Now’s the Time for Agile, Data-Driven TPRM (and Our Latest Research Proves It)
Third parties aren’t just part of your digital ecosystem—they are your digital ecosystem, acting as critical conduits for innovation and growth. Yet, as we witnessed with the cascading impact of the 2024 Snowflake breach, compromising data for millions across Ticketmaster, AT&T, and beyond, this interconnectedness can quickly become a systemic vulnerability. The integrity of our extended enterprise, and by extension, our ability to deliver value to customers and protect shareholder interests, hinges on how effectively we manage this exposure.
That’s not an anomaly. It’s a preview.
The truth is, third-party risk management (TPRM) or third-party cyber risk management (TPCRM) as we know it isn’t built to handle today’s threats. Think of it like driving a car with only a rearview mirror; you’re constantly looking at where you’ve been, but completely blind to what’s unfolding around you. Most programs are still rooted in outdated compliance checklists and manual processes—treating risk like a checkbox instead of a moving target.
If we don’t rethink our approach to third-party cyber risk management, the security of our interconnected digital ecosystems will remain at risk—and we’ll continue to be caught off guard.
But here’s the good news: As Black Kite’s 2025 Supply Chain Vulnerability Report demonstrates, we now have the visibility, tools, and data to do TPCRM differently—and better.
We just need to act decisively.
TPRM IS AT A CROSSROADS
According to the 2025 Black Kite Third Party Breach Report, third-party vendors were the single biggest entry point for cybercriminals, causing some of the most devastating breaches in recent history.
Here’s why: Big-name companies have strong cyber defenses. Their vendors often don’t. Attackers know this, and they’re using the third-party supply chain as a backdoor.
In today’s business environment, it’s not feasible to simply cut down on vendor access. If anything, cybersecurity teams should expect to deal with even larger vendor ecosystems, including vendors with varying degrees of security maturity, in the coming years.
However, many third-party risk management programs today aren’t equipped to deal with this quickly changing threat landscape because they’re still stuck in the past with:
- Static and Outdated Assessments: Point-in-time questionnaires that miss evolving risks.
- Inefficient Processes: Manual workflows that slow down vendor reviews and strain resources.
- False Sense of Security: Self-reported data that’s incomplete or misleading.
- Inflexible and Reactive Operations: A focus on compliance that limits adaptability to new threats.
We keep trying to solve modern problems with legacy approaches—and it’s not working. As Dr. Stephen Hawking once observed, “Intelligence is the ability to adapt to change.” This rings profoundly true for cybersecurity. While the siren song of artificial intelligence may tempt us as the ‘key’ to solving TPRM, let’s not be fooled. AI is a powerful tool, not a strategy unto itself. Slapping automation on a broken process won’t fix the underlying problem. We need a foundational shift in how we think about and manage third-party cyber risk.
WHAT AN EFFECTIVE TPCRM PROGRAM ACTUALLY LOOKS LIKE
If we want to build resilience into the supply chain, we need to build smarter, not just faster. That means focusing on a sturdy foundation built on several key pillars. Here’s what that looks like:
- Strong governance, with clearly defined policies, roles, responsibilities, and a well-understood risk appetite.
- Mature, well-documented processes that cover the entire vendor lifecycle, from onboarding and due diligence through continuous monitoring and offboarding.
- Quality data and integration, so we understand where our critical vendor data resides, how to collect it, and how to make it usable.
- Skilled people, with expertise to interpret complex information, exercise critical judgement, manage vendor relationships, and make risk-based decisions.
- Technology, to support and enhance the other four pillars.
This isn’t about “transforming” for the sake of buzzwords. It’s about building a TPRM program that works—one that adapts, scales, and gives you clarity instead of chaos.
How Our Report Adds Visibility (and Prioritization) to Third-Party Vulnerabilities
One of the biggest roadblocks to effective TPRM has always been poor visibility. When you don’t have clear data on where you’re vulnerable, you end up treating all risks the same—and that’s a fast track to burnout and blind spots.
For example, in 2024, 40,000 new CVEs were published. Even when you apply standard filtering strategies (for example, only looking at critical CVEs with a CVSS of 9.0+), you’re left with an unmanageable number (about 4,400 CVEs).
This is where our report demonstrates how we can change the game of TPRM.
At Black Kite, we’ve developed a methodology to filter even further by prioritizing for OSINT discoverability, exploitability, and vendor susceptibility. The result? We shrink the haystack. Instead of chasing 40,000 needles, you focus on the 14 that actually matter.
