Focus Friday: Critical Third-Party Risks In Mikrotik Routeros, Apache Tomcat, Hashicorp Vault, and Litespeed Plugin
Welcome to this week’s Focus Friday, where we analyze critical and high-impact vulnerabilities from a Third-Party Risk Management (TPRM) perspective. This edition highlights four major risks affecting widely deployed technologies — MikroTik RouterOS & SwOS, Apache Tomcat, HashiCorp Vault, and the LiteSpeed Cache plugin for WordPress.
Each of these vulnerabilities underscores how infrastructure and application-layer weaknesses can cascade into third-party exposure. From a router misconfiguration that leaks administrative credentials, to an authentication bypass in a secret management system, to path traversal in a server platform, and even a reflected XSS flaw in a caching plugin — these incidents reveal how interconnected today’s vendor ecosystems truly are.
In the following sections, we explore each vulnerability, its impact, and how TPRM professionals can leverage Black Kite’s FocusTags™ to pinpoint and mitigate vendor exposure efficiently.
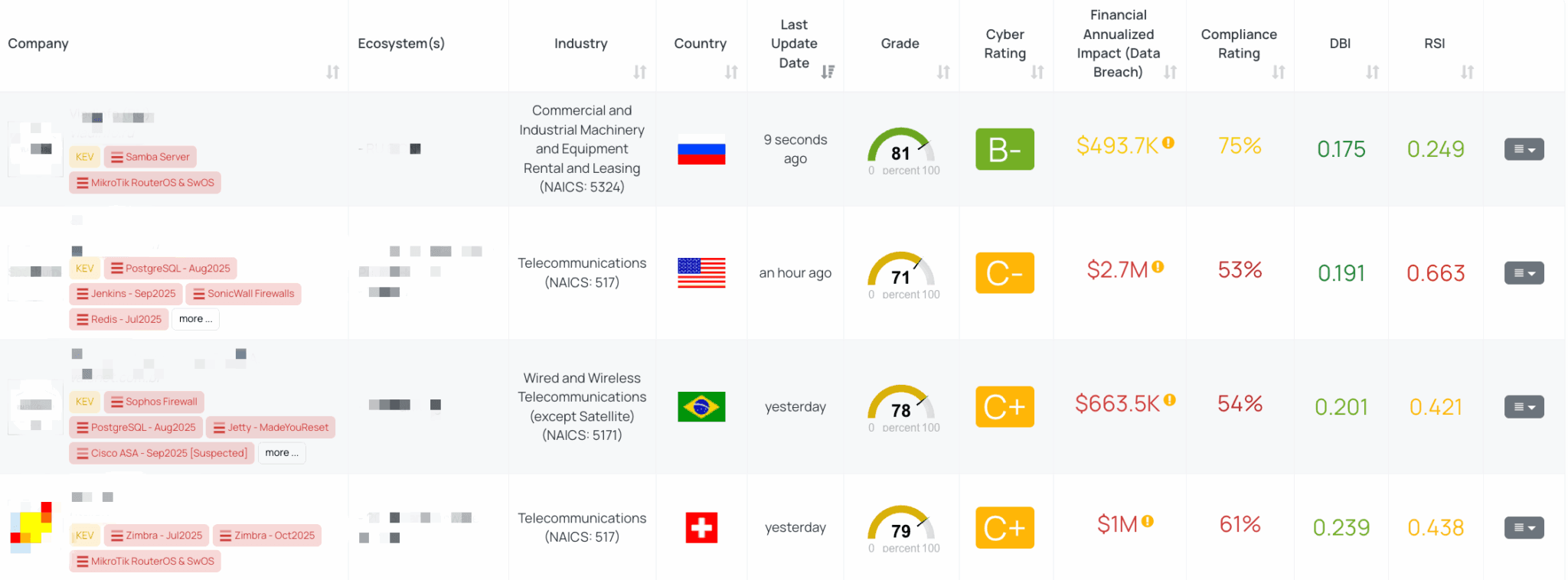
Filtered view of companies with MikroTik RouterOS & SwOS FocusTag™ on the Black Kite platform.
CVE-2025-61481 — MIKROTIK ROUTEROS & SWOS WEBFIG MANAGEMENT INTERFACE
WHAT IS CVE-2025-61481?
CVE-2025-61481 is a critical vulnerability (CVSS 10.0, EPSS 0.02%) affecting MikroTik RouterOS (up to version 7.14.2) and SwOS (up to version 2.18) through the WebFig management interface. The issue stems from insecure default configurations where WebFig initializes with HTTP enabled and without redirection to HTTPS. After a factory reset, the entire management interface—including the login page and scripts—loads over cleartext HTTP, exposing credentials during authentication.
An on-path attacker can intercept and potentially modify management traffic and credentials through a Man-in-the-Middle (MITM) attack. In certain configurations, malformed packets sent to the MikroTik Discovery Protocol (MNDP) service can trigger disclosure of the router’s configuration, including plaintext administrator passwords. Public exploit activity has been observed, and independent researchers reported active exploitation beginning in late October 2025.
At the time of this writing, the vulnerability is not listed in CISA’s Known Exploited Vulnerabilities catalog.
WHY SHOULD TPRM PROFESSIONALS CARE ABOUT THIS VULNERABILITY?
Routers and network edge appliances like MikroTik devices often serve as high-trust infrastructure within a vendor’s network. A compromise at this layer enables an attacker to intercept traffic, steal administrative credentials, deploy malware, or pivot deeper into internal systems.
