Focus Friday: TPRM Insights Into Fortinet SSO Bypass, Exchange Server Flaws, and Cacti RCE Risks
Contributor: Hakan Karabacak
INTRODUCTION
Welcome to this week’s edition of Focus Friday, where we examine some of the most impactful vulnerabilities disclosed over the past several days and assess them through a Third-Party Risk Management (TPRM) lens. This week brings critical and high-severity issues across three widely deployed technologies: Fortinet appliances using FortiCloud SSO, Microsoft Exchange Server, and the Cacti monitoring platform. Each vulnerability presents distinct risks depending on how vendors deploy, configure, and maintain these systems. Using Black Kite’s FocusTags, organizations can quickly determine which vendors are affected and prioritize outreach based on real exposure rather than assumptions or broad questionnaires. This week’s analysis highlights the operational and security implications of these vulnerabilities and outlines how TPRM teams can address them effectively.
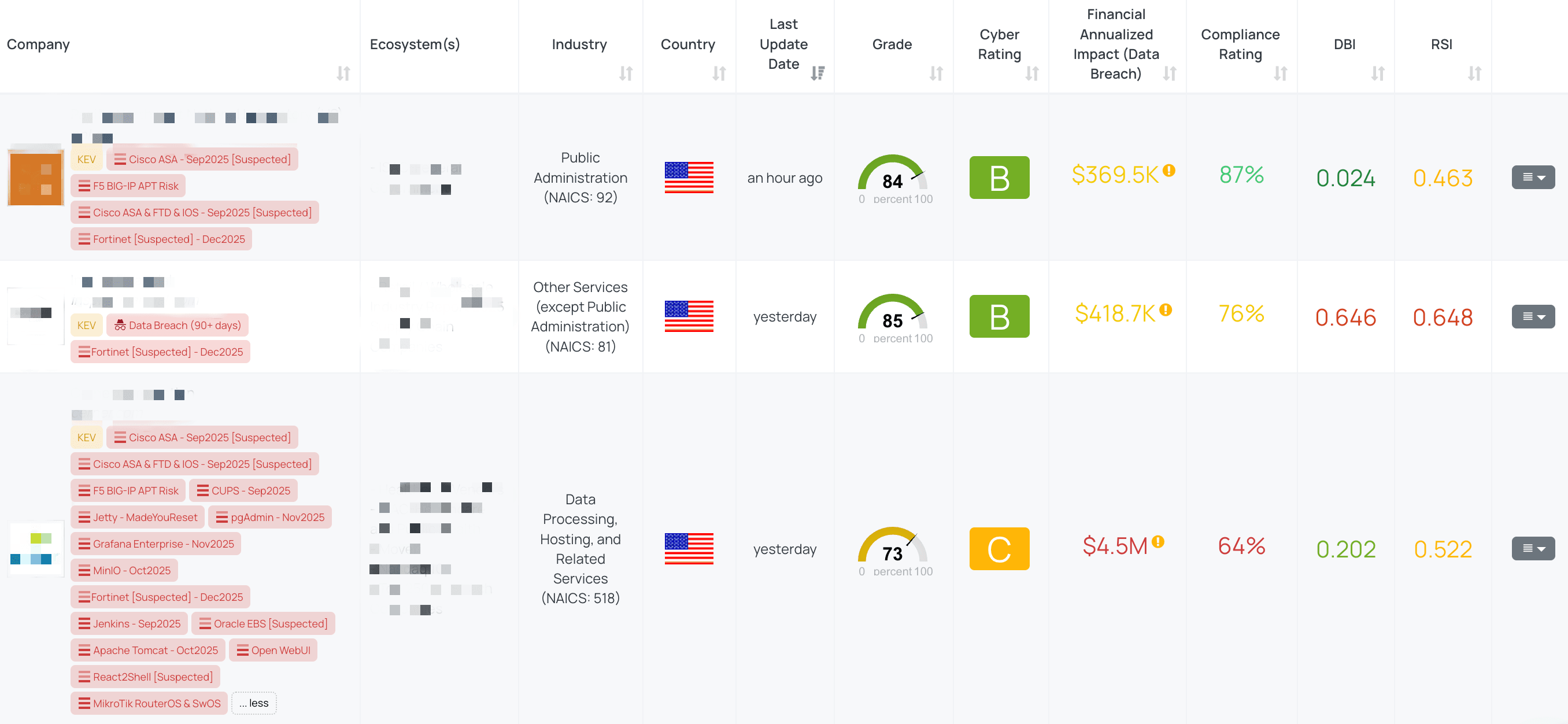
Filtered view of companies with Fortinet - Dec2025 FocusTag™ on the Black Kite platform.
