Focus Friday: TPRM Insights on SharePoint, MSSQL, and SAP NetWeaver Critical Vulnerabilities
Welcome to this week’s edition of Focus Friday, where we examine the latest high-profile cybersecurity incidents through the lens of Third-Party Risk Management (TPRM). This week, we focus on three enterprise-critical platforms—Microsoft SharePoint, Microsoft SQL Server (MSSQL), and SAP NetWeaver—all of which have received significant security updates to address newly identified vulnerabilities.
Each of these technologies plays a central role in vendor environments: SharePoint as a collaboration and document management system, MSSQL as a core database engine, and SAP NetWeaver as the backbone of many enterprise applications. The vulnerabilities patched this month range from remote code execution (RCE) and command injection to authentication bypass and insecure deserialization—all of which could lead to significant compromise if left unpatched. In the sections that follow, we provide a TPRM-focused analysis of these vulnerabilities, offering insights into vendor risk, key questions to ask, remediation recommendations, and the details of Black Kite’s FocusTags™ for each case.
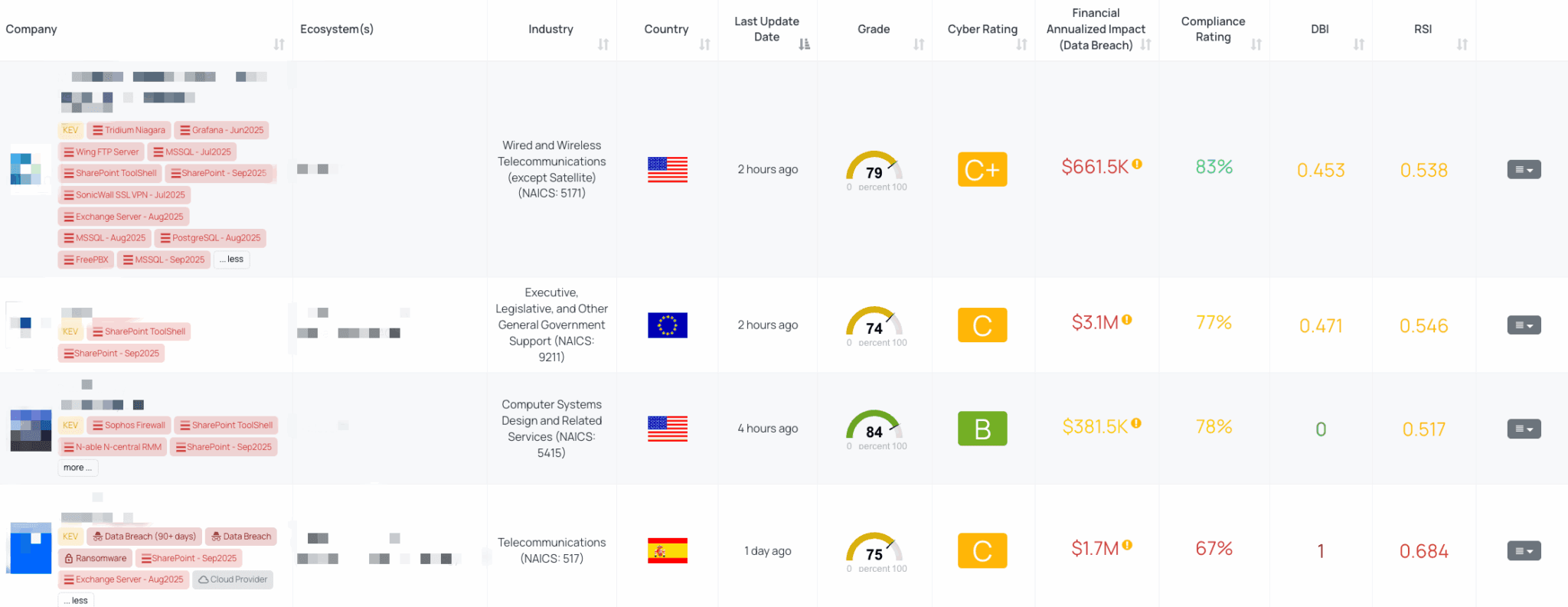
Filtered view of companies with SharePoint – Sep2025 FocusTag™ on the Black Kite platform.
CVE-2025-54897 / MICROSOFT SHAREPOINT - REMOTE CODE EXECUTION
What is the CVE-2025-54897 SharePoint Vulnerability?
CVE-2025-54897 is a Remote Code Execution (RCE) vulnerability in Microsoft SharePoint, stemming from a deserialization of untrusted data weakness (CWE-502). The vulnerability carries a High severity rating, with a CVSS score of 8.8. Its EPSS score is 0.52%, indicating a modest but non-negligible probability of being exploited in the near future.
It was published as part of Microsoft’s September 2025 Patch Tuesday. This patch also covers related SharePoint issues. At the time of release, no public proof-of-concept code or public exploit campaign for CVE-2025-54897 had been disclosed, and Microsoft’s exploitability assessment classified this vulnerability (together with related ones) as “Less Likely.”