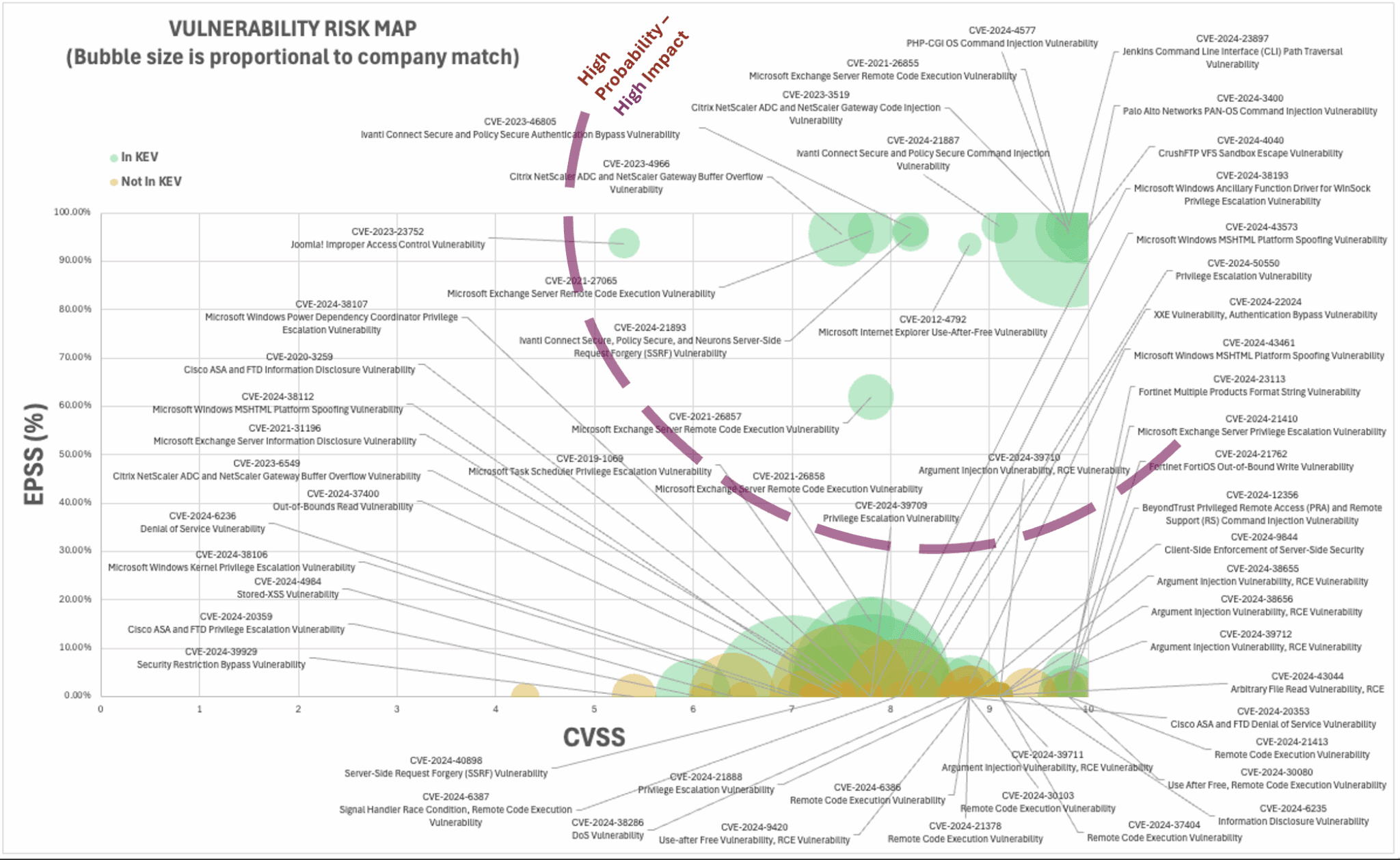
This level of clarity—knowing which vulnerabilities matter, which ones your vendors are exposed to, and which attackers are actively targeting—is the definition of an agile, data-backed approach to supply chain security. No more guesswork or wasted resources on vulnerabilities that pose no real threat. For the first time, TPRM teams can act decisively, focusing on the vulnerabilities that attackers will exploit next before it’s too late.
IT'S TIME TO LEAD THE SHIFT IN TPCRM
Compared to previous years, 2024 saw an estimated 56% increase in zero-day vulnerabilities. Ransomware and unauthorized network access also served as popular vectors for bad actors to break into third parties and their larger supply chains.
The writing is on the wall: It’s time to ditch outdated TPRM methods and embrace a new era—one where TPRM transforms from a mere compliance exercise into a strategic advantage that underpins our business resilience and market credibility.
This isn’t just about security; it’s about enabling the business to innovate confidently and operate securely in an increasingly interconnected world. This change reinforces the executive vision by explicitly linking the transformation of TPRM to broader business objectives like resilience and market credibility, which are talking points that resonate deeply in the boardroom.
Want to see how your organization can prioritize real risks in your vendor ecosystem—before they become breaches? Read our full report, “2025 Supply Chain Vulnerability Report: Navigating a New Era of Managing Vulnerability Risk in Third Parties.”