For organizations monitoring vendors, this flaw is significant because it can expose vendor management interfaces to credential theft or unauthorized access. If a vendor’s network is managed through an affected MikroTik device, attackers could potentially manipulate configurations, reroute traffic, or compromise VPN gateways and remote-access systems.
This is especially concerning for vendors providing managed services, connectivity, or remote work infrastructure. A compromised MikroTik router in a vendor’s environment could directly threaten downstream clients by enabling lateral movement into trusted corporate networks.
WHAT QUESTIONS SHOULD TPRM PROFESSIONALS ASK VENDORS ABOUT THIS VULNERABILITY?
Here are focused, evidence-based questions for assessing vendor exposure:
- Which versions of MikroTik RouterOS and SwOS are currently deployed in your environment, and have all devices been updated beyond versions 7.14.2 and 2.18?
- Is the WebFig interface accessible over the Internet or from untrusted networks? If so, is HTTPS enforced and HTTP fully disabled?
- After factory resets or redeployments, what configuration policies ensure HTTPS is automatically enforced and management interfaces remain isolated?
- Have you rotated administrator credentials following the disclosure of CVE-2025-61481, and do you maintain logs or alerts for attempts to access management interfaces over HTTP?
REMEDIATION RECOMMENDATIONS FOR VENDORS
Vendors should take the following technical actions immediately:
- Apply security updates: Upgrade MikroTik RouterOS and SwOS to the latest stable versions that address CVE-2025-61481.
- Disable HTTP access: Enforce HTTPS-only communication for WebFig and remove any fallback to unencrypted HTTP.
- Isolate management interfaces: Restrict WebFig access to a dedicated management VLAN or VPN that is inaccessible to untrusted users.
- Disable the MikroTik Discovery Protocol (MNDP): Turn off MNDP on all interfaces, particularly WAN and bridge interfaces, to prevent configuration broadcasts.
- Rotate credentials: Assume administrator passwords may have been exposed and change them immediately after patching. Remove or disable unused accounts.
- Implement secure administration practices: Use SSH or VPN for remote management and avoid performing administrative actions over public or shared networks.
- Review and monitor logs: Watch for unauthorized access attempts, configuration changes, or unexpected broadcasts from affected devices.
HOW TPRM PROFESSIONALS CAN LEVERAGE BLACK KITE FOR THIS VULNERABILITY
The “MikroTik RouterOS & SwOS” FocusTag was published by Black Kite on October 30, 2025 (Confidence: Very High; Expiration: January 31, 2026).
Using this tag, TPRM professionals can:
- Identify vendors operating MikroTik RouterOS or SwOS devices running affected versions.
- Access asset-level evidence, including IPs, banners, and subdomain data, to determine whether vendors expose WebFig interfaces via HTTP.
- Prioritize outreach to vendors with Internet-facing management endpoints, assigning remediation SLAs proportional to risk.
- Automate vendor assessments by generating focused questionnaires and tracking patch verification within risk workflows.
- Use the tag’s expiration and version metadata to schedule follow-up scans and confirm that vulnerable assets are remediated or isolated.

Black Kite’s MikroTik RouterOS & SwOS FocusTag™ details critical insights on the event for TPRM professionals.
CVE-2025-55752, CVE-2025-55754, CVE-2025-61795 — APACHE TOMCAT
WHAT VULNERABILITIES ARE INCLUDED IN THIS FOCUSTAG AND WHEN WERE THEY PUBLISHED?
This FocusTag covers three Apache Tomcat vulnerabilities published on 27–28 October 2025: CVE-2025-55752 (URL rewrite / path-traversal regression — CVSS 7.5, EPSS 0.15%), CVE-2025-55754 (ANSI escape / console injection — CVSS 9.6, EPSS 0.04%), and CVE-2025-61795 (multipart upload temporary-file cleanup → DoS — CVSS 5.3, EPSS 0.04%). Black Kite published the tag on 28 October 2025, marked as Confidence = HIGH, with expiration 31 January 2026.
Short technical summaries:
- CVE-2025-55752: A regression in URL rewrite normalization can allow bypass of security constraints (for example /WEB-INF/ and /META-INF/) under certain rewrite rules. If HTTP PUT is enabled and a rewrite rule manipulates the request URI, an attacker could upload files into protected locations — creating a possible RCE path in those specific configurations. Patched in Tomcat 11.0.11+, 10.1.45+, 9.0.109+.
- CVE-2025-55754: Improper handling of ANSI escape sequences in logs/console output. On Windows consoles (or other environments that process ANSI sequences), specially crafted URLs could inject sequences that affect console display or clipboard content and potentially trick an administrator into running attacker-controlled commands. Patched in 11.0.11+, 10.1.45+, 9.0.109+.
- CVE-2025-61795: Temporary multipart upload parts are not reliably cleaned up on error; under certain JVM/GC configurations and high load, temporary storage can be exhausted, causing service denial. Patched in 11.0.12+, 10.1.47+, 9.0.110+.
At the time of tagging: no widespread public PoCs or confirmed large-scale in-the-wild exploitation were observed, and these CVEs were not listed in CISA’s KEV catalog during the check. EPSS values above are taken from the FocusTag text.
WHY SHOULD TPRM PROFESSIONALS CARE?