As of now, CVE-2025-54897 has not been added to CISA’s Known Exploited Vulnerabilities (KEV) catalog (based on public sources accessed). There is no CISA advisory specifically naming CVE-2025-54897 as being exploited in the wild. Microsoft has published its security update guidance that includes this fix.
Why TPRM Professionals Should Care About This Vulnerability
From a Third-Party Risk Management (TPRM) perspective, CVE-2025-54897 is important for several reasons:
- Because SharePoint is often used by vendors to host internal document management systems, collaboration sites, file shares, or intranet portals, a remote code execution vulnerability could lead to serious confidentiality, integrity, and availability impacts if exploited.
- Such an RCE could allow malicious actors to execute arbitrary code, potentially gaining control of vendor-hosted servers, moving laterally, exfiltrating data, or deploying malware. If those servers communicate with or support critical systems (customer data, financial systems, etc.), the downstream risk is high.
- Vendors may be running unsupported or older SharePoint versions, especially in smaller or less mature environments. Ensuring they have applied recent patches (including for CVE-2025-54897) is critical.
- Even though CVE-2025-54897 is “newer” (September patch), two related vulnerabilities—CVE-2025-53760 (SSRF) and CVE-2025-49712 (another deserialization / RCE) from August 2025—precede it. For completeness, vendors should be verifying that those earlier ones were covered (patched) appropriately.
- Because exploitability is currently assessed as “Less Likely,” some organizations might deprioritize it, but the EPSS score and high severity make it something that should be in the near-term patching plan, particularly for public-facing or externally accessible SharePoint servers.
What questions should TPRM professionals ask vendors about this vulnerability?
To assess whether a vendor is properly managing the risk posed by CVE-2025-54897 (and the related SharePoint vulnerabilities), here are some specific questions:
- Can you confirm if you have updated all instances of Microsoft SharePoint Server Subscription Edition, Microsoft SharePoint Server 2019, and Microsoft SharePoint Enterprise Server 2016 to the patched versions (16.0.18526.20518, 16.0.19127.20100, 16.0.10417.20041, 16.0.10417.20047, 16.0.5513.1002, 16.0.5517.1000) to mitigate the risk of CVE-2025-53760, CVE-2025-49712, and CVE-2025-54897?
- Have you implemented any specific measures to monitor and prevent Server-Side Request Forgery (SSRF) and Deserialization of Untrusted Data vulnerabilities in your Microsoft SharePoint servers, which are the root causes of CVE-2025-53760, CVE-2025-49712, and CVE-2025-54897?
- Can you confirm if you have taken steps to prevent an attacker from exploiting the Elevation of Privilege vulnerability (CVE-2025-53760) in Microsoft SharePoint, which allows viewing sensitive information and making minor changes to disclosed information?
- Have you implemented any specific measures to prevent an authorized attacker with low privileges from exploiting the Remote Code Execution vulnerabilities (CVE-2025-49712 and CVE-2025-54897) in Microsoft SharePoint, which can lead to arbitrary code execution on the SharePoint server?
Remediation Recommendations for Vendors Subject to this Risk
Here are concrete steps vendors should take to mitigate CVE-2025-54897 and its related SharePoint vulnerabilities:
- Apply the official Microsoft security update for CVE-2025-54897 immediately to all affected SharePoint servers. Ensure you have updated to the correct build versions.
- Verify that earlier vulnerabilities (CVE-2025-53760 and CVE-2025-49712) are also patched, since those were published in August and are part of the same class of risk (SSRF or deserialization).
- Reduce exposure: for servers that do not need to be publicly reachable, block external access or restrict to trusted networks.
- Harden SharePoint configuration: disable or limit features that allow arbitrary serialization, reduce privileges for site owners, ensure that data inputs are validated and sanitized, and enforce least privilege.
- Enable and configure appropriate detection tools (e.g., EDR, file integrity monitoring, web application firewall rules) to detect exploitation attempts.
- Ensure a rigorous patch management process: inventory all SharePoint servers (including versions, builds), apply updates in a timely fashion, and test patches in staging before production rollout.
How TPRM Professionals Can Leverage Black Kite for This Vulnerability
Black Kite’s FocusTag “SharePoint ‒ Sep2025” was published to ensure customers are aware of multiple high-impact vulnerabilities in Microsoft SharePoint (including CVE-2025-54897, as well as CVE-2025-53760 and CVE-2025-49712).
Here’s how TPRM teams can operationalize this tag:
- Use Black Kite’s vendor scanning to identify which vendors in your ecosystem host affected SharePoint versions or assets (IP addresses, subdomains) that match the builds listed.
- Review the asset details Black Kite provides: if any vendor’s asset shows presence of an affected SharePoint server (by version/build), those vendors move into your high-risk bucket for follow-up.
- Include the specific questions above in any vendor questionnaires or risk assessments triggered by this tag.
- Prioritize remediation efforts (patching, mitigation, monitoring) for vendors identified by Black Kite as having vulnerable assets.