CVE-2025-59718 & CVE-2025-59719 (Fortinet FortiCloud SSO Admin Bypass)
What is the Fortinet FortiCloud SSO Authentication Bypass Issue?
CVE-2025-59718 and CVE-2025-59719 are critical authentication-bypass vulnerabilities caused by improper verification of SAML cryptographic signatures within Fortinet products that support FortiCloud SSO. The flaw (CWE-347) allows an unauthenticated attacker to send a crafted SAML message and gain administrative access without valid credentials.
Both vulnerabilities were published in early December 2025 and received high severity ratings, with CVSS scores of 9.1 and 9.8. Their EPSS scores, provided in the FocusTag, are 0.05%.
Fortinet confirms that FortiCloud SSO is not enabled by default; however, the feature is automatically turned on when a device is registered to FortiCare through the GUI unless the administrator manually disables it. This behavior raises the possibility that organizations may be unaware that SSO is active.
At the time of writing, no confirmed exploitation in the wild has been reported, though public proof-of-concept exploit code exists. The vulnerabilities are not included in CISA’s Known Exploited Vulnerabilities catalog, and CISA has not issued an advisory.
These vulnerabilities are cataloged in the European Union Vulnerability Database under EUVD-2025-202198 and EUVD-2025-202191.
Why should TPRM professionals care about this?
These flaws directly affect security appliances that may serve as perimeter defenses, reverse proxies, firewalls, or management systems. If FortiCloud SSO was automatically enabled during device registration, a vendor may unknowingly expose a management interface that allows an attacker to obtain full administrative access.
For third-party ecosystems, such an event can lead to:
- Unauthorized configuration changes that weaken network segmentation or firewall rules.
- Implantation of persistent access mechanisms on a vendor’s perimeter systems.
- Use of the compromised device to pivot into internal environments, including shared customer portals or operational systems.
- Interruption of security services that customers rely upon, such as web application protections or proxy policies.
Given the critical role Fortinet appliances play in many vendors’ infrastructures, TPRM teams should evaluate whether their vendors have SSO enabled and whether they have applied the patched versions released by Fortinet.
What questions should TPRM professionals ask vendors about these vulnerabilities?
Vendors affected by these vulnerabilities should be asked targeted and technical questions, such as:
- Have you upgraded all instances of FortiOS, FortiProxy, FortiWeb, and FortiSwitch Manager to the specified patched versions or newer to mitigate the risk of CVE-2025-59718 and CVE-2025-59719?
- Can you confirm if the FortiCloud SSO login feature is enabled on your Fortinet devices? If so, have you taken steps to disable it as a critical mitigation measure against CVE-2025-59718 and CVE-2025-59719?
- Have you conducted an inventory of your Fortinet devices to determine if the FortiCloud SSO login feature is enabled, considering that this feature is automatically enabled upon device registration with FortiCare unless explicitly disabled?
- Have you implemented the recommended CLI command to disable the FortiCloud SSO login feature on your Fortinet devices as a temporary measure if immediate patching is not feasible?
