When the Shai-Hulud Worm Awakens: Tinycolor’s Fall and the New Era of Supply Chain Risk
THE DAY OPEN SOURCE BECAME A WEAPON
In September 2025, the popular npm package @ctrl/tinycolor became the epicenter of a self-propagating supply chain attack, now known as the Shai-Hulud campaign. What started as a single compromised package quickly spread across the npm ecosystem, affecting dozens — if not hundreds — of dependent libraries. The impact reached the enterprise level, with CrowdStrike confirming that some of its packages were compromised, demonstrating that even security leaders are not immune to the ripple effects of open-source vulnerabilities.
This incident illustrates a painful truth for organizations: the open-source ecosystem, often treated as a passive tool, can become a weapon in the hands of attackers who exploit developer accounts, automation scripts, and CI/CD pipelines.
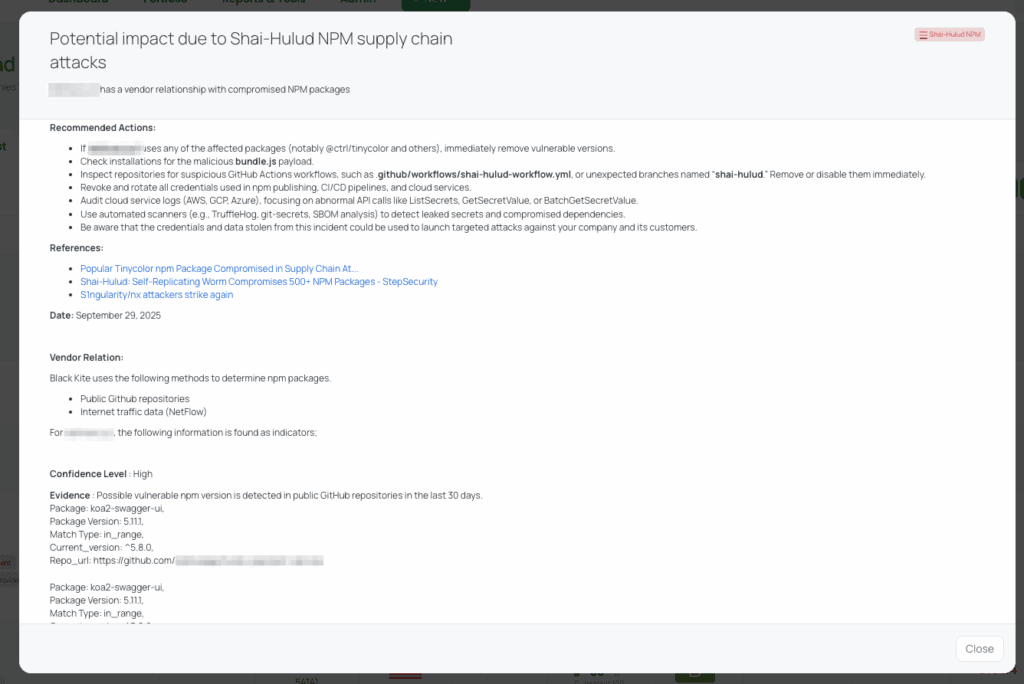
Black Kite’s Shai-Hulud NPM FocusTag™ details critical insights on the event for TPRM professionals.
ANATOMY OF THE WORM
The Shai-Hulud campaign is a stark reminder that supply chain worms can lie dormant, tunneling silently beneath the surface of organizations for years. All it takes is a single misstep—a compromised developer account, a poisoned package—for the worm to awaken and bring the entire structure to the brink of collapse.
The attack relied on a malicious postinstall script embedded in @ctrl/tinycolor. Here’s how it worked:
- Upon installation, the script executed a minified payload (bundle.js) that scanned the host environment, searching for sensitive files, environment variables, and CI/CD configuration files.
- The payload looked specifically for cloud credentials (AWS, GCP, Azure), GitHub and npm tokens, and other authentication secrets used in continuous integration workflows.
- Once harvested, the credentials were sent to attacker-controlled endpoints, allowing lateral movement and exfiltration from connected systems.
- The worm then republished compromised versions of other npm packages, effectively propagating itself automatically through the ecosystem.
- Initial reports from Socket.dev indicated ~40 affected packages, but StepSecurity and Aikido later confirmed that the worm had infected hundreds of packages, including those used by enterprise organizations.
- Indicators of compromise (IoCs) include:
- Malicious bundle SHA-256: 46faab8ab153fae6e80e7cca38eab363075bb524edd79e42269217a083628f09
- Rogue GitHub workflow: .github/workflows/shai-hulud-workflow.yml
- Unusual publish activity and external HTTP requests to endpoints like webhook.site.
- Malicious bundle SHA-256: 46faab8ab153fae6e80e7cca38eab363075bb524edd79e42269217a083628f09
This combination of credential harvesting, automated propagation, and repository compromise makes Shai-Hulud one of the most sophisticated npm supply chain attacks observed to date.
THE ADVERSARY'S PLAYBOOK: WHO WOULD LAUNCH A DIGITAL WORM?
While the exact identity of the attackers remains unknown, their methodology suggests a criminally motivated, automation-driven campaign:
- Objective: Harvest high-value secrets at scale from developer machines, CI/CD pipelines, and cloud environments.
- Method: Exploit developer trust in npm packages, propagate malicious payloads automatically, and leverage stolen tokens to compromise additional packages.