- Since this tag is new (covers the September patch), ensure you also cross-check whether vendors had already addressed the August vulnerabilities (CVE-2025-53760 and CVE-2025-49712), as failure to do so may leave them vulnerable even after patching September issues.
- Track updates to the FocusTag: if new exploit activity emerges or if CISA adds any of these CVEs to KEV, that increases urgency.
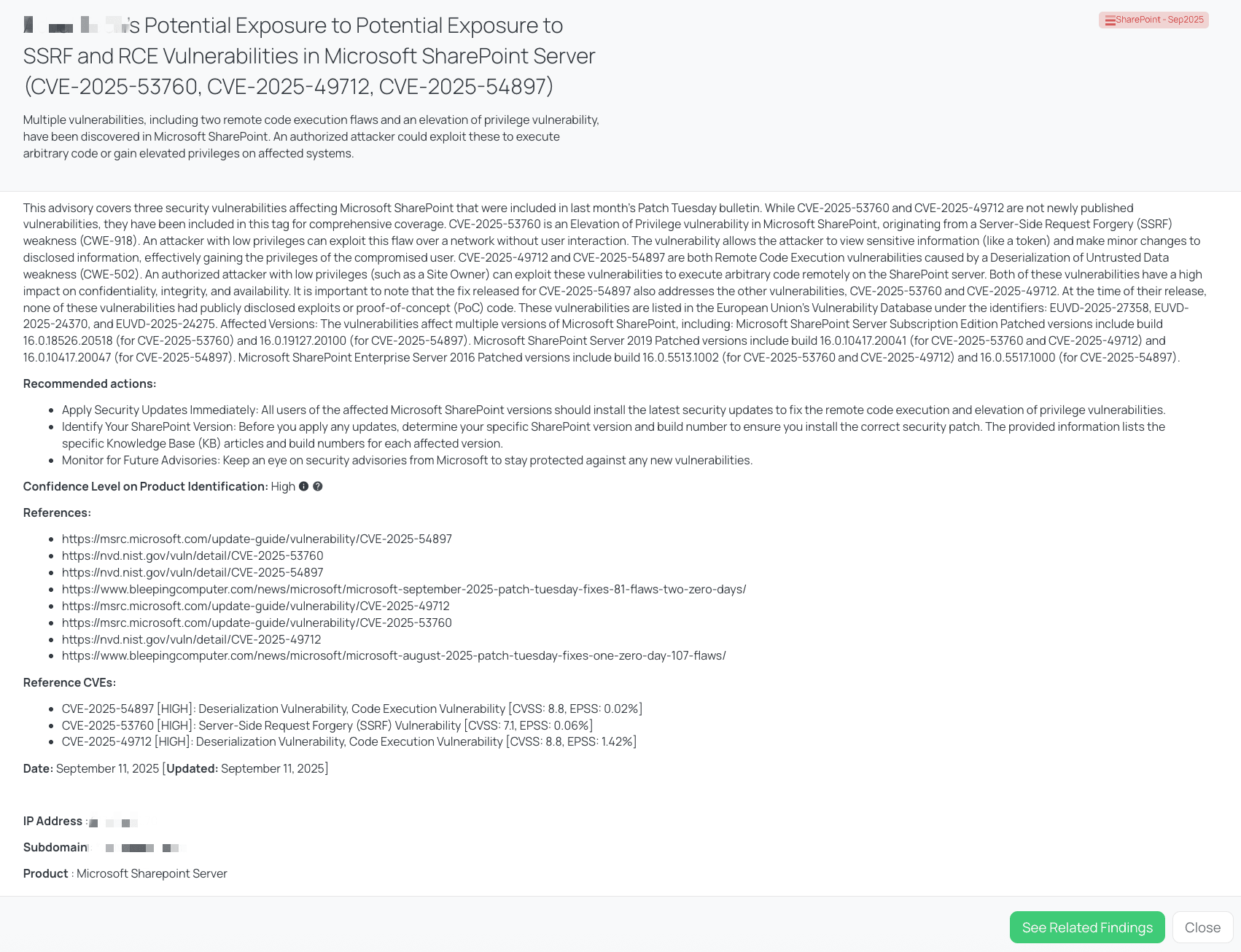
Black Kite’s SharePoint – Sep2025 FocusTag™ details critical insights on the event for TPRM professionals.
CVE-2025-55227 & CVE-2025-47997 / MICROSOFT SQL SERVER VULNERABILITIES
What are the MSSQL vulnerabilities CVE-2025-55227 and CVE-2025-47997?
CVE-2025-55227 is a command injection/elevation of privilege vulnerability in Microsoft SQL Server. It has a high severity rating (CVSS 8.8) and an EPSS of 0.07%. The flaw allows an attacker with low privileges to inject malicious SQL code during table creation, potentially gaining sysadmin privileges over the instance. It was disclosed in Microsoft’s September 2025 Patch Tuesday. At the time of disclosure, no proof-of-concept code was publicly available, and Microsoft marked the exploitability as “Less Likely.”