Remediation recommendations for vendors subject to this risk
Vendors should take immediate steps to remove exposure associated with these CVEs:
- Apply Fortinet’s patches for FortiOS, FortiProxy, FortiWeb, and FortiSwitch Manager, upgrading to the fixed versions or newer.
- If immediate patching is not possible, temporarily disable FortiCloud SSO using the available configuration command to prevent unauthorized administrative access.
- Conduct a configuration review to confirm whether FortiCloud SSO was automatically enabled after FortiCare registration.
- Assess management interface exposure, ensuring administrative access is restricted to dedicated internal networks or VPN-protected channels.
How TPRM professionals can leverage Black Kite for this vulnerability
Black Kite published the Fortinet [Suspected] – Dec 2025 FocusTag on 2025-12-10, enabling customers to quickly identify vendors whose Fortinet appliances may be vulnerable if FortiCloud SSO is active. The tag includes asset-specific intelligence, allowing TPRM teams to pinpoint which vendor systems are hosting affected Fortinet products and whether those systems present potential exposure.
Because the tag contains version context and whether FortiCloud SSO may be enabled, customers can prioritize outreach only to vendors with meaningful risk. This prevents broad, low-value questionnaires and helps reduce response fatigue among vendors.
Black Kite customers operationalize this tag by:
- Reviewing automatically identified assets tied to at-risk Fortinet versions.
- Validating whether SSO features are active on those assets.
- Using this intelligence to guide targeted vendor communications focused on patching and configuration hardening.
![Fortinet [Suspected] - Dec2025](/_next/image?url=%2Fapi%2Fmedia%2Ffile%2F1_Fortinet%2520%255BSuspected%255D%2520-%2520Dec2025-2050x1328.png&w=3840&q=85)
Black Kite’s Fortinet - Dec2025 FocusTagTM details critical insights on the event for TPRM professionals.
CVE-2025-64666 & CVE-2025-64667 (Microsoft Exchange Server - Dec2025)
What are the new Exchange Server vulnerabilities?
Microsoft Exchange Server is affected by two newly published vulnerabilities: CVE-2025-64666 and CVE-2025-64667.
- CVE-2025-64666 is an Elevation of Privilege vulnerability caused by improper input validation (CWE-20). An attacker with low privileges and no user interaction can exploit the flaw over the network to gain a significant increase in access, resulting in high impact on confidentiality, integrity, and availability. The assigned CVSS score is 7.5.
- CVE-2025-64667 is a Spoofing vulnerability caused by user interface misrepresentation of critical information (CWE-451). It requires no privileges and no user interaction. An attacker can spoof the displayed 5322.From email address, resulting in a low integrity impact. The CVSS score is 5.3.
Both vulnerabilities were disclosed in early December 2025 with Microsoft’s monthly security release. The EPSS scores are not included in the FocusTag text and therefore not referenced.
There is no public proof-of-concept exploit and no evidence of exploitation in the wild. Neither vulnerability is listed in the CISA Known Exploited Vulnerabilities catalog, and CISA has not issued an advisory for either CVE. Both entries appear in the EUVD under identifiers EUVD-2025-202236 and EUVD-2025-202237.
Why should TPRM professionals care about these vulnerabilities?
Exchange Server is a core communication platform for many vendors, supporting email delivery, workflow systems, and customer interaction channels. This makes vulnerabilities in Exchange Server particularly impactful in a third-party context.
- If exploited, CVE-2025-64666 could allow an attacker with minimal access to obtain elevated privileges, manipulate mailbox contents, access sensitive data, alter security settings, or modify transport rules. Such an attack could have consequences beyond the vendor environment, including forged communications, exposure of confidential information, or disruption of business operations.
- CVE-2025-64667, although lower severity, could enable an attacker to spoof sender identities. In a vendor ecosystem, this could be used to send fraudulent or misleading emails that appear to originate from trusted vendor domains, potentially facilitating phishing or business email compromise.