Apache Tomcat is a common application server used across many third-party vendors. These three issues present different but complementary risks that matter to third-party risk management:
- Configuration-dependent RCE risk (CVE-2025-55752): Vendors that enable HTTP PUT or use complex rewrite rules are at higher risk of remote compromise, which can lead to data exposure or application takeover.
- Human-in-the-loop administrative risk (CVE-2025-55754): Console log injection can be exploited to manipulate administrator workflows, enabling social-engineering-driven command execution or misconfiguration.
- Operational continuity risk (CVE-2025-61795): Multipart upload cleanup failures can cause temporary storage exhaustion and service outages — a significant SLA and availability concern for vendors handling large or frequent uploads.
Therefore, TPRM assessments should go beyond version checks and evaluate configuration profiles, upload pathways, admin practices, and temp-storage monitoring for each vendor.
WHAT TARGETED QUESTIONS SHOULD TPRM PROFESSIONALS ASK VENDORS?
Use these focused questions to obtain evidence-backed answers:
- Have you updated all instances of Apache Tomcat to versions 11.0.12, 10.1.47, or 9.0.110 (or newer) to mitigate the risk of CVE-2025-55752, CVE-2025-55754, and CVE-2025-61795?
- Can you confirm if you have reviewed and adjusted your JVM settings related to garbage collection and temporary file handling to prevent potential denial-of-service conditions as per the recommendation for CVE-2025-61795?
- Have you inspected your Tomcat configurations to ensure that HTTP PUT requests are appropriately restricted to trusted users, and reviewed any URL rewrite rules that manipulate the request URI, especially if PUT requests are enabled, as recommended for CVE-2025-55752?
- For CVE-2025-55754, have you implemented measures to caution administrators running Tomcat in Windows console environments about the risk of ANSI escape sequence injection through specially crafted URLs in log messages?
REMEDIATION RECOMMENDATIONS FOR VENDORS (TECHNICAL AND PRIORITIZED)
- Upgrade immediately to patched Tomcat releases: for CVE-2025-55752/55754 use 11.0.11+, 10.1.45+, 9.0.109+; for CVE-2025-61795 use 11.0.12+, 10.1.47+, 9.0.110+. Verify upgrades in staging before production rollout.
- Disable or restrict HTTP PUT unless strictly required. If PUT is necessary, enforce strong authentication, IP allowlists, mTLS, and robust logging/alerting for PUT activity.
- Review and harden rewrite rules: simplify or remove risky normalization/decoding behaviors and avoid transformations that could expose protected paths.
- Sanitize console/log output: do not display raw request data in interactive admin consoles; escape or strip ANSI/control characters before rendering; harden clipboard workflows.
- Harden multipart handling: place upload temp files on dedicated, monitored volumes with quotas and alerts; implement immediate cleanup on error paths and consider code hooks for synchronous deletion; tune JVM/GC to reduce reliance on delayed cleanup.
- Edge/WAF protections: add WAF rules to detect/block suspicious PUTs and unusual rewrite patterns; treat internet-facing Tomcat instances as high priority.
- Monitoring and detection: alert on new files in protected paths, anomalous PUT attempts, rapid growth in temp directory usage, and GC-related memory pressure.
HOW TPRM PROFESSIONALS CAN LEVERAGE BLACK KITE FOR THIS FOCUSTAG
- Tag metadata & timeline: Black Kite’s “Apache Tomcat – Oct2025” tag (published 28 Oct 2025, expires 31 Jan 2026, Confidence = HIGH) bundles these CVEs and their remediation guidance for immediate triage use.
- Targeted discovery: Black Kite identifies which vendors in your portfolio run the affected Tomcat versions and surfaces externally observable assets (IP addresses, subdomains, version banners) that match the vulnerable ranges — enabling focused outreach rather than blanket questionnaires.
- Asset-level evidence: Where available, Black Kite links vulnerable assets to vendor records (IP + banner + version), so you can demand remediation with concrete evidence.
- Operational playbook: Use the tag to auto-generate a short vendor questionnaire (the targeted questions above), attach scan evidence to vendor records, set SLAs by exposure level (internet-facing highest), and schedule re-discovery based on the tag’s expiration/update metadata.
QUICK CHECKLIST (FOR RAPID TRIAGE)
- Treat vendors running affected Tomcat versions as potentially at-risk, but prioritize those with: internet-facing Tomcat instances, enabled HTTP PUT, complex rewrite rules, services that accept large/multipart uploads, or admin consoles that render logs interactively.
- Confirm patch status and obtain configuration evidence.
- For high-exposure vendors, require immediate mitigation (disable PUT, WAF rules) and a short remediation SLA.
- Maintain monitoring for new public PoCs or any additions to CISA KEV; re-run discovery after vendors report patching.

Black Kite’s Apache Tomcat – Oct2025 FocusTag™ details critical insights on the event for TPRM professionals.
CVE-2025-12044 & CVE-2025-11621 — HASHICORP VAULT
WHAT ARE THESE VAULT VULNERABILITIES, AND WHEN WERE THEY PUBLISHED?
This FocusTag groups two high-severity Vault issues disclosed in late October 2025: CVE-2025-12044 — an unauthenticated JSON-based Denial-of-Service (DoS) caused by a rate-limit regression (CVSS 7.5, EPSS 0.07%) — and CVE-2025-11621 — an AWS Auth authentication-bypass that enables cross-account role-name collisions or wildcard abuse (CVSS 8.1, EPSS 0.06%). HashiCorp’s advisories and public write-ups appeared in October 2025; Black Kite published the “Vault – Oct2025” tag on 28 Oct 2025 (Confidence: HIGH, expiration: 31 Jan 2026).