CVE-2025-47997 is an information disclosure vulnerability caused by a race condition in Microsoft SQL Server. It has a Medium severity rating (CVSS 6.5) and an EPSS of 0.10%. An attacker with low privileges could leverage improper synchronization to expose sensitive information over the network. This issue was also fixed in the September 2025 Patch Tuesday, and similarly assessed by Microsoft as “Less Likely” to be exploited.
As of the latest review, neither CVE-2025-55227 nor CVE-2025-47997 appears in CISA’s Known Exploited Vulnerabilities (KEV) catalog, and no public advisories indicate in-the-wild exploitation of either vulnerability.
Why should TPRM Professionals care about these MSSQL vulnerabilities?
From a third-party risk management standpoint, these vulnerabilities are significant because:
- SQL Server is often used by vendors for database backends, business logic, reporting, or web apps. If a vendor’s SQL Server is compromised, data theft, corruption, or system takeover are all possible.
- For CVE-2025-55227, gaining sysadmin privileges means full control over the SQL instance, which can be escalated to host or network control in some configurations, or used to exfiltrate sensitive data or execute malicious code.
- Even though CVE-2025-47997 is “only” an information disclosure, its race condition nature could leak credentials, configuration files, or other sensitive data, which may facilitate further attacks (e.g., privilege escalation, lateral movement).
- Because exploitability is assessed as “Less Likely” and EPSS scores are relatively low, agencies or vendors may deprioritize these. But dependency on SQL Server, and the possibility of chaining vulnerabilities or leveraging misconfigurations, means these shouldn’t be ignored.
- Vendors might be running outdated builds, or applying patches unevenly (for example, between cumulative updates (CUs) and GDR patches). Ensuring where they stand relative to the patched builds listed in Microsoft advisories is crucial.
What questions should TPRM professionals ask vendors about these vulnerabilities?
Here are specific questions to help assess vendor risk relative to these MSSQL issues:
- Can you confirm if you have upgraded all instances of Microsoft SQL Server to the patched versions mentioned in the advisory (SQL Server 2022: CU20+GDR: Builds 16.0.4212.1 and above, RTM+GDR: Builds 16.0.1150.1 and above, SQL Server 2019: CU32+GDR: Builds 15.0.4445.1 and above, RTM+GDR: Builds 15.0.2145.1 and above, SQL Server 2017: CU31+GDR: Builds 14.0.3505.1 and above, RTM+GDR: Builds 14.0.2085.1 and above, SQL Server 2016: Azure Connect Feature Pack: Builds 13.0.7065.1 and above, SP3 RTM+GDR: Builds 13.0.6470.1 and above) to mitigate the risk of CVE-2025-55227 and CVE-2025-47997?
- Have you implemented any specific measures to prevent command injection attacks, particularly in the context of table creation in Microsoft SQL Server, to address the elevation of privilege vulnerability (CVE-2025-55227)?
- What steps have you taken to address the race condition vulnerability (CVE-2025-47997) in Microsoft SQL Server that could potentially lead to the disclosure of sensitive information?
- How are you monitoring for further advisories from Microsoft to ensure protection against any future vulnerabilities in Microsoft SQL Server, particularly those similar to CVE-2025-55227 and CVE-2025-47997?
Remediation Recommendations for Vendors subject to this risk
Here are concrete steps vendors should take to mitigate these MSSQL vulnerabilities:
- Deploy Microsoft’s relevant security updates immediately for all affected SQL Server versions (2022, 2019, 2017, 2016, etc.), ensuring correct builds are used.
- Inventory your SQL Server instances: track version, build number, edition (for example, Enterprise vs Standard), and whether they’re on the CU or GDR branch.
- Restrict network exposure: ensure that SQL Servers are not unnecessarily exposed; use firewalls, VLANs/segmentation, IP whitelisting, or VPNs as needed.
- Enforce least privilege: limit which accounts can perform schema changes or table creation. Avoid giving low-privileged accounts write access beyond what they strictly need.
- Enable detailed logging and monitoring: monitor for anomalous SQL statements, elevated privilege operations, and timing anomalies that might indicate race conditions.
- Test patches in staging: ensure that deploying patches doesn’t break existing functionality, especially if vendor-supplied applications rely on specific behaviors.
- Implement mitigations (if available): if Microsoft provides any workarounds or mitigations (e.g., disabling certain features, applying temp configurations) for cases where patching is delayed, use them.
How TPRM profe
ssionals can leverage Black Kite for this vulnerability
Black Kite’s FocusTag “MSSQL ‒ Sep2025” gives organizations a way to zero in on which vendors are potentially running vulnerable Microsoft SQL Server instances (i.e., instances with version/build numbers pre-patch for CVE-2025-55227 or CVE-2025-47997). Here’s how to operationalize it:
- Use Black Kite’s vendor intelligence/scan data to identify assets (IP addresses, hostnames, subdomains) that correspond to Microsoft SQL Server versions/builds that are vulnerable.
- For each vendor identified with vulnerable SQL Server assets, initiate follow-ups using the questions above.