Product | Vulnerable Versions | Patched Versions (CU and Build) |
|---|---|---|
Microsoft Exchange Server 2019 | Cumulative Update 14 (15.02.1544.x) and older | Cumulative Update 14 (15.02.1544.037) |
Microsoft Exchange Server 2019 | Cumulative Update 15 (15.02.1748.x) and older | Cumulative Update 15 (15.02.1748.042) |
Microsoft Exchange Server 2016 | Cumulative Update 23 (15.01.2507.x) and older | Cumulative Update 23 (15.01.2507.063) |
Microsoft Exchange Server Subscription Edition | RTM (15.02.2562.x) and older | RTM (15.02.2562.035) |
Table: Supported Exchange Server versions patched against CVE-2025-64666 and CVE-2025-64667
Vendors running outdated or unsupported Exchange Server versions represent heightened risk, especially when not enrolled in the Extended Security Update program. For TPRM teams, this means careful monitoring of patch levels and authentication controls on vendor-operated Exchange environments.
What questions should TPRM professionals ask vendors about these vulnerabilities?
To assess exposure, TPRM teams can ask targeted questions such as:
- Have you updated all instances of Microsoft Exchange Server 2016, 2019, and Subscription Edition to the latest fixed versions that address the Elevation of Privilege flaw (CVE-2025-64666) and the Spoofing vulnerability (CVE-2025-64667)?
- Can you confirm if you have implemented Multi-Factor Authentication (MFA) for all Exchange users, especially administrators, to mitigate the risk of CVE-2025-64666, which requires Low Privileges for exploitation?
- Have you enrolled in the Extended Security Update (ESU) program to receive necessary updates for servers running Exchange Server 2016 and 2019, which are out of support, or migrated to Exchange Server Subscription Edition (SE) as recommended?
- What specific monitoring measures have you implemented to detect unauthorized attempts to elevate privileges, particularly network activity originating from low-privileged authorized accounts, in relation to the Elevation of Privilege vulnerability (CVE-2025-64666)?
Remediation recommendations for vendors subject to this risk
To remediate or reduce exposure, vendors should:
- Apply the December 2025 security update for Exchange Server immediately and ensure systems are running the patched cumulative update and build versions.
- Confirm enrollment in the Extended Security Update (ESU) program if operating Exchange Server 2016 or 2019, which no longer receive standard support.
- Strengthen authentication by enabling multi-factor authentication and reviewing privilege assignments for Exchange user accounts.
- Validate and harden email identity mechanisms, including proper handling of displayed sender information and enforcement of DKIM, SPF, and DMARC policies.
How TPRM professionals can leverage Black Kite for this vulnerability
Black Kite published the Exchange Server – Dec 2025 FocusTag on December 10, 2025, with a VERY HIGH confidence level. This allows customers to quickly identify vendors operating Exchange environments that match the affected versions or update levels.
The tag includes asset-level intelligence, enabling TPRM teams to see which specific IP addresses or hostnames are associated with potentially vulnerable Exchange deployments. This helps focus outreach on vendors with actual exposure rather than conducting broad and unfocused questionnaires.
By operationalizing this FocusTag, TPRM teams can:
- Prioritize vendors whose Exchange Servers are externally accessible or running outdated cumulative updates.
- Validate whether vendors have applied the December 2025 fixes.
- Integrate the tag into ongoing monitoring workflows to track remediation progress.