Quick technical summary
- CVE-2025-12044 (DoS) — A regression introduced after an earlier fix caused Vault to parse JSON payloads before applying rate-limits, allowing attackers to submit many large but valid JSON requests that consume CPU/memory until the service becomes unresponsive. Patched in Vault Community 1.21.0 and corresponding Enterprise fixes.
- CVE-2025-11621 (AWS Auth bypass) — When Vault’s AWS Auth method uses bound_principal_iam entries with identical role names across accounts or wildcards (e.g., arn:aws:iam::*:role/ExampleRole), the internal cache key did not include sufficient account-identifying information. A successful authentication by one principal could cause the cached authentication result to be reused for a different principal that shares the same role name or matches the wildcard, allowing an unauthorized principal to obtain a Vault token intended for another entity. Patched in Community 1.21.0 and Enterprise 1.16.27, 1.19.11, 1.20.5, 1.21.0. The root cause is a cache key construction error (CWE-288).
- PoC status & KEV: Public exploit code is not known to be widely published. The ZeroPath analysis (Oct 23, 2025) provides a technical explanation of the AWS Auth cache flaw and reproduction logic, but no weaponized PoC was broadly reported at disclosure. These CVEs were not listed in CISA’s KEV catalog at the time of the initial checks.
WHY SHOULD TPRM PROFESSIONALS CARE ABOUT THESE VAULT VULNERABILITIES?
Vault is a central secrets-management service for many vendors. These vulnerabilities threaten both availability (service outage or degraded automation if Vault becomes unresponsive) and confidentiality/authentication (unauthorized retrieval of secrets via AWS Auth bypass). For third-party risk teams, the key concerns are:
- Business continuity: Outage of a vendor’s Vault can break CI/CD, automated deployments, certificate renewal, and secrets retrieval — causing downstream outages for your organization.
- Cross-account exposure: Misconfigured AWS Auth bindings or wildcard use can allow principals from an unrelated AWS account to obtain Vault tokens and read secrets, potentially exposing credentials, keys, or other sensitive artifacts.
- Configuration sensitivity: The risk depends heavily on vendor configuration: whether they use AWS Auth, whether wildcards or identical role names exist across accounts, and whether Vault endpoints are internet-facing or integrated into critical automation.
TPRM assessments must therefore verify both patch status and configuration hygiene, not just version numbers.
WHAT TARGETED QUESTIONS SHOULD TPRM PROFESSIONALS ASK VENDORS?
Use these focused questions to get verifiable evidence:
- Have you upgraded all instances of HashiCorp Vault Community Edition to version 1.21.0 or later and HashiCorp Vault Enterprise to versions 1.16.27, 1.19.11, 1.20.5, or 1.21.0 or later to mitigate the risk of CVE-2025-12044 and CVE-2025-11621?
- Have you reviewed your AWS Auth Configurations for instances where the same IAM role name exists across different accounts to mitigate the risk of CVE-2025-11621?
- Have you evaluated and removed any wildcard () usage in the `bound_principal_iam` configuration within Vault’s AWS Auth method to mitigate potential exposure to CVE-2025-11621?
- Can you confirm if you have implemented measures to prevent unauthenticated JSON denial-of-service attacks, specifically in relation to the vulnerability CVE-2025-12044?
REMEDIATION RECOMMENDATIONS FOR VENDORS (TECHNICAL, PRIORITIZED)
Provide these actions and require evidence of implementation:
- Upgrade Vault to Community 1.21.0 or the appropriate Enterprise releases (1.16.27, 1.19.11, 1.20.5, 1.21.0). Validate in staging and test authentication and automation flows.
- Harden AWS Auth bindings: Remove wildcard entries from bound_principal_iam. Replace wildcards and ambiguous role-name matches with explicit ARNs that include account IDs, or use bound_principal_arn with strict account scoping. Audit for identical role names across accounts and rename roles where collisions exist.
- Edge rate-limiting & request-size controls: Enforce request-size and rate limits at the edge or WAF so that Vault never parses very large JSON payloads before rate-limit checks. Implement bot-protection and request-throttling rules.
- Monitoring & incident playbooks: Add alerts for sustained increases in CPU/memory tied to request processing, and monitor request-size distributions and error rates. Prepare fallbacks for critical systems that rely on Vault (e.g., cached secrets with short TTLs or emergency rotation/playbook).
- Test mitigations: Conduct non-destructive tests to validate that wildcards and cross-account login attempts are blocked post-mitigation, and that rate-limits prevent DoS amplification.
- Least privilege & secrets hygiene: Ensure minimal exposure of high-value secrets and enforce strict ACLs for paths provisioned to AWS Auth-authenticated tokens.
HOW TPRM PROFESSIONALS CAN LEVERAGE BLACK KITE FOR THIS FOCUSTAG
- Tag metadata: Black Kite’s “Vault – Oct2025” tag (published 28 Oct 2025, Confidence: HIGH, expires 31 Jan 2026) packages these CVEs and recommended actions so you can set triage priority and scanning cadence automatically.
- Evidence-driven scope reduction: Black Kite discovers which vendors in your portfolio run affected Vault versions and surfaces externally observable evidence (banners, endpoints). This lets you target only vendors that actually expose vulnerable versions or endpoints, reducing questionnaire fatigue.