- Prioritize patching efforts or additional security controls for those vendors with externally reachable SQL Server instances or those with sensitive data stored.
- Include this FocusTag in your vendor risk framework: treat vendors flagged by this tag as requiring more frequent reviews or more aggressive mitigation.
- Monitor for any updates to the tag: e.g., if exploit activity emerges, or if these CVEs are added to CISA’s KEV catalog, that raises the urgency.
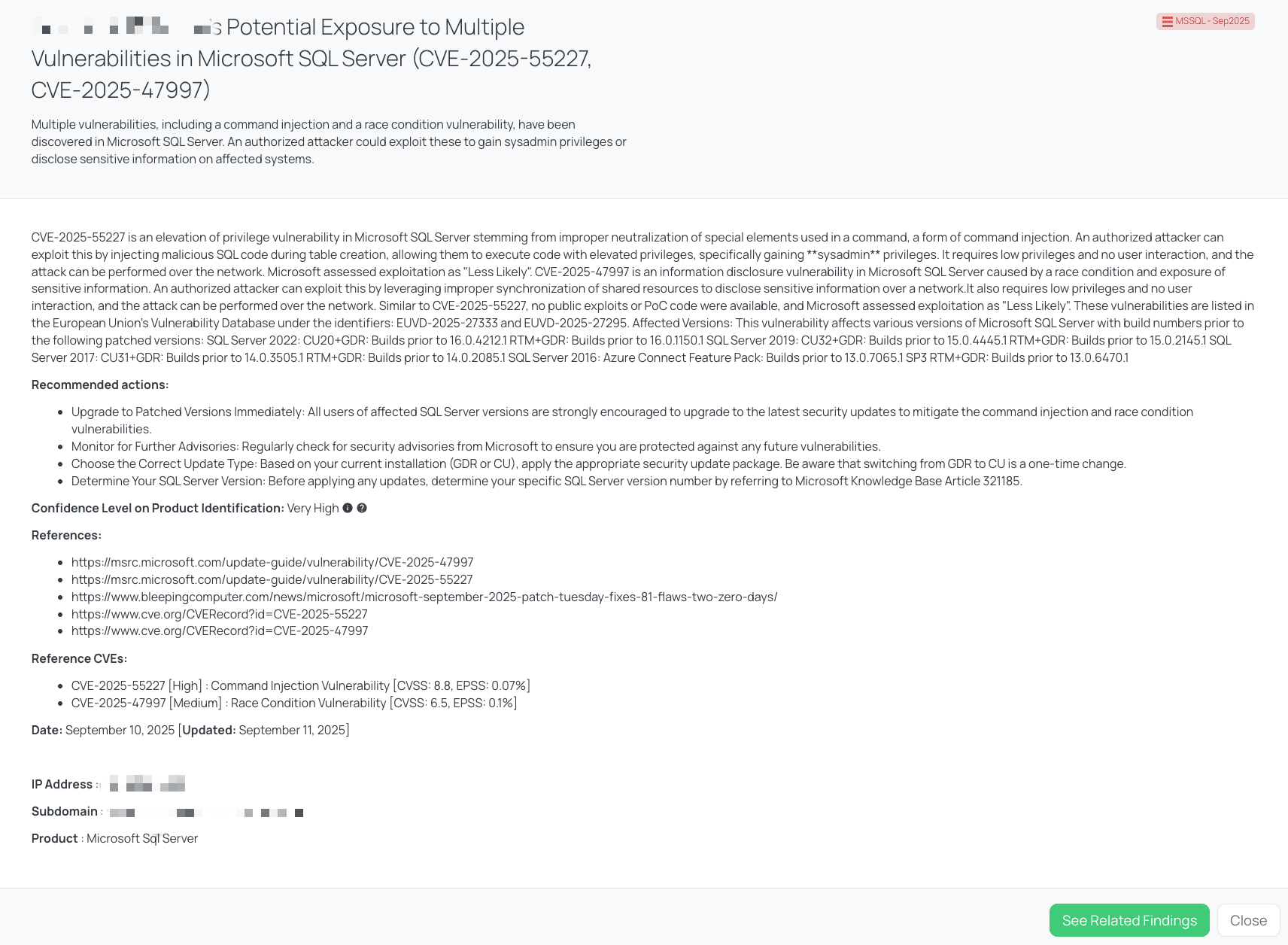
Black Kite’s MSSQL – Sep2025 FocusTag™ details critical insights on the event for TPRM professionals.
CVE-2025-42944, CVE-2025-42922 & CVE-2025-42958 / SAP NETWEAVER CRITICAL VULNERABILITIES
What are the SAP NetWeaver vulnerabilities CVE-2025-42944, CVE-2025-42922, and CVE-2025-42958?
