A Guide to fix your Cyber Rating? Here’s the Black Kite Strategy Report
Published
Jun 24, 2020
Updated
Jan 27, 2026
Authors
Black Kite
We all know effective risk management starts with an effective risk model. An effective model helps clearly express risks and enables you to take action. Risk management professionals frequently find themselves struggling with risk parameters, risk prioritization and mitigation issues. With classification-based risk scores, and financial risk models, is it clear to risk professionals where to start? Where to streamline their efforts?
As the only strategy report in cyberspace providing guidance from a technical, financial, and compliance perspective, here’s the Black Kite Strategy Report and how it reduces these efforts into one single report of actionable steps.
The Challenges in Risk Management
The Right Language: You can’t manage what you can’t talk about
Starting from the very basics, risk is defined as ”the probable frequency and probable magnitude of future loss” associated with a specific event, according to the Open FAIR™ institute. To accurately define a risk, one needs to consider a threat scenario, the affected asset(s), their value to the organization and the possible consequences.
It’s common for security professionals to misuse the words “risk” and “cyber risk” when referring to an event or a threat. Oftentimes, the assets’ value with regards to the company itself, regulations, and sometimes even the assets themselves are ignored in those conversations.
If one of these elements is missing, we can’t properly talk about risk. And if we cannot speak the right language, we cannot manage it.
“What is My Risk Management Model?”
Knowing and understanding the cyber ecosystem and the risk it presents to the company is a critical process in risk management. Given the ever widening regulatory landscape and trend of outsourcing critical functions, the workload for third-party risk management (TPRM) teams continues to pile up to complete the requisite due diligence, including assessment and monitoring.
This notion brings us to the questions:
- What model am I using right now?
- Is it an efficient model for TPRM?
- is it classification-based without any underlying advanced analysis?
- What should be the risk management model?
- How do I rank third parties according to their level of risk so cybersecurity consequences are connected to business goals?
Where to Start
Of all the challenges listed above, the initial steps that should be taken to alleviate the aggregated risk are perhaps the most critical ones in the realization of a TPRM strategy. Whether the risks are managed by an automated tool or manually with regards to a maturity model such as NIST, ISO27001, etc. risk professionals always find it difficult to take action even with a prioritized list of risks.