- Impact: Access to sensitive enterprise resources, potential lateral movement, and the ability to manipulate other packages in the supply chain.
Unlike precision attacks from nation-state actors, Shai-Hulud prioritized speed and scale, turning the open-source ecosystem into a viral propagation network.
THE SILENT THREAT IN OPEN SOURCE
This campaign underscores a harsh reality for TPRM (Third-Party Risk Management) teams: dependencies are vendors, whether you have contracts with them or not.
- Transitive risk matters: A single compromised indirect dependency can introduce serious vulnerabilities into enterprise systems.
- Developer accounts and CI/CD pipelines are attack surfaces: GitHub tokens, npm tokens, and automation credentials now act as gateways to sensitive resources.
- Rapid propagation outpaces traditional alerts: Vendor notifications often arrive too late; proactive monitoring is essential.
- Open-source threat intelligence is critical: Indicators of compromise, malicious hashes, rogue workflow files, and unusual package publish activity must be ingested into SIEM/SOAR pipelines to detect early signs of compromise.
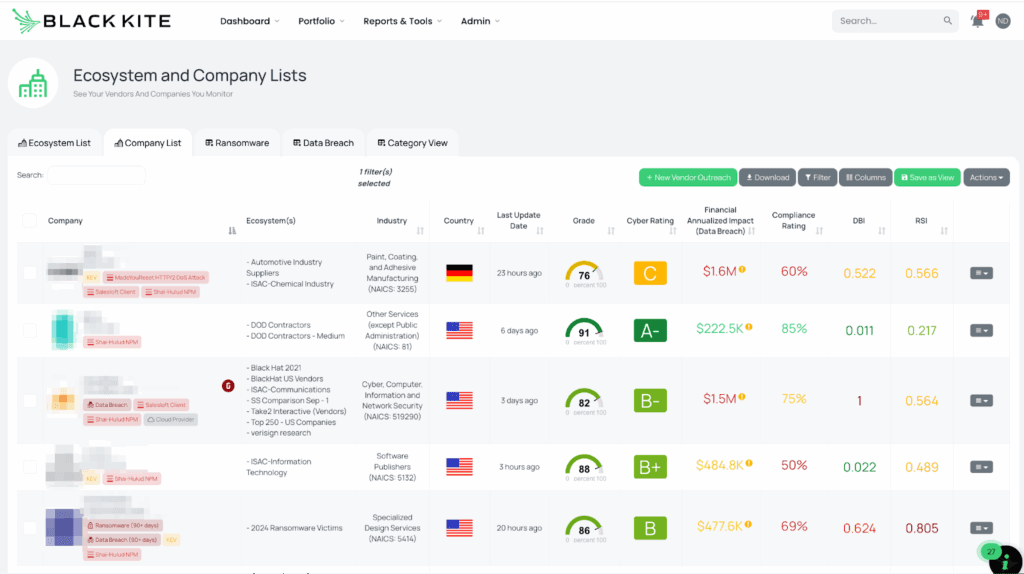
Filtered view of companies with the Shai-Hulud NPM FocusTag™ on the Black Kite platform.
LESSONS ETCHED IN CODE: IMMEDIATE TPRM ACTIONS
For organizations looking to strengthen their TPRM posture, the Shai-Hulud campaign provides a clear checklist:
- Audit dependencies: Review SBOMs and dependency graphs to identify direct and transitive usage of @ctrl/tinycolor or other impacted packages.
- Revoke and rotate credentials: Immediately rotate npm tokens, GitHub tokens, and cloud keys that may have been exposed.
- Scan CI/CD and repositories: Look for rogue workflow files like .github/workflows/shai-hulud-workflow.yml and unusual external calls from build scripts.
- Lock package versions: Pin to verified, clean versions and rebuild artifacts from source to ensure integrity.
- Enforce least privilege: Limit token scopes and enforce ephemeral credentials in CI/CD pipelines.
- Educate developers: Secrets should never be stored in plain text, tickets, or code comments. Awareness is a key defense.
- Integrate OSS threat intelligence: Incorporate IoCs and alerts from open-source monitoring platforms into TPRM dashboards.
For TPRM and third-party risk intelligence teams, the message is clear: treat dependencies like vendors, monitor them continuously, and prepare for fast-moving supply chain threats. The cost of ignoring this reality is measured not in lost time, but in compromised secrets and potential enterprise exposure.
TURNING OPEN-SOURCE CHAOS INTO CLEAR RISK VISIBILITY WITH BLACK KITE
The Shai-Hulud campaign demonstrated how the compromise of a single npm package (@ctrl/tinycolor) could rapidly spread to hundreds of dependencies and enterprise systems. Such supply chain attacks make it clear that not only direct business partners but also open-source dependencies must now be addressed within the scope of TPRM.
Black Kite provides organizations with the ability to make their dependency ecosystem visible and continuously monitored. It not only maps the direct usage of a package but also its transitive dependencies and ecosystem connections, flagging risky components. For example, in the Shai-Hulud case, affected packages could have been automatically prioritized with FocusTag™-like labels. Black Kite also enabled organizations to clearly see their own exposure by identifying repositories containing the affected packages—whether updated or still vulnerable—and the applications tied to them.
This way, companies no longer have to rely solely on delayed vendor notifications; instead, they can proactively detect risks, quickly rotate credentials, and limit access to build an effective defense.