In September 2025, SAP released security updates addressing three critical vulnerabilities in NetWeaver software:
- CVE-2025-42944 [CRITICAL]: Insecure Deserialization Vulnerability [CVSS: 10, EPSS: 0.03%]
Found in SAP NetWeaver (RMIP4), ServerCore 7.50. An unauthenticated attacker can send a malicious Java object to an open RMI-P4 port, resulting in arbitrary OS command execution. - CVE-2025-42922 [CRITICAL]: Insecure File Operations Vulnerability [CVSS: 9.9, EPSS: 0.05%]
Impacts NetWeaver AS Java (Deploy Web Service), J2EE-APPS 7.50. An attacker with authenticated non-administrative access can abuse the deployment functionality to upload arbitrary files, leading to full system compromise. - CVE-2025-42958 [CRITICAL]: Missing Authentication Check Vulnerability [CVSS: 9.1, EPSS: 0.06%]
Allows bypassing of authentication checks in certain NetWeaver components. While full technical details were not disclosed, this flaw could allow attackers to interact with protected services without valid credentials.
Publication & Exploitation Status
These vulnerabilities were disclosed in SAP’s September 2025 Patch Tuesday. Public proof-of-concept (PoC) exploits have been reported. However, no confirmed in-the-wild exploitation has been attributed so far. Based on current checks, none of these CVEs have been added to the CISA KEV Catalog, nor has CISA published specific advisories mentioning them.
Why should TPRM Professionals care about these SAP NetWeaver vulnerabilities?
SAP NetWeaver often underpins critical enterprise processes, making any flaw in its services a high-value target for attackers.
- For CVE-2025-42944, the insecure deserialization flaw is particularly dangerous because it enables unauthenticated remote code execution through a commonly exposed RMI-P4 port. If vendors expose this port externally or fail to restrict access, attackers could gain full control over the system.
- For CVE-2025-42922, arbitrary file uploads by authenticated users can lead to malware deployment, privilege escalation, or lateral movement across enterprise environments.
- For CVE-2025-42958, bypassing authentication controls erodes a fundamental security boundary, potentially exposing sensitive administrative functions or services.
From a TPRM perspective, these vulnerabilities create severe downstream risks. A compromised NetWeaver server could leak sensitive business data, disrupt vendor services, or serve as a foothold for threat actors to move deeper into a vendor’s environment. If your vendors rely on SAP NetWeaver, patching and monitoring these flaws is non-negotiable.
What questions should TPRM professionals ask vendors about these vulnerabilities?
To evaluate whether vendors are at risk, TPRM teams should ask targeted, vulnerability-specific questions:
- Have you updated all instances of SAP NetWeaver (RMIP4), ServerCore 7.50, and SAP NetWeaver AS Java (Deploy Web Service), J2EE-APPS 7.50 to the versions released in the September 2025 security updates to mitigate the risk of CVE-2025-42944, CVE-2025-42922, and CVE-2025-42958?
- Can you confirm if you have restricted network exposure of the RMI-P4 port (often 50000 for AS Java) to only necessary internal SAP-to-SAP communication or administration purposes to mitigate the risk of CVE-2025-42944?
- Have you implemented the principle of least privilege for all users of SAP NetWeaver AS Java, especially concerning web service deployment functionalities, to mitigate the risk of CVE-2025-42922?
- Are you actively monitoring SAP NetWeaver logs for any unusual activity, such as attempts at arbitrary file uploads, unauthorized command execution, or suspicious authentication bypass attempts, particularly after applying patches?
Remediation Recommendations for Vendors subject to this risk
Vendors should take the following steps to mitigate these vulnerabilities:
- Apply SAP’s September 2025 security updates immediately across all NetWeaver systems to address CVE-2025-42944, CVE-2025-42922, and CVE-2025-42958.
- Restrict exposure of the RMI-P4 port (commonly 50000) to only trusted internal communications. Ensure it is not accessible from the internet.
- Enforce least privilege: review roles for SAP NetWeaver AS Java users to ensure non-administrative accounts cannot access sensitive deployment functions.
- Harden file upload configurations to prevent unauthorized files from being uploaded and executed.
- Monitor for anomalies: set up alerts for suspicious file uploads, unexpected deserialization activity, or failed/unauthorized authentication attempts.
- Conduct vulnerability scans and penetration tests to validate that the vulnerabilities have been fully remediated and that no exposed services remain unprotected.
How TPRM professionals can leverage Black Kite for this vulnerability
Black Kite published the SAP NetWeaver – Sep2025 FocusTag on September 10, 2025, with a High confidence level. TPRM teams can use this tag to:
- Identify vendors with potential exposure to vulnerable SAP NetWeaver builds, thanks to Black Kite’s asset-based intelligence (IP addresses, subdomains, and service fingerprints).
- Prioritize vendor outreach: vendors flagged by this tag should be at the top of your questionnaire or remediation queue.
- Operationalize intelligence by including the above questions in vendor risk assessments and using the provided asset details to confirm exposure.
- Track updates: since public PoCs have already emerged, if these CVEs are later confirmed as exploited or added to CISA KEV, Black Kite will update the FocusTag. Such updates help you refine urgency and vendor prioritization dynamically.
By leveraging this FocusTag, organizations can quickly zero in on vendors most likely affected by these SAP NetWeaver flaws, minimizing wasted effort and focusing security resources where they matter most.