- Asset-level context: Where available, Black Kite links IPs, hostnames, and version artifacts to vendor records so you can demand remediation with concrete indicators. For Vault, this allows prioritizing vendors whose Vault endpoints are internet-reachable or integrated into critical automation pipelines.
- Operational playbook & automation: Use the tag to auto-generate the vendor questionnaire (the targeted questions above), attach scan artifacts to vendor tickets, set SLAs by exposure level (internet-facing = highest), and trigger re-discovery after vendors report patching.
PoC and threat activity notes
- PoC availability: The ZeroPath analysis (Oct 23, 2025) provides a technical breakdown of CVE-2025-11621, clearly describing the cache key construction flaw and offering reproduction logic for defenders and red-team testing. That analysis confirms the root cause is the missing account identifier in the cache key (CWE-288). As of disclosure, no widely weaponized exploit code was reported.
- Active exploitation & KEV status: There were no confirmed reports of large-scale exploitation at disclosure, and these CVEs were not listed in CISA’s KEV catalog at the time of initial checks. Continue to monitor threat feeds and KEV for changes.
Quick triage checklist (one-line actions)
- Confirm vendor Vault version and provide patch evidence (1.21.0+ or fixed Enterprise builds).
- For AWS Auth: remove wildcards from bound_principal_iam and validate account-ID scoping.
- For DoS: enforce heavy request-size and rate-limits at edge/WAF and monitor request-size distributions.
- Require artifacted evidence (configs, logs, tickets) before closing vendor remediation.
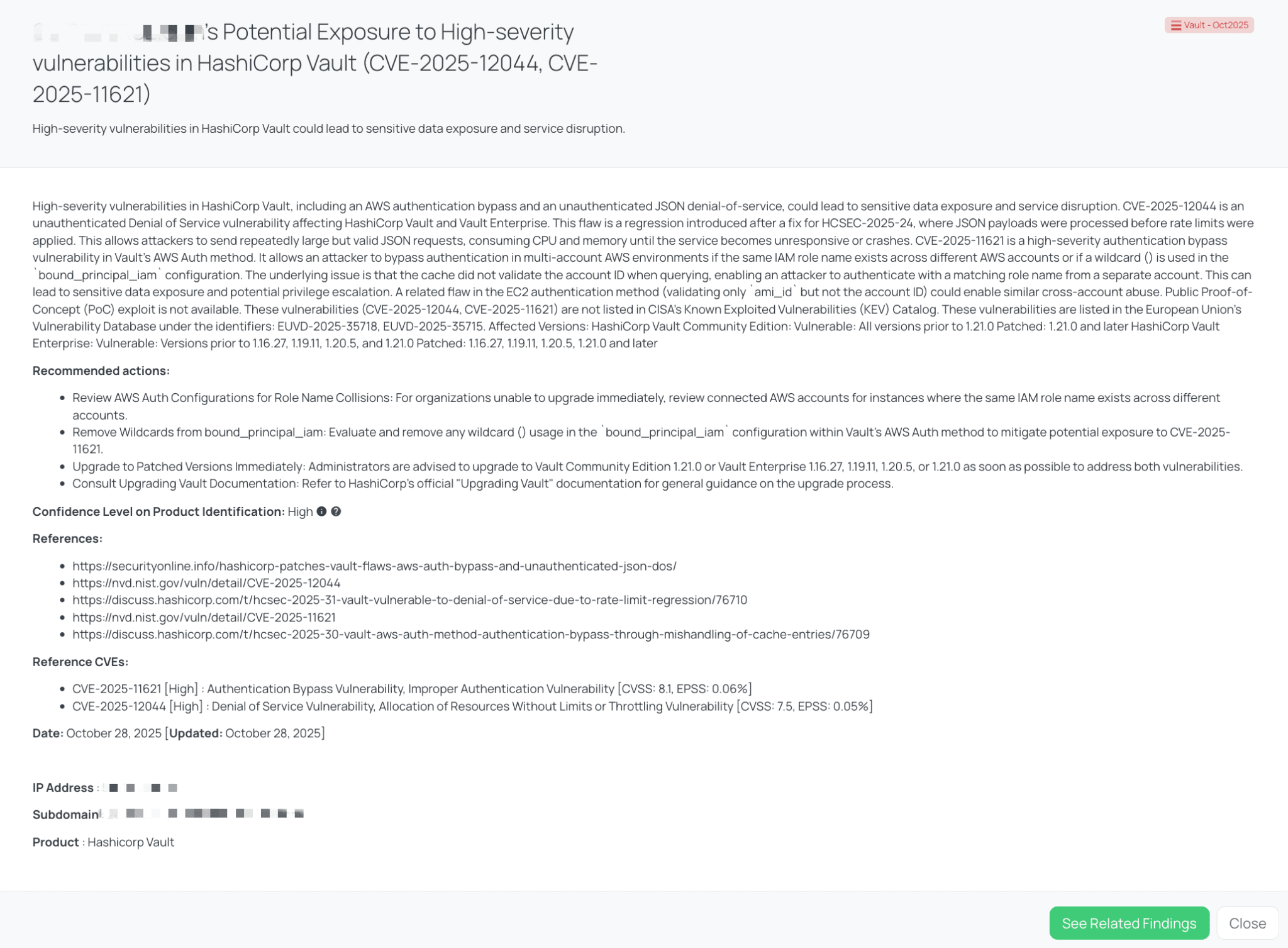
Black Kite’s Vault – Oct2025 FocusTag™ details critical insights on the event for TPRM professionals.