It’s not always straightforward whether the remediation of the actionable item will create the desired outcome. Lacking a true risk-based approach, and the true (economic) impact of engaging a third party lies in the heart of the problem.
With a clear, objective, and measurable list of items, like the Black Kite Strategy Report, it is easier for risk management professionals to take action.
Black Kite’s Strategy Report
Black Kite’s Strategy Report provides simple steps to mitigate risk. It is the only report in cyberspace providing guidance from a technical, financial, and compliance perspective.
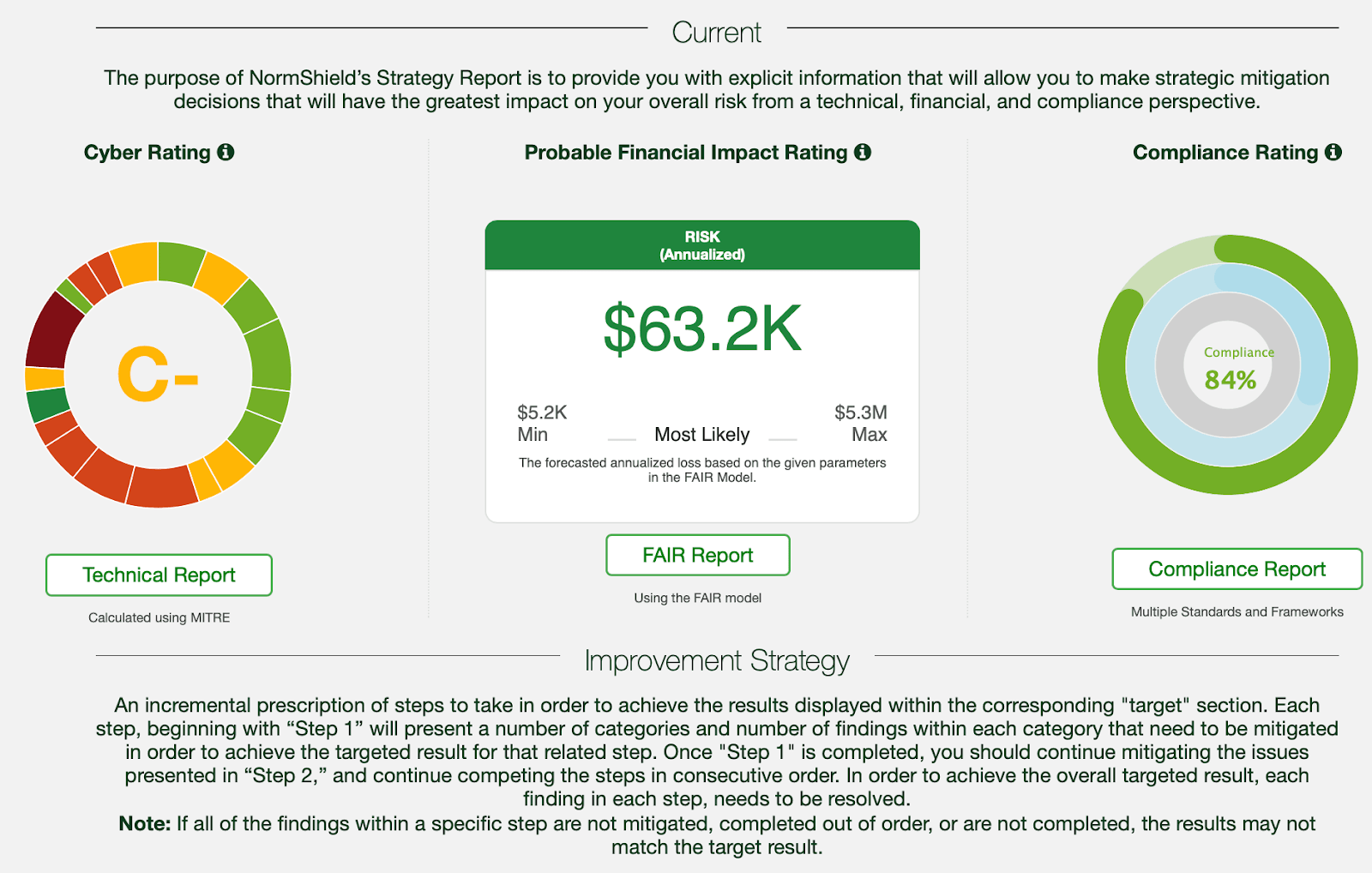
Platform users do not have to guess which steps to take to achieve the desired level of risk for both the organization and third parties. With Black Kite’s Automated Continuous Monitoring, it’s aggregated.
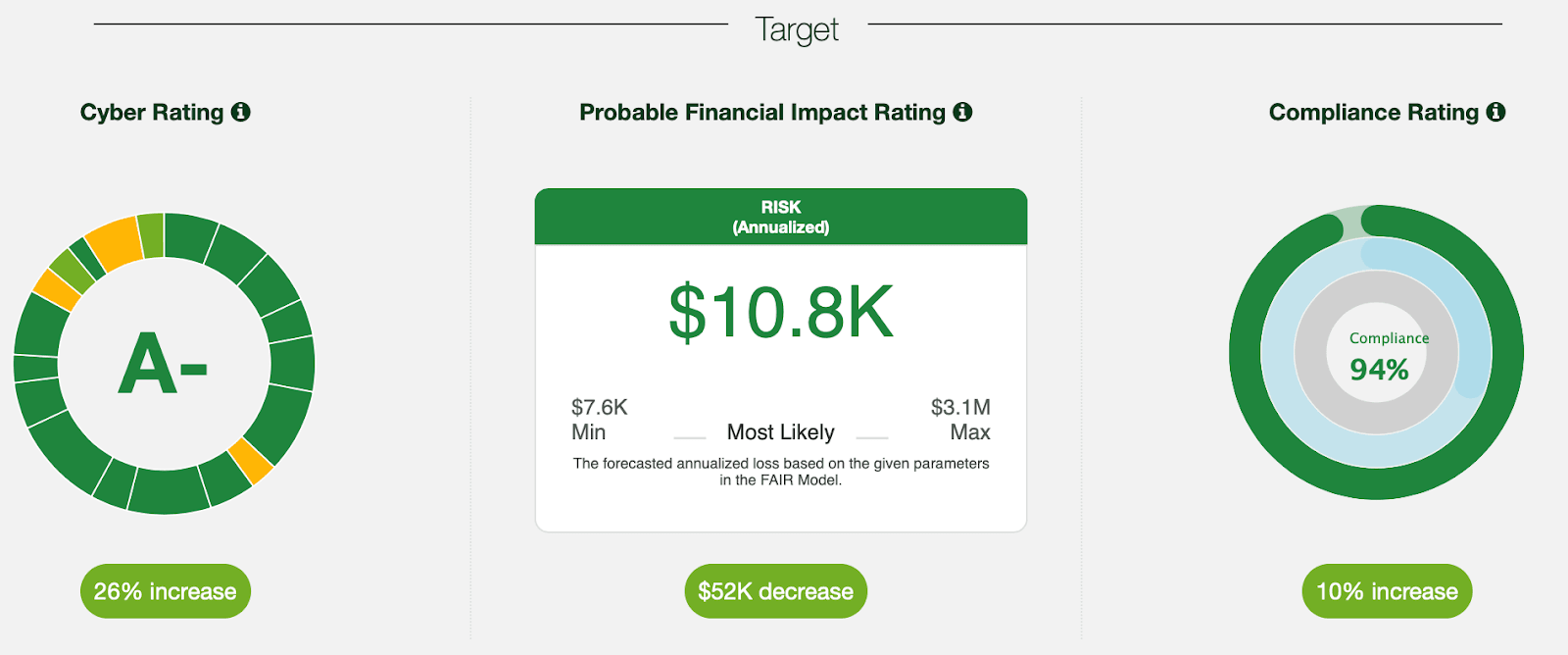
The Strategy Report consists of:
- Simple steps to mitigate risk
- Tasks prioritized based on criticality
- Strategy based on the target results you need
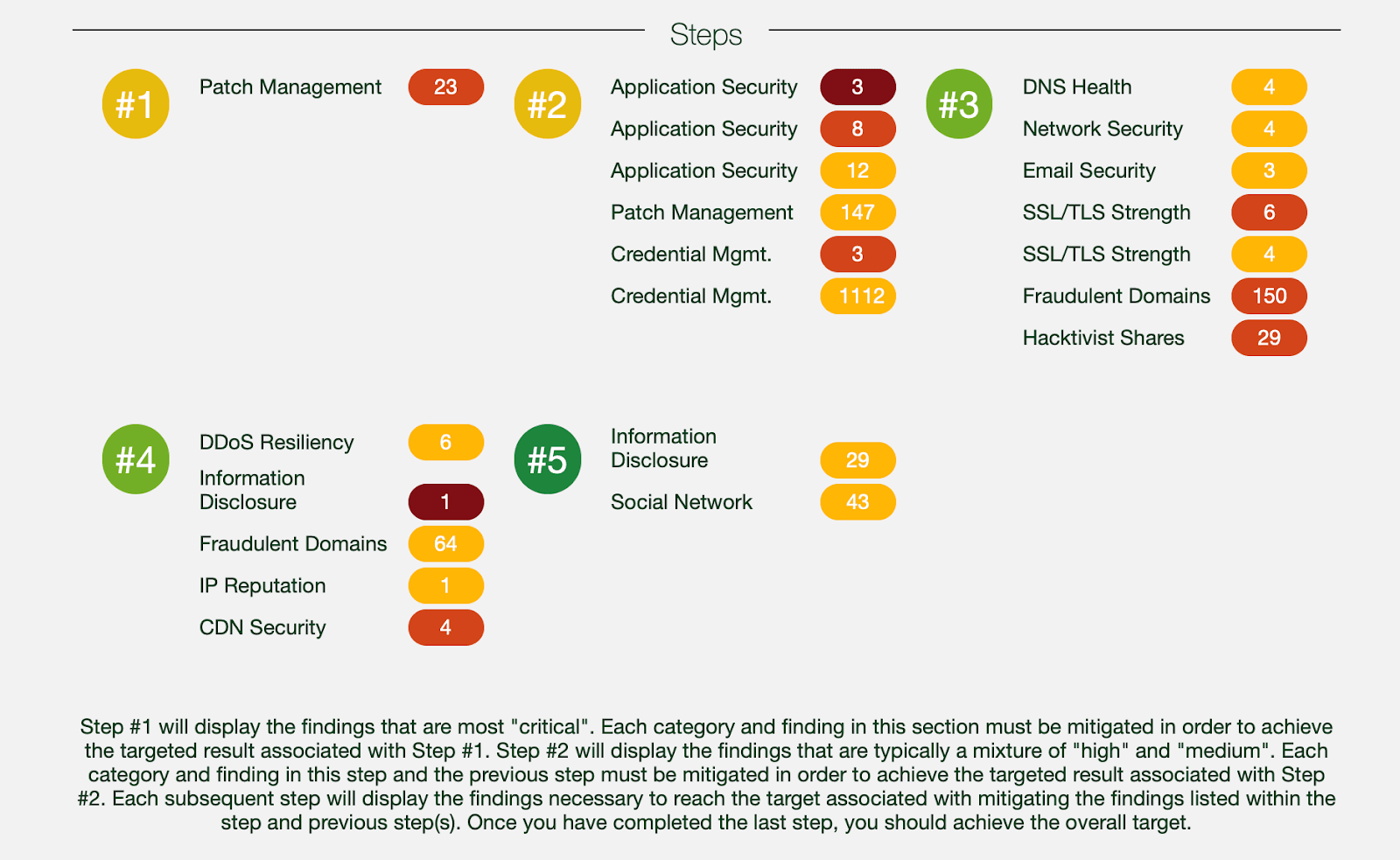
The report can be shared with a vendor in a .pdf report format or an excel file as a list of actionable items.
Integration with Ticketing System
The Strategy Report is also linked to the Black Kite Ticketing system, where you can assign suggested steps to a relevant contact in the organization and track whether remediation is solved.
The combination of these features will make any TPRM program a powerhouse.
To watch the video, click here.