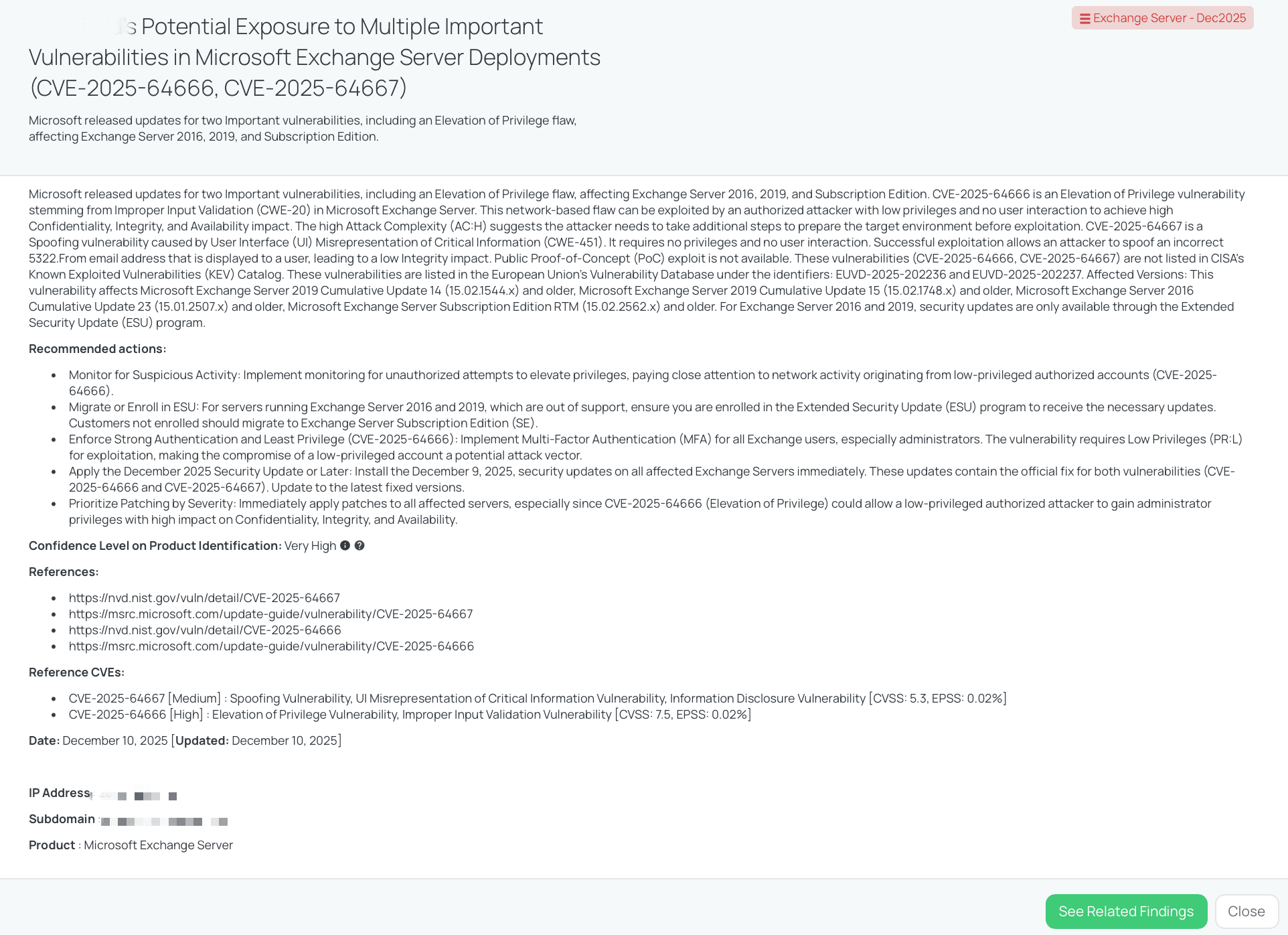
Black Kite’s Exchange Server - Dec2025 FocusTagTM details critical insights on the event for TPRM professionals.
CVE-2025-66399 (Cacti - Dec2025 SNMP Configuration RCE)
What is the Cacti Remote Code Execution Vulnerability?
CVE-2025-66399 is a high-severity Remote Code Execution vulnerability affecting Cacti installations prior to version 1.2.29. The flaw originates from improper input validation within the SNMP device configuration workflow, specifically how the snmp_community string is handled when a user with device-edit permissions saves a device configuration.