CVE-2025-12450 — LITESPEED CACHE FOR WORDPRESS
WHAT IS THIS VULNERABILITY?
The vulnerability addressed by CVE-2025-12450 is a Reflected Cross-Site Scripting (XSS) flaw in the LiteSpeed Cache plugin for WordPress. An unauthenticated attacker can craft a malicious link that, when clicked by a victim, causes arbitrary JavaScript to run in the victim’s browser. The danger is higher if the targeted user is an administrator: the attacker may steal session cookies, hijack the session, create new admin accounts, inject backdoors, or fully compromise the site. The FocusTag text lists this vulnerability as Medium severity (CVSS 6.1, EPSS 0.07%). The vulnerable versions are all up to and including 7.5.0.1; remediation is available in version 7.6+. Although no public Proof of Concept (PoC) exploit is documented at the time of the tag, the plugin in question has widespread deployment (millions of sites), making it a high-profile risk. The vulnerability was not listed in the Cybersecurity & Infrastructure Security Agency (CISA) Known Exploited Vulnerabilities (KEV) catalog at the time of the tagging.
WHY SHOULD TPRM PROFESSIONALS CARE?
From a third-party risk management (TPRM) standpoint, this plugin vulnerability is relevant because many vendors and service providers host WordPress sites and use LiteSpeed Cache to accelerate them. If a vendor’s publicly-facing WordPress site uses a vulnerable version, an attacker could target user sessions, access admin panels, and pivot into broader site compromise. That compromise could mean unauthorized content or plugin installation, data exfiltration from the site’s database, or using the site as a distribution point for phishing/malware. For organizations whose vendors operate customer-facing WordPress sites, the vendor’s web layer becomes an attack surface impacting integrity, availability and the vendor’s brand trust.
WHAT QUESTIONS SHOULD TPRM PROFESSIONALS ASK VENDORS ABOUT THIS VULNERABILITY?
Here are four targeted questions to send to vendors using LiteSpeed Cache:
- Which version of LiteSpeed Cache plugin is installed on your WordPress instances (public-facing and internal)?
- Are any of the WordPress sites you operate publicly reachable and still running version 7.5.0.1 or earlier of LiteSpeed Cache? If yes, what is the mitigation/upgrade plan?
- Do you have a Content Security Policy (CSP) in place on your WordPress sites that restricts script execution sources and reduces XSS risk?
- Do you monitor or log for unusual account creations, plugin installations, or session-cookie theft events following link-click activity? Can you provide recent logs or alert summaries?
REMEDIATION RECOMMENDATIONS FOR VENDORS
Provide these actionable steps for vendors subject to the risk:
- Immediately upgrade the LiteSpeed Cache plugin to version 7.6 or newer.
- Review all WordPress sites (public-facing and vendor-internal) and confirm no instances remain on versions ≤ 7.5.0.1.
- Implement a strict Content Security Policy (CSP) restricting allowed script sources (for example, only trusted domains) to mitigate reflected XSS impact.
- Educate site administrators and users about the risks of clicking untrusted links, especially those that appear to come from internal systems or look-alike domains.
- Monitor site logs for abnormal behavior: new admin accounts, plugin installs outside change windows, unusual script execution, or session cookie anomalies.
HOW TPRM PROFESSIONALS CAN LEVERAGE BLACK KITE FOR THIS VULNERABILITY
The Black Kite “LiteSpeed – Oct2025” FocusTag was published with Confidence Level: HIGH and an expiration date of 31 January 2026. TPRM professionals can use the tag to:
- Identify which of their vendors host WordPress sites and whether those sites use the vulnerable plugin version.
- Leverage asset-level intelligence (public IPs, domain/subdomain lists, version banner information) to detect externally-reachable sites using the plugin version ≤ 7.5.0.1.
- Automate vendor outreach by generating a vendor questionnaire based on the above questions, tracking remediation status, and assigning SLAs (for example, high priority for internet-facing sites).
- Use the tag’s expiration and update timeline to schedule re-scanning of vendor environments, and maintain a closed-loop process where evidence of upgrade or mitigation is required before vendor status is considered “remediated”.
