Healthcare Ransomware Attack Led to Cancelled Surgeries and Diverted Patients – What is Next?
Published
Aug 27, 2021
Updated
Jan 27, 2026
Authors
Black Kite
Last week Memorial Health canceled surgeries and had to redirect patients due to a ransomware attack allegedly by a new-in-the-market ransomware gang named HIVE. This- once again- turned eyes on the healthcare sector. What makes healthcare such a juicy target for cybercriminals? With growing cybersecurity challenges in the threat landscape, is there a way to increase the healthcare sector’s immunity to such attacks?
What we know so far
According to the announcement made by the Memorial Health CEO, the hospital is currently in the negotiation process with hackers – in concert with the FBI. He also added the hospital infrastructure has “robust processes in place to maintain safe and effective patient care”.
The health system said it was working on paper charts to avoid further disturbance after its networks were taken down. In the meantime, all non-emergency surgical procedures and radiological exams have been postponed.
Incorporating three hospitals in its network (Marietta Memorial Hospital, Selby General Hospital, and Sistersville General Hospital) in Ohio and West Virginia, and with more than 3,000 employees, Memorial Health is a non-profit system.
According to Black Kite researchers, the attack appears to be the work of the HIVE ransomware gang. Unfortunately, it’s too early to claim whether or not patient data has been released, although the hospital’s issuance states otherwise. It can take up to months and sometimes a year, to ensure no protected health information (PHI) is leaked.
HIVE is the usual suspect
The HIVE ransomware gang is the usual suspect in the Memorial Health attack. Like other gangs, it has a dedicated leak site disclosing the date of the attack and countdown to the due date for the payment.
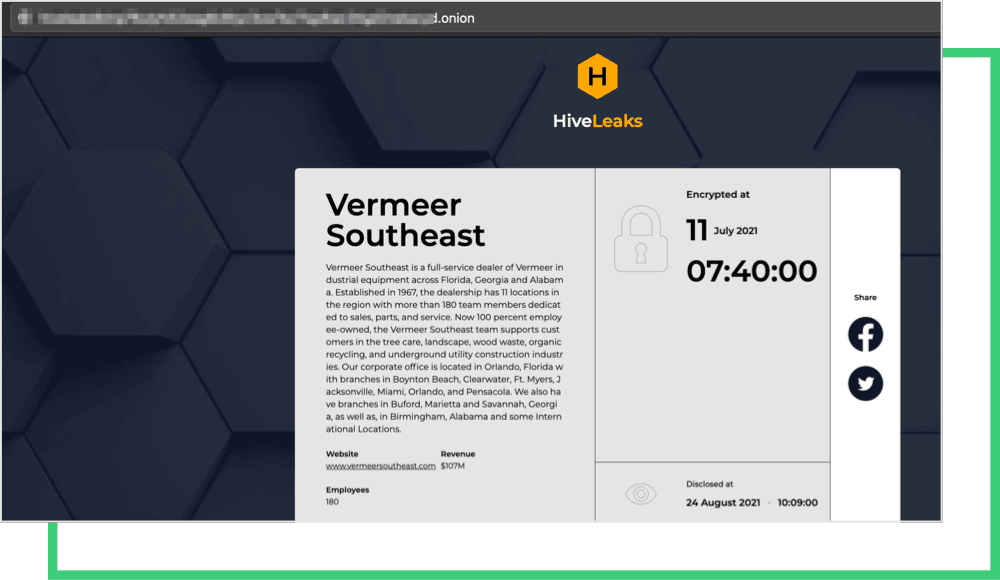
HIVE is a relatively new gang that emerged in July. Although new to the market, HIVE has attacked many companies, mostly small to medium-sized businesses. Black Kite researchers made a detailed analysis of HIVE victims and derived their industry, country, and leak details. For privacy reasons, we do not disclose the names of the companies.
Industry | Country | Incident Date | Disclosed Date | Details |
|---|---|---|---|---|
Software | Canada | 06.23.2021 | 06.26.2021 | Not disclosed |
Law Practice | US | 06.24.2021 | 06.30.2021 | Not disclosed |
Hardware Store | US | 06.30.2021 | 07.12.2021 | Not disclosed |
Charter Airline | Portugal | 06.28.2021 | 07.11.2021 | Not disclosed |
Media | India | 07.01.2021 | 07.17.2021 | Not disclosed |
Farming | US | 07.01.2021 | 07.17.2021 | 200 MB – example part |
Legal Services | US | 07.11.2021 | 07.24.2021 | 12 MB – example part |
Marketing & Advertising | US | 07.13.2021 | 07.24.2021 | 200 MB – example part |
Farming | US | 07.14.2021 | 07.24.2021 | Not disclosed |
Printing | US | 07.14.2021 | 07.24.2021 | Not disclosed |
Automotive | US | 07.20.2021 | 07.24.2021 | Not disclosed |
Logistic | Peru | 07.01.2021 | 07.30.2021 | 30 MB – example part |
Electrical & Electronic Manufacturing | US | 07.01.2021 | 07.30.2021 | 116 MB – example part |
Accomodation | France | 07.04.2021 | 07.31.2021 | 256 MB – example part |
Physical Security | Thailand | 07.10.2021 | 08.02.2021 | Not disclosed |
Internet | Australia | 08.03.2021 | 08.26.2021 | Not disclosed |
Construction & Building | US | 08.03.2021 | 08.10.2021 | Not disclosed |
IT & Services | US | 08.03.2021 | 08.15.2021 | Not disclosed |
Financial Services | US | 07.12.2021 | 08.05.2021 | 254 GB |
Construction & Building | Germany | 07.04.2021 | 08.09.2021 | Not disclosed |
Software | US | 07.14.2021 | 08.09.2021 | Not disclosed |
Education | US | 07.30.2021 | 08.16.2021 | Not disclosed |
Real Estate | US | 08.03.2021 | 08.17.2021 | Not disclosed |
Construction | Norway | 07.17.2021 | 08.17.2021 | Not disclosed |
Machinery | China | 07.28.2021 | 08.17.2021 | Not disclosed |
Machinery | US | 07.11.2021 | 08.19.2021 | Not disclosed |
Legal Services | Germany | 07.09.2021 | 08.20.2021 | Not disclosed |
Design | US | 07.13.2021 | 08.20.2021 | Not disclosed |
Accounting | UK | 08.01.2021 | 08.20.2021 | Not disclosed |
Financial Services | US | 07.31.2021 | 08.23.2021 | Not disclosed |
IT & Services | Spain | 07.24.2021 | 08.20.2021 | 13 MB – example part |
Black Kite RSI™
Black Kite’s Ransomware Susceptibility Index® determines how susceptible a company and its third parties are to a ransomware attack. Data is collected from various open-source intelligence (OSINT) sources including internet-wide scanners, hacker forums, the deep/dark web, and more. Black Kite correlates each finding with 26 control items using data and machine learning in order to provide approximations. Black Kite’s RSI™ scores range on a scale from 0.0 (least susceptible) to 1.0 (most susceptible).