Because the sanitization regex for this field is intentionally left empty, Cacti fails to filter out dangerous characters such as newline or command-separator characters. This allows a malicious user to craft an SNMP community string containing control characters that Cacti stores directly in its database. Later, when the system uses backend SNMP tools to poll devices, these injected characters corrupt the command structure and result in execution of unintended commands with the privileges of the Cacti process.
The flaw is rated HIGH severity with a CVSS score of 7.4 and an EPSS score of 0.02. Public proof-of-concept exploit code exists, meaning the vulnerability is well understood by researchers and attackers alike. As of now, CVE-2025-66399 is not included in the CISA Known Exploited Vulnerabilities catalog, and no CISA advisory has been published. It appears in the EUVD under identifier EUVD-2025-200287. The vulnerability was disclosed in early December 2025.
Why should TPRM professionals care about this vulnerability?
Cacti is commonly used by vendors to monitor critical systems, network devices, and infrastructure. A compromise of the Cacti server can disrupt monitoring operations and undermine the trustworthiness of alerts and performance data. Because the server often has broad visibility and may hold sensitive configuration details, a successful exploitation of CVE-2025-66399 enables:
- Complete takeover of the monitoring server through remote command execution.
- Interference with monitoring integrity, potentially hiding malicious activity or degrading operational awareness.
- Deployment of persistent backdoors or additional malware through the privileged execution context of the Cacti process.
- Lateral movement across the vendor’s internal network, since monitoring servers often sit in privileged network segments.
These risks directly translate into exposure for downstream customers who rely on vendors to maintain secure and reliable monitoring environments. For TPRM programs, a vendor operating an outdated or misconfigured Cacti deployment represents an elevated risk.
What questions should TPRM professionals ask vendors about this vulnerability?
To evaluate exposure and verify remediation efforts, TPRM teams can ask:
- Can you confirm if you have upgraded all instances of Cacti to version 1.2.29 or later to mitigate the risk of CVE-2025-66399?
- Have you implemented robust monitoring for your Cacti server to detect unusual process execution, unauthorized file writes, or unexpected outgoing network connections, which could indicate successful exploitation of CVE-2025-66399?
- Have you restricted user permissions to enforce the principle of least privilege, limiting device-edit permissions to only trusted administrators who absolutely require them, as exploitation of CVE-2025-66399 requires an authenticated user with such privileges?
- Have you taken any additional measures to prevent command injection via the SNMP community string, beyond the recommended upgrade to Cacti version 1.2.29 or later?
Remediation recommendations for vendors subject to this risk
To fully remediate or reduce the risk associated with CVE-2025-66399, vendors should:
- Upgrade immediately to Cacti version 1.2.29 or later, which includes the fix for the vulnerable SNMP community string handling.
- Restrict device-edit permissions and apply the principle of least privilege, ensuring only trusted administrators can modify SNMP device configurations.
- Audit existing SNMP community strings in the database, removing any entries that contain control characters, multi-line inputs, or suspicious formatting.
- Enable system-level monitoring on the Cacti server to detect anomalous behavior, such as unexpected command executions or unauthorized modifications.
How TPRM professionals can leverage Black Kite for this vulnerability
Black Kite published the Cacti – Dec2025 FocusTag on December 5, 2025, providing customers with high-confidence intelligence on vendors that may be using vulnerable Cacti versions. Through asset-level visibility, Black Kite identifies which vendor systems expose Cacti hosts and whether those systems appear aligned with versions impacted by CVE-2025-66399.
This allows TPRM professionals to:
- Immediately pinpoint vendors running pre-1.2.29 Cacti installations.
- Prioritize follow-up with vendors whose Cacti servers appear externally reachable or at-risk based on behavioral signals.