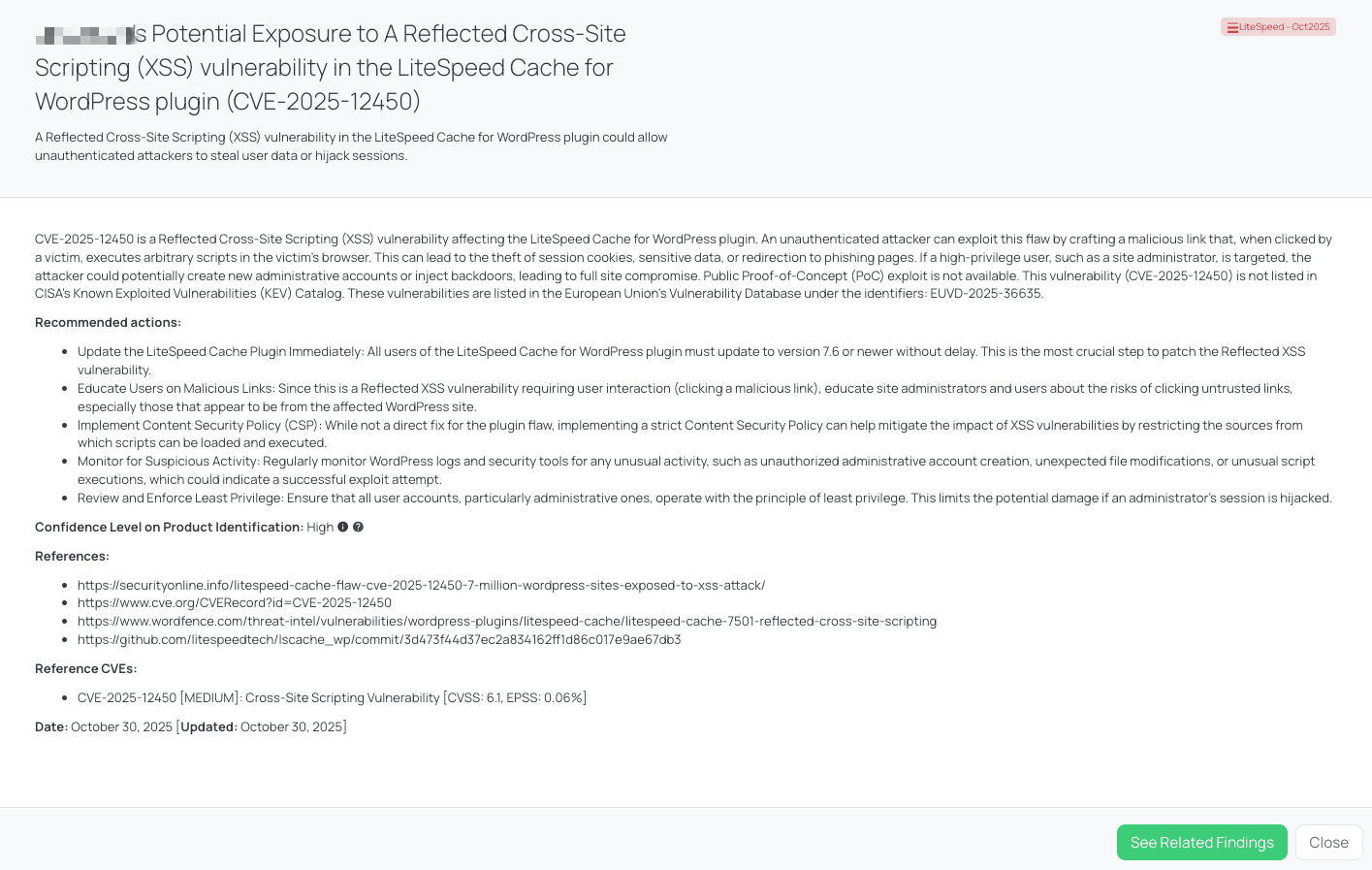
Black Kite’s LiteSpeed – Oct2025 FocusTag™ details critical insights on the event for TPRM professionals.
ENHANCING THIRD-PARTY RISK MANAGEMENT WITH BLACK KITE’S FOCUSTAGS™
In an environment where vulnerabilities emerge daily across multiple layers of the technology stack, Black Kite’s FocusTags™ enable security and risk teams to act decisively. This week’s vulnerabilities — spanning from network infrastructure (MikroTik RouterOS) to middleware (Apache Tomcat), security tooling (HashiCorp Vault), and CMS plugins (LiteSpeed Cache) — illustrate the breadth of third-party exposure organizations face.
FocusTags™ streamline this complexity through:
- Real-Time Risk Identification: Instantly revealing which vendors use affected technologies, enabling teams to act quickly and prioritize their outreach.
- Targeted Risk Prioritization: Allowing organizations to rank vendors based on both the criticality of the vulnerability and the vendor’s role in their ecosystem.
- Actionable Vendor Engagement: Empowering TPRM professionals to engage vendors with precise, context-specific questions supported by observed asset data.
- Comprehensive Exposure Visibility: Offering an aggregated view of vulnerabilities across vendor assets, including IPs, subdomains, and product banners, transforming fragmented intelligence into unified risk insights.
By leveraging these capabilities, Black Kite’s FocusTags™ help transform vulnerability awareness into tangible action, reducing the time between exposure detection and mitigation. They equip organizations to focus not on every vulnerability — but on the ones that truly matter across their vendor ecosystem.
ABOUT FOCUS FRIDAY
Every week, we delve into the realms of critical vulnerabilities and their implications from a Third-Party Risk Management (TPRM) perspective. This series is dedicated to shedding light on pressing cybersecurity threats, offering in-depth analyses, and providing actionable insights.
FOCUSTAGS™ IN THE LAST 30 DAYS:
- MikroTik RouterOS & SwOS : CVE-2025-61481, Arbitrary Code Execution Vulnerability, Man-in-the-Middle (MITM) Attack Vulnerability in MikroTik RouterOS & SwOS.
- Apache Tomcat – Oct2025 : CVE-2025-55752, CVE-2025-55754, CVE-2025-61795, Remote Code Execution, Authorization Bypass, Path Traversal, File Upload, Improper Neutralization of Escape, Meta, or Control Sequences, Improper Resource Shutdown or Release, Improper Input Validation, Authentication Bypass, Denial of Service Vulnerabilities in Apache Tomcat.
- Vault – Oct2025 : CVE-2025-12044, CVE-2025-11621, Denial of Service, Allocation of Resources Without Limits or Throttling, Authentication Bypass, Improper Authentication Vulnerabilities in Vault.
