRM
WHAT HAPPENED: THE SALESLOFT INCIDENT
Between August 8 and August 18, 2025, the threat actor, tracked as UNC6395 (also known as GRUB1), compromised OAuth tokens for the Salesloft Drift application. The attackers compromised OAuth tokens, which granted them unauthorized access to the systems of hundreds of companies that had integrated with Drift, most notably their Salesforce instances.
Using these stolen tokens, the threat actors systematically exfiltrated vast amounts of data. Their primary goal was not just to steal information, but to harvest valuable credentials and secrets. They specifically targeted data from Salesforce objects such as Cases, Accounts, Users, and Opportunities, searching for sensitive information like Amazon Web Services (AWS) access keys, passwords, and Snowflake-related access tokens.
In the immediate aftermath of the security incident, Salesloft initially stated that customers who were not integrated with Salesforce were unaffected, based on the data available at the time. On August 20, Salesloft began a close collaboration with Salesforce to respond to the incident and all active access and refresh tokens for the Drift application were jointly revoked. Additionally, Salesforce temporarily removed the Drift app from its AppExchange to allow for a thorough investigation.
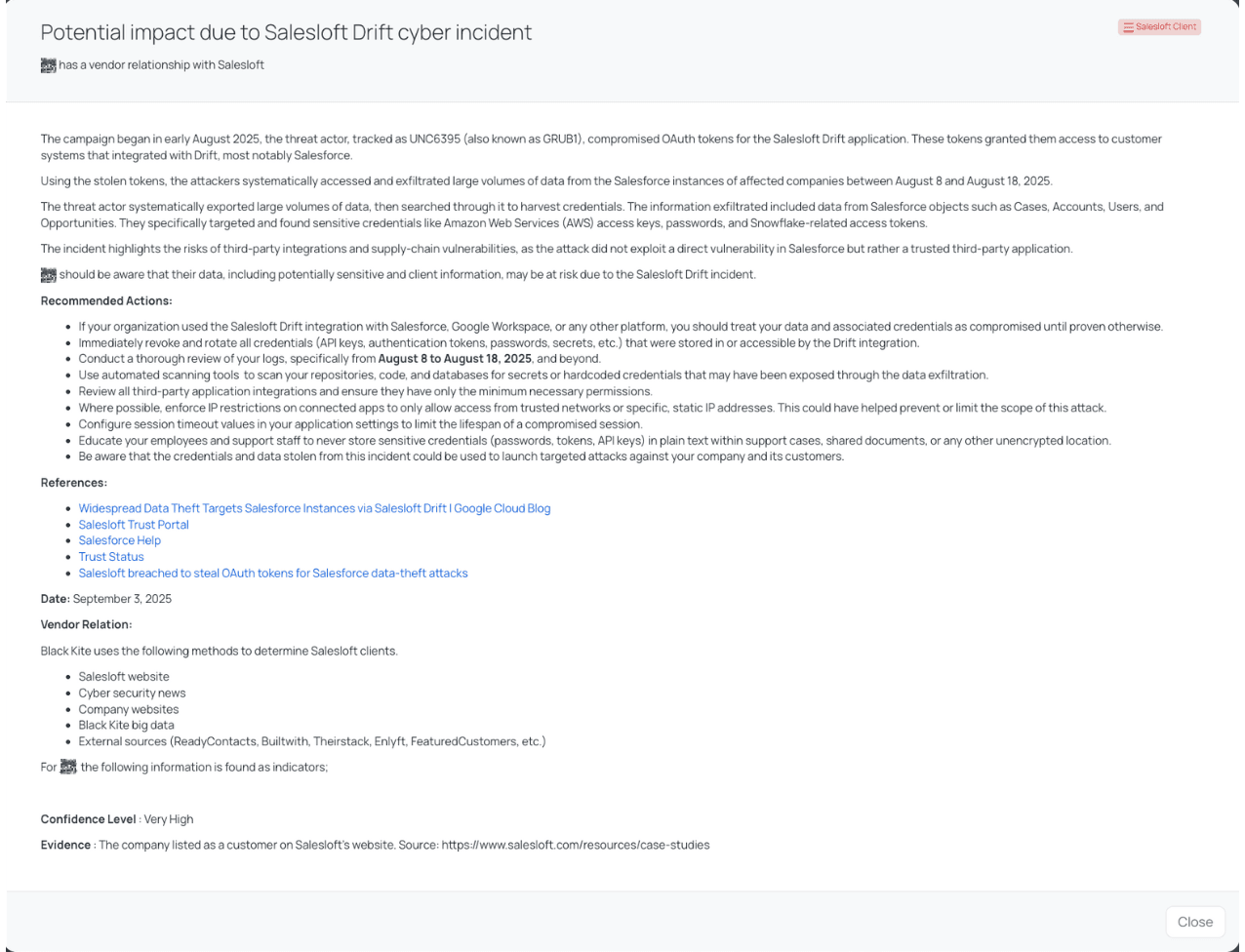
Black Kite’s Salesloft Client FocusTag™ details critical insights on the event for TPRM professionals.