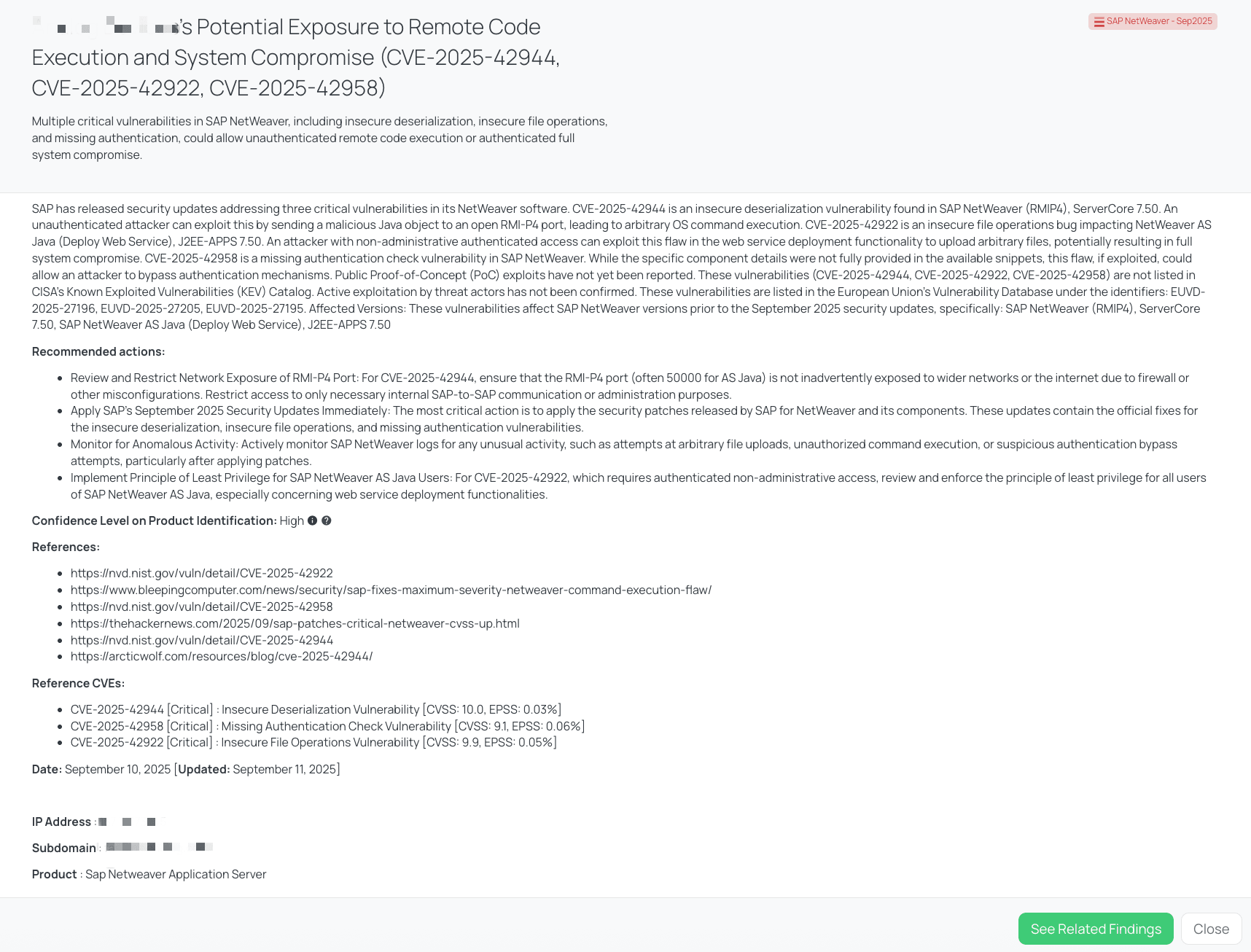
Black Kite’s SAP NetWeaver – Sep2025 FocusTag™ details critical insights on the event for TPRM professionals.
ENHANCING TPRM STRATEGIES WITH BLACK KITE’S FOCUSTAGS™
The critical vulnerabilities in SharePoint, MSSQL, and SAP NetWeaver illustrate how quickly risk can spread across third-party ecosystems when widely used enterprise technologies are affected. This is where Black Kite’s FocusTags™ provide unique value to TPRM teams.
- Immediate Vulnerability Awareness: FocusTags identify vendors potentially running vulnerable builds of high-profile technologies like SharePoint, MSSQL, and NetWeaver, enabling rapid response.
- Prioritized Risk Management: By correlating vulnerability severity (e.g., RCE with CVSS 10.0) with vendor importance, FocusTags allow security teams to focus resources where the impact would be greatest.
- Targeted Vendor Engagement: Instead of sending blanket questionnaires, TPRM professionals can use the vulnerability-specific questions provided in this week’s FocusTags to have precise and meaningful conversations with vendors.