- Reduce unnecessary questionnaires by engaging only with vendors that have a meaningful association with the vulnerable technology.

Black Kite’s Cacti - Dec2025 FocusTagTM details critical insights on the event for TPRM professionals.
Enhancing Vendor Risk Decisions With Black Kite's FocusTags
Black Kite’s FocusTags play a central role in strengthening TPRM programs, particularly when new vulnerabilities emerge across infrastructure, email systems, and monitoring platforms. The tags issued this week for Fortinet, Exchange Server, and Cacti offer targeted insights that help organizations respond with precision and speed. Rather than assessing hundreds or thousands of vendors manually, FocusTags allow security and risk teams to concentrate efforts where exposure is confirmed or strongly suspected.
FocusTags provide:
Rapid Identification of At-Risk Vendors
The moment a vulnerability is disclosed, FocusTags highlight which vendors operate potentially affected assets. This removes the guesswork and significantly reduces the time required to launch an informed response.
Risk-Aligned Prioritization
With visibility into both vendor importance and vulnerability severity, TPRM teams can focus first on exposures that carry the greatest business or operational impact, such as administrative bypasses in perimeter devices or privilege escalation in email systems.
Purposeful Vendor Engagement
Instead of sending broad, duplicative questionnaires, risk teams can ask specific, technically relevant questions grounded in the vulnerability details. This approach reduces friction and drives more meaningful exchanges with vendors.
Improved Understanding of the Threat Landscape
By consolidating asset data, vulnerability intelligence, and vendor exposure, FocusTags help organizations maintain a clear view of emerging risks. This context strengthens overall cybersecurity decision-making and supports proactive mitigation strategies.
As demonstrated by this week’s vulnerabilities in Fortinet, Exchange Server, and Cacti, Black Kite’s FocusTags transform complex vulnerability intelligence into actionable guidance. They give TPRM teams the clarity needed to respond rapidly and effectively, ensuring vendor ecosystems remain resilient even as high-profile risks continue to evolve.
About Focus Friday
Every week, we delve into the realms of critical vulnerabilities and their implications from a Third-Party Risk Management (TPRM) perspective. This series is dedicated to shedding light on pressing cybersecurity threats, offering in-depth analyses, and providing actionable insights.
FocusTags in the Last 30 Days:
- Fortinet [Suspected] – Dec2025 : CVE-2025-59718, CVE-2025-59719, Administrative Authentication Bypass via SAML Forgery in Fortinet FortiCloud SSO.
- Exchange Server – Dec2025 : CVE-2025-64666, CVE-2025-64667, Elevation of Privilege and Email Spoofing Vulnerabilities in Microsoft Exchange Server.
- Cacti – Dec2025 : CVE-2025-66399, Remote Code Execution Vulnerability via SNMP Community String Injection in Cacti.
- React Server Components (RSC) [Suspected] : CVE-2025-55182, Remote Code Execution Vulnerability in React Server Components.
- Mixpanel Clients : Assessing the Potential Impact of Client Data Exposure in Mixpanel.
- SonicWall SSL VPN – Nov2025 : CVE-2025-40601, Pre-Authentication Stack-Based Buffer Overflow Vulnerability in SonicWall SonicOS SSLVPN Service Leading to Denial of Service.
- Grafana Enterprise – Nov2025 : CVE-2025-41115, Incorrect Privilege Assignment Vulnerability Allowing Privilege Escalation and User Impersonation via SCIM Provisioning in Grafana Enterprise.
- Apache SkyWalking : CVE-2025-54057, Stored Cross-Site Scripting (XSS) Vulnerability Allowing Persistent Script Injection in Apache SkyWalking Monitoring Dashboards.
- Gainsight Client – Nov2025 : Integration-Token Abuse Incident, Unauthorized Access and Potential Data Exfiltration Through Compromised OAuth Tokens in Gainsight–Salesforce Connected Applications.