To aid in the investigation of the cybersecurity incident involving its Drift application, Salesloft engaged Mandiant (Google Cloud) on August 28, 2025. The goal of this partnership is to uncover every detail of the incident and to help Salesloft contain the situation and become more secure.
As of September 6, 2025, Mandiant’s research has concluded that the threat actor’s actions were as follows:
- In March through June 2025, the threat actor accessed the Salesloft GitHub account. With this access, the threat actor was able to download content from multiple repositories, add a guest user and establish workflows.
- The investigation noted reconnaissance activities occurring between March 2025 and June 2025 in the Salesloft and Drift application environments. The analysis has not found evidence beyond limited reconnaissance related to the Salesloft application environment.
- The threat actor then accessed Drift’s AWS environment and obtained OAuth tokens for Drift customers’ technology integrations.
- The threat actor used the stolen OAuth tokens to access data via Drift integrations.
Following their investigation, Mandiant also performed crucial response and remediation activities.
According to the latest announcement from Salesloft on September 7, 2025, the integration between the Salesloft platform and Salesforce has now been fully restored.
THE DOMINO EFFECT IN CRM ECOSYSTEMS: HOW A SINGLE INTEGRATION CAN PUT THE ENTIRE SYSTEM AT RISK
This incident illustrates how a third-party integration, such as a chatbot connected to a CRM, can become a widespread supply-chain risk, even if it appears small or insignificant. In the Salesloft-Drift case, attackers gained direct access to Salesforce environments by stealing OAuth and refresh tokens. However, this access was not limited to a single system; attackers leveraged their permissions in Salesforce to reach data in other connected systems as well.
- Pivot via OAuth tokens: The compromised integration tokens allowed attackers to access Salesforce environments and extend their reach to downstream systems. This exposed a particular vulnerability in token-based authorization systems, enabling attackers to access the system directly without cracking user passwords or performing privilege escalation.
- Cross-platform impact: The tokens affected not only Salesforce but also a small number of Google Workspace accounts through the Drift Email integration. This demonstrates the potential for attacks to propagate across multiple platforms. A single third-party integration can act as a bridge between different systems, as clearly illustrated by this incident.
- Ripple effect across organizations: Many companies using Salesforce environments were affected by this breach. According to BleepingComputer, business contacts, customer support data, and certain case records were exfiltrated via the compromised tokens. The interconnected nature of corporate environments amplified the chain effect of a single integration failure.
Key Takeaway: In CRM ecosystems, even integrations that appear minor can become critical attack vectors. A single breach can trigger a domino effect, putting multiple systems and platforms at risk. This underscores the importance of continuously monitoring third-party integrations and enforcing strict controls, especially in systems using OAuth and API-based authorization.