Actionable Intelligence: FocusTags not only flag which vendors are affected but also provide associated asset information (such as IP addresses and subdomains), giving organizations a clear, technical view of where the risk resides.
By operationalizing these FocusTags, organizations reduce wasted effort, cut through questionnaire fatigue, and gain actionable visibility into which vendors need immediate attention. In an era where vulnerabilities in collaboration tools, databases, and enterprise applications can ripple across supply chains in days, Black Kite’s FocusTags™ empower TPRM programs with the intelligence needed to act decisively and effectively.
ABOUT FOCUS FRIDAY
Every week, we delve into the realms of critical vulnerabilities and their implications from a Third-Party Risk Management (TPRM) perspective. This series is dedicated to shedding light on pressing cybersecurity threats, offering in-depth analyses, and providing actionable insights.
FOCUSTAGS™ IN THE LAST 30 DAYS:
- SharePoint – Sep2025: CVE-2025-54897, CVE-2025-53760, CVE-2025-53760, Deserialization Vulnerability, Code Execution Vulnerability, Server-Side Request Forgery (SSRF) Vulnerability in Microsoft SharePoint.
- MSSQL – Sep2025: CVE-2025-47997, CVE-2025-55227, Race Condition Vulnerability, Command Injection Vulnerability in Microsoft SQL Server.
- SAP NetWeaver – Sep2025: CVE-2025-42944, CVE-2025-42922, CVE-2025-42958, Insecure Deserialization Vulnerability, Insecure File Operations Vulnerability, Missing Authentication Check Vulnerability in SAP NetWeaver.
- Django : CVE-2025-57833, SQL Injection Vulnerability in Django.
- FreePBX : CVE-2025-57819, Remote Code Execution Vulnerability in Sangoma’s FreePBX.
- Vault – Sep2025 : CVE-2025-6203, DoS Vulnerability in HashiCorp Vault.
- Citrix NetScaler – Aug2025 : CVE-2025-7775, CVE-2025-7776, CVE-2025-8424, Memory Overflow Vulnerability, Remote Code Execution Vulnerability, DoS Vulnerability, Improper Access Control Vulnerability in Citrix NetScaler ADC/Gateway.
- Salesforce Tableau – Aug2025 : CVE-2025-26496, CVE-2025-26497, CVE-2025-26498, CVE-2025-52450, CVE-2025-52451, Type Confusion Vulnerability, Remote Code Execution Vulnerability, Unrestricted File Upload Vulnerability, Path Traversal Vulnerability, Improper Input Validation Vulnerability in Salesforce Tableau.
- MadeYouReset HTTP/2 DoS Attack : CVE-2025-8671, CVE-2025-48989, CVE-2025-54500, CVE-2025-55163, CVE-2025-36047, MadeYouReset DoS Vulnerability in HTTP/2.
- Ivanti Connect Secure – Aug2025 : CVE-2025-5456, CVE-2025-5462, Out-of-bound Read Vulnerability, DoS Vulnerability, Buffer Overflow Vulnerability in Ivanti Connect Secure (ICS), Ivanti Policy Secure (IPS), Ivanti ZTA Gateway, Ivanti Neurons for Secure Access.
- PostgreSQL – Aug2025 : CVE-2025-8713, CVE-2025-8714, CVE-2025-8715, Arbitrary Code Injection Vulnerability, Exposure of Sensitive Information Vulnerability in PostgreSQL.
- Plesk Obsidian : CVE-2025-54336, Incorrect Comparison Vulnerability in Plesk Obsidian.
- Exchange Server – Aug2025 : CVE-2025-53786, CVE-2025-25005, CVE-2025-25006, CVE-2025-25007, CVE-2025-33051, Improper Authentication, Input Validation, and Information Disclosure Vulnerabilities.
- MSSQL – Aug2025 : CVE-2025-49758, CVE-2025-24999, CVE-2025-53727, CVE-2025-49759, CVE-2025-47954, Privilege Escalation and SQL Injection Vulnerabilities.
- N-able N-Central RMM : CVE-2025-8875, CVE-2025-8876, Command Injection Vulnerability in N-able N-Central RMM.
- Squid Proxy – Aug2025 : CVE-2025-54574, Buffer Overflow Vulnerability in Squid Proxy.
See Black Kite’s full CVE Database and the critical TPRM vulnerabilities that have an applied FocusTagTM at https://blackkite.com/cve-database/.
REFERENCES
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-54897
https://nvd.nist.gov/vuln/detail/CVE-2025-53760
https://nvd.nist.gov/vuln/detail/CVE-2025-54897
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-49712
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-53760
https://nvd.nist.gov/vuln/detail/CVE-2025-49712
https://nvd.nist.gov/vuln/detail/CVE-2025-47997
https://nvd.nist.gov/vuln/detail/CVE-2025-55227
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-47997
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-55227
https://thehackernews.com/2025/09/sap-patches-critical-netweaver-cvss-up.html
https://nvd.nist.gov/vuln/detail/CVE-2025-42944
https://nvd.nist.gov/vuln/detail/CVE-2025-42922