- LiteSpeed – Oct2025 : CVE-2025-12450, Cross-site Scripting (XSS) Vulnerability in LiteSpeed.
- Samba Server : CVE-2025-10230, Remote Code Execution Vulnerability in Samba servers.
- Atlassian Jira – Oct2025 : CVE-2025-22167, CVE-2025-58057, CVE-2025-58056, CVE-2025-7962, CVE-2025-48989, Path Traversal, Arbitrary File Write, Remote Code Execution (RCE), Denial of Service (DoS), Request Smuggling, SMTP Injection, Improper Resource Shutdown or Release (MadeYouReset DDoS) vulnerabilities in Atlassian Jira Software and Jira Service Management.
- TP-Link Omada Gateways : CVE-2025-6541, CVE-2025-6542, CVE-2025-7850, CVE-2025-7851, OS Command Injection vulnerabilities and Unauthorized Root Access via Debug Functionality in TP-Link Omada Gateways.
- MinIO – Oct2025 : CVE-2025-62506, Privilege Escalation Vulnerability in MinIO servers.
- Squid Proxy – Oct2025 : CVE-2025-62168, Information Disclosure Vulnerability in Squid Proxy.
- Sauter EY-modulo : CVE-2025-41723, CVE-2025-41724, CVE-2025-41722, CVE-2025-41721, CVE-2025-41720, CVE-2025-41719, Improper Validation of Syntactic Correctness of Input Vulnerability, Denial of Service Vulnerability, Use of Hard-coded Credentials Vulnerability, Reliance on File Name or Extension of Externally-Supplied File Vulnerability, Command Injection Vulnerability in Sauter EY-modulo.
- Oracle EBS: CVE-2025-61882, Remote Code Execution Vulnerability, Missing Authentication for Critical Function Vulnerability in Oracle E-Business Suite.
- Jenkins – Oct2025: CVE-2017-1000353, Remote Code Execution Vulnerability in Jenkins.
- Redis – Oct2025: CVE-2025-49844, CVE-2025-46817, CVE-2025-46818, CVE-2025-46819, Remote Code Execution Vulnerability in Redis.
- DrayTek Vigor – Oct2025: CVE-2025-49844, CVE-2025-46817, CVE-2025-46818, CVE-2025-46819, Remote Code Execution Vulnerability in DrayTek Vigor Routers.
- Zimbra – Oct2025: CVE-2025-27915, Cross-Site Scripting (XSS) Vulnerability in Zimbra Collaboration Suite.
- Elastic – Oct2025: CVE-2025-25009, CVE-2025-25017, CVE-2025-25018, CVE-2025-37727, CVE-2025-37728, Cross-Site Scripting (XSS) Vulnerability, Unrestricted File Upload Vulnerability, Information Disclosure Vulnerability, Insufficiently Protected Credentials Vulnerability in Elastic & Kibana.
- Django – Oct2025: CVE-2025-59681, CVE-2025-59682, SQL Injection Vulnerability, Directory Traversal Vulnerability in Django.
- Grafana – Oct2025: CVE-2021-43798, Directory Traversal Vulnerability in Grafana.
- SillyTavern: CVE-2025-59159, DNS Rebinding Vulnerability, Remote Code Execution Vulnerability, Code Injection Vulnerability, Exposure of Sensitive Information Vulnerability in SillyTavern.
- WP Yoast SEO – Oct2025: CVE-2025-11241, Cross-Site Scripting (XSS) Vulnerability in WP Yoast SEO.
- Cisco ASA – Sep2025: CVE-2025-20333, CVE-2025-20362, Buffer Overflow Vulnerability, Missing Authorization in Cisco ASA and Cisco FTD.
- Cisco ASA & FTD & IOS – Sep2025: Buffer Overflow Vulnerability, Remote Code Execution Vulnerability in Cisco ASA, Cisco IOS, and Cisco FTD.
- VMware vCenter – Sep2025: CVE-2025-41250, SMTP Header Injection Vulnerability, Username Enumeration Vulnerability, Weak Password Recovery Mechanism Vulnerability in VMware vCenter.
- WD My Cloud: CVE-2025-30247, Command Injection Vulnerability in multiple Western Digital My Cloud network-attached storage (NAS) devices.
See Black Kite’s full CVE Database and the critical TPRM vulnerabilities that have an applied FocusTagTM at https://blackkite.com/cve-database/.
REFERENCES
https://nvd.nist.gov/vuln/detail/CVE-2025-61481
https://help.mikrotik.com/docs/spaces/ROS/pages/328131/WebFig
https://help.mikrotik.com/docs/spaces/SWOS/pages/328415/SwOS
https://svarthatt.se/cve/mikrotik-swos-cve-2025-61481
https://nvd.nist.gov/vuln/detail/CVE-2025-55752
https://nvd.nist.gov/vuln/detail/CVE-2025-55754
https://nvd.nist.gov/vuln/detail/CVE-2025-61795
https://github.com/TAM-K592/CVE-2025-55752
https://nvd.nist.gov/vuln/detail/CVE-2025-12044
https://nvd.nist.gov/vuln/detail/CVE-2025-11621
https://zeropath.com/blog/cve-2025-11621-vault-aws-auth-bypass
https://www.cve.org/CVERecord?id=CVE-2025-12450
https://github.com/litespeedtech/lscache_wp/commit/3d473f44d37ec2a834162ff1d86c017e9ae67db3