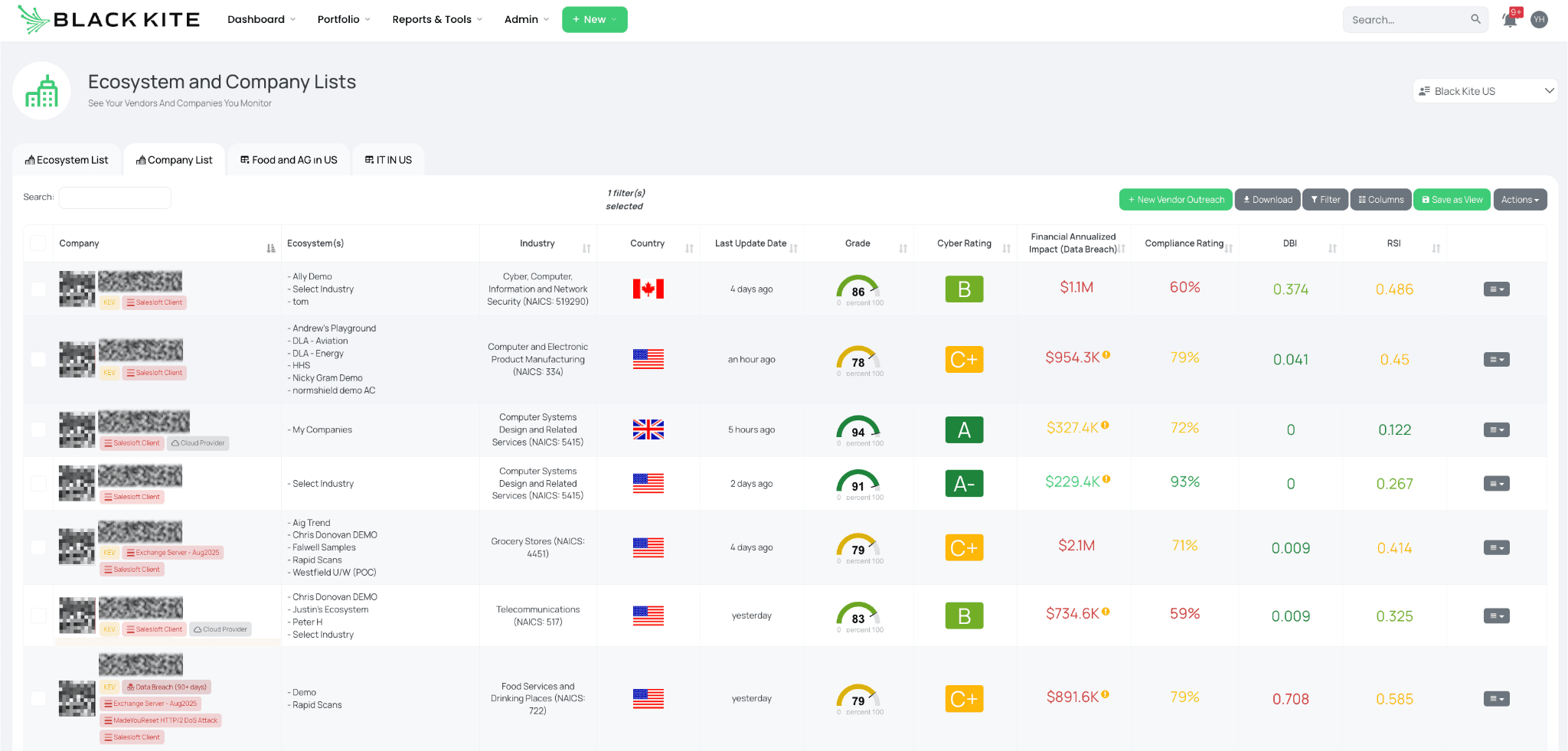
Filtered view of companies with the Salesloft Client FocusTag™ on the Black Kite platform.
KEY QUESTIONS TO ASK FROM A TPRM PERSPECTIVE:
Based on the Salesloft-Drift incident, organizations should ask themselves the following to ensure they’re effectively managing third-party risk:
- Which third-party integrations have high privileges within our CRM and downstream systems?