- FortiWeb [Suspected] : CVE-2025-64446, CVE-2025-58034, Authentication Bypass Vulnerability, Path Traversal Vulnerability, OS Command Injection Vulnerability in Fortinet FortiWeb Web Application Firewall.
- SolarWinds Serv-U - Nov2025 : CVE-2025-40547, CVE-2025-40548, CVE-2025-40549, Logic Error Vulnerability, Improper Authorization Vulnerability, Path Traversal Vulnerability, Remote Code Execution Vulnerabilities in SolarWinds Serv-U.
- OAuth2 Proxy : CVE-2025-64484, Improper Neutralization Of HTTP Headers For Scripting Syntax Vulnerability, Header Smuggling Vulnerability, Potential Privilege Escalation Vulnerability in OAuth2 Proxy.
- pgAdmin - Nov2025 : CVE-2025-12762, CVE-2025-12763, CVE-2025-12764, CVE-2025-12765, Remote Code Execution Vulnerability, Command Injection Vulnerability, LDAP Injection Vulnerability, TLS Certificate Verification Bypass Vulnerability in pgAdmin.
- W3 Total Cache - Nov2025 : CVE-2025-9501, Command Injection Vulnerability, Remote Code Execution Vulnerability in W3 Total Cache WordPress Plugin.
- Microsoft SharePoint - Nov2025 : CVE-2025-62204, Deserialization of Untrusted Data Vulnerability, Remote Code Execution Vulnerability in Microsoft Office SharePoint.
- MSSQL - Nov2025 : CVE-2025-59499, Improper Neutralization of Special Elements in SQL Commands, SQL Injection Vulnerability, Privilege Escalation Vulnerability in Microsoft SQL Server.
- Elastic Kibana - Nov2025 : CVE-2025-37734, CVE-2025-59840, Server-Side Request Forgery (SSRF) Vulnerability, DOM-based Cross-site Scripting (XSS) Vulnerability, Improper Input Validation Vulnerability in Elastic Kibana.
- Django - Nov2025 : CVE-2025-59681, CVE-2025-59682, SQL Injection Vulnerability, Directory Traversal Vulnerability, Improper Input Sanitization Vulnerability in Django Web Framework.
- Open WebUI - Nov2025 : CVE-2025-64495, Stored DOM XSS Vulnerability, Account Takeover Vulnerability, Remote Code Execution Vulnerability in Open WebUI.
- MOVEit - Oct2025 : CVE-2025-10932, Uncontrolled Resource Consumption Vulnerability, Denial of Service Vulnerability in Progress MOVEit Transfer.
- Redis - Nov2025 : CVE-2025-62507, Improper Input Validation Vulnerability, Stack-based Buffer Overflow Vulnerability, Remote Code Execution Vulnerability in Redis.
- Control Web Panel (CWP) : CVE-2025-48703, Remote Code Execution Vulnerability, OS Command Injection Vulnerability in CentOS Control Web Panel.
See Black Kite’s full CVE Database and the critical TPRM vulnerabilities that have an applied FocusTagTM at https://blackkite.com/cve-database/.
References
https://securityonline.info/critical-fortinet-flaw-risks-unauthenticated-admin-bypass-via-forticloud-sso-saml-forgery/
https://fortiguard.fortinet.com/psirt/FG-IR-25-647
https://nvd.nist.gov/vuln/detail/CVE-2025-59719
https://nvd.nist.gov/vuln/detail/CVE-2025-59718
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-64666
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-64667
https://www.cve.org/CVERecord?id=CVE-2025-64666
https://www.cve.org/CVERecord?id=CVE-2025-64667
https://securityonline.info/high-severity-cacti-flaw-cve-2025-66399-risks-remote-code-execution-via-snmp-community-string-injection/
https://nvd.nist.gov/vuln/detail/CVE-2025-66399
https://github.com/Cacti/cacti/security/advisories/GHSA-c7rr-2h93-7gjf