How do we interpret the RSI™ score?
Since this is a ransomware attack, we immediately inspected the RSI™ score of the company on our platform, which yielded 0.81. Black Kite continuously monitors the Ransomware Susceptibility Index® along with an organization’s technical score.
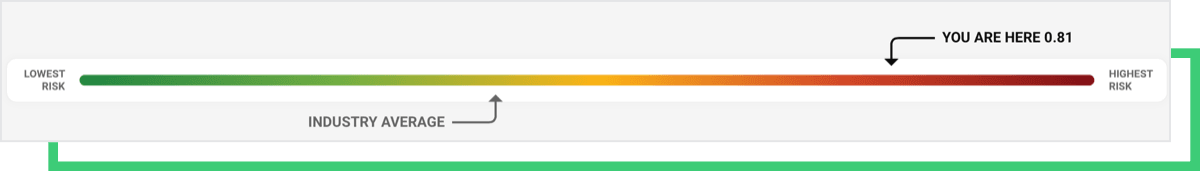
Memorial Health’s RSI™ score is above a critical threshold, that is 0.6, set by the Black Kite Research Team based on historical and statistical data of ransomware attacks. Furthermore, it is 39% more susceptible to ransomware than the industry average.
The Leverage Factor is the Undisruptability of the Healthcare System
The unique nature of the industry and its workers, keeping data and computer systems protected is a complex task. Doctors and nurses, in healthcare, shift from workstation to workstation with varying levels of system privileges. Shared workstations, in this sense, increase the attack surface of a healthcare organization.
Furthermore, the nature of the PII data and criticality of the operations even makes the stakes higher in healthcare. The IT and cybersecurity controls have to guarantee both the safety and security of the patients.
A ransomware attack both threatens the continuity of life-critical operations and privacy of health-related data. These two critical factors have made the healthcare sector a lucrative target for hackers. It is by no means ethical for anybody to execute an attack on a hospital unless it is a ruthless criminal. However, we should keep in mind that cybercriminals are in this sense no different than ordinary criminals.
CISA’s Advisory on Ransomware Is a Good Starting Point To Increase Cybersecurity Maturity in Healthcare
CISA recently released an advisory for organizations to defend against ransomware and prevent data breaches. The info sheet named, “Protecting Sensitive and Personal Information from Ransomware-Caused Data Breaches,” is a generalized set of best practices and recommendations, and sector-free. Therefore any sector, including healthcare, can adapt this set of control items to increase its cyber security maturity and immunity to ransomware attacks.
The recommendations are framed according to the three tiers of a ransomware attack; namely Preventing the ransomware attack, Protecting sensitive and personal information; and Responding to ransomware-driven data breaches.
The infosheet is short and can be considered as an easy-to-consume guide for IT personnel. The reader is referred to other resources for detailed information.
Here are the recommendation items for each tier:
Preventing the ransomware attack
- Maintain offline, encrypted backups of data and regularly test your backups.
- Create, maintain, and exercise a basic cyber incident response plan, resiliency plan, and associated communications plan.
- Mitigate internet-facing vulnerabilities and misconfigurations to reduce risk of actors exploiting this attack surface.
- Reduce the risk of phishing emails from reaching end users by cybersecurity awareness, training and enabling strong spam filters.
- Practice good cyber hygiene by enabling MFA, anti-virus and anti-malware.
Protecting sensitive and personal information
- Know what personal and sensitive information is stored on your systems and who has access to it.
- Implement physical security best practices from FTC, and CISA.
- Implement cybersecurity best practices by implementing firewalls, identifying where PII is stored, encrypting sensitive information, etc.
- Ensure your cyber incident response and communications plans include response and notification procedures for data breach incidents.
Responding to ransomware caused data breaches
- Secure network operations and stop additional data loss.
- If no initial mitigation actions appear possible, take a system image and memory capture of a sample of affected devices.
- Follow notification requirements as outlined in your cyber incident response plan.
- Report the incident to CISA, your local Federal Bureau of Investigation (FBI) field office, the FBI Internet Crime Complaint Center, or your local U.S. Secret Service office.