- Not all integrations are created equal. Some may have read-only access, while others can view or modify critical data. Understanding which integrations have elevated privileges helps prioritize monitoring and mitigation efforts.
- Which integrations can access sensitive data such as credentials, customer cases, or other confidential information?
- A seemingly harmless tool—like a chatbot or email automation—might still touch highly sensitive areas. Organizations should map out exactly what data each integration can access and enforce least-privilege access where possible.
- Are OAuth tokens, API keys, and other credentials rotated regularly, and is unauthorized usage monitored?
- The breach showed how stolen tokens can provide persistent access if not rotated or monitored. Continuous validation and anomaly detection are essential to prevent long-term compromise.
- How quickly can we detect and respond to unusual activity originating from third-party integrations?
- Rapid detection is critical. In the Salesloft case, attackers deleted query jobs to avoid detection, showing that relying solely on standard logs is not enough. Organizations need proactive monitoring of integrations for anomalies.
- Do we maintain sufficient visibility and control over AI agents and automated workflows within our systems?
- Automated agents or bots may operate autonomously, but they can also be exploited to access sensitive data. It’s important to monitor not just human activity but also automated workflows to catch abnormal patterns early.
BLACK KITE’S RECOMMENDATIONS FOR MANAGING THIRD-PARTY RISK AT SCALE
Black Kite provides a practical framework for managing third-party risk, particularly in CRM ecosystems where AI agents and automation tools are increasingly integrated. Based on lessons learned from the Salesloft-Drift incident, the following measures are recommended:
- Supply-Chain Visualization:
Map both direct and indirect integrations across your ecosystem. Understanding the full network of dependencies—not just the immediate third parties but also their partners—helps organizations identify hidden risk areas and potential attack paths. This visibility is crucial to anticipate how a single compromised integration could cascade through multiple systems. - Focused Risk Tagging and Prioritization:
Use tools like FocusTags™ to flag high-risk integrations, such as AI chatbots, automated workflows, or other third-party apps that touch sensitive data. Prioritizing these integrations for continuous monitoring ensures that the most critical potential vulnerabilities are always under scrutiny. - Real-Time Anomaly Detection:
Continuously monitor token usage, API calls, and integration activity for unusual patterns. The Salesloft breach demonstrated that attackers can manipulate queries and delete logs to hide their actions. Real-time detection helps organizations respond before a minor compromise escalates into a larger breach. - Automated Remediation Workflows:
Establish systems that automatically revoke, rotate, or quarantine credentials and integrations when suspicious activity is detected. Automation ensures a faster and more consistent response than relying solely on manual intervention. - Vendor Collaboration and Accountability:
Work closely with service providers to ensure they follow best-practice incident management protocols—prompt notifications, token revocations, joint forensic investigations, and shared post-incident reviews. Transparent collaboration reduces the time to containment and limits downstream impact. - Zero-Trust Principles Across Integrations:
Limit each integration’s privileges to the minimum necessary, enforce least-privilege access, and segment workflows where possible. This minimizes the potential impact of a single compromised integration and makes lateral movement more difficult for attackers.
Why This Matters:
By embedding these practices into TPRM frameworks, organizations can scale secure digital transformation while safely integrating AI agents and third-party tools into CRM ecosystems. The Salesloft-Drift breach serves as a clear reminder that even seemingly minor integrations can become critical attack vectors if not properly managed.
References
- https://cloud.google.com/blog/topics/threat-intelligence/data-theft-salesforce-instances-via-salesloft-drift
- https://trust.salesloft.com/?uid=Drift+Will+Be+Temporarily+Offline+%281%3A55PM+ET%29
- https://help.salesforce.com/s/articleView?id=005134951&type=1
- https://status.salesforce.com/generalmessages/20000217?locale=en-US
- https://www.bleepingcomputer.com/news/security/salesloft-breached-to-steal-oauth-tokens-for-salesforce-data-theft-attacks/
- https://trust.salesloft.com/?uid=Update+on+Mandiant+Drift+and+Salesloft+Application+Investigations