Focus Friday: TPRM Insights on Jetty, Jenkins, and CUPS Vulnerabilities
INTRODUCTION
Welcome to this week’s Focus Friday. We’re looking at three timely issues through a third-party risk lens: Jetty’s HTTP/2 MadeYouReset DoS, Jenkins core information-disclosure and log-injection flaws, and CUPS authentication bypass and DoS. Each can disrupt key supplier services—web apps and APIs (Jetty), CI/CD pipelines (Jenkins), and print services across Linux/Unix estates (CUPS). Below, you’ll find dedicated sections for each FocusTag with the essentials: what the flaws are, why they matter to TPRM, targeted questions for vendors, and concrete remediation steps.
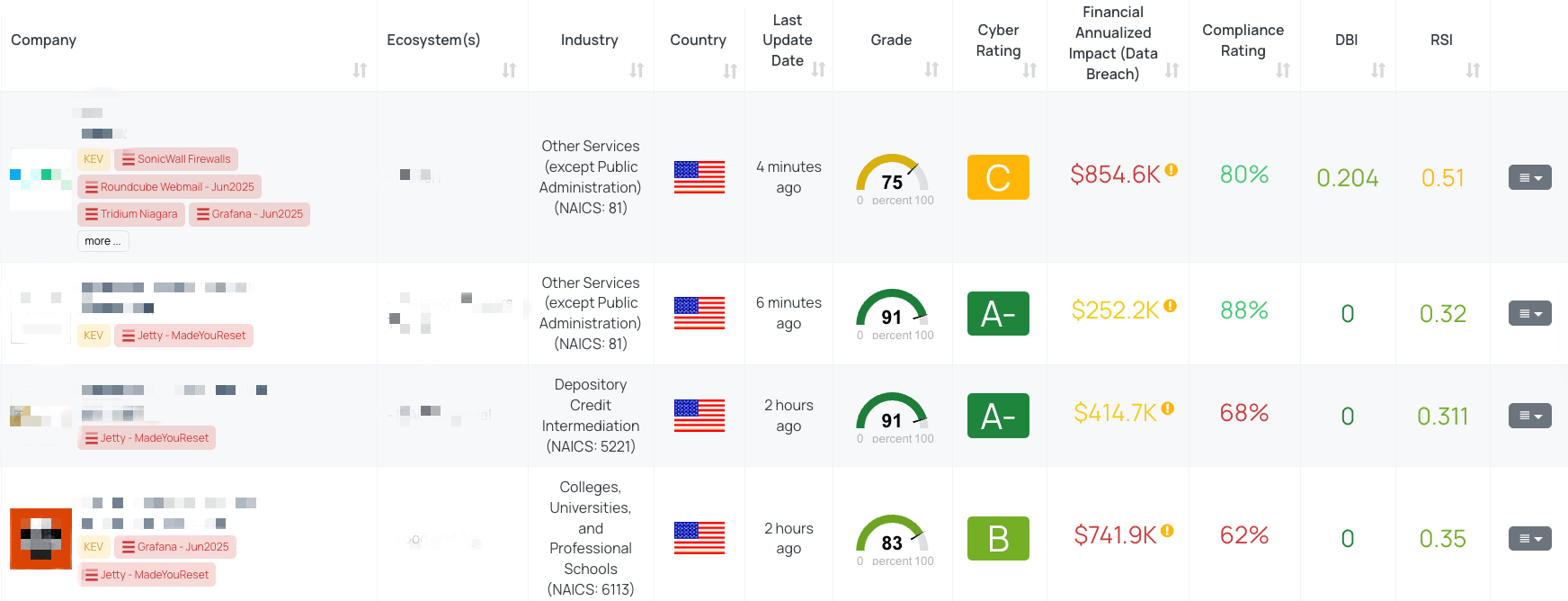
Filtered view of companies with Jetty – MadeYouReset FocusTag™ on the Black Kite platform.
CVE-2025-5115 – ECLIPSE JETTY HTTP/2 "MADEYOURESET" (DOS)
What is the MadeYouReset vulnerability in Eclipse Jetty?
A high-severity denial-of-service flaw in Jetty’s HTTP/2 handling lets a client trigger server-side RST_STREAM frames using malformed control/flow sequences (for example, invalid WINDOW_UPDATE, HEADERS/DATA on half-closed streams, or malformed PRIORITY). Because reset streams aren’t counted toward the concurrent-stream limit, an attacker can rapidly spin up work the backend still processes, exhausting CPU and memory. Current scores: CVSS 7.7 and EPSS 0.07%. Public disclosure was in 2025-08-20. As of 2025-09-18, there is no CISA KEV listing and no public confirmation of in-the-wild exploitation tied to this CVE. Patched versions are available, and products embedding Jetty (such as CI/CD frontends) have issued fixes or guidance.
Why should TPRM professionals care?
Jetty underpins many Java web apps, reverse proxies, and embedded servers. When exposed over HTTP/2, this flaw can knock out public portals, APIs, CI/CD frontends, and partner integrations—leading to outages, failed transactions, and SLA breaches at vendors your organization depends on. Even if HTTP/2 is disabled by default, administrators sometimes enable it for performance; misconfigurations can turn a transient stress test into prolonged downtime.
What questions should TPRM professionals ask vendors?
- Have you updated your Eclipse Jetty instance to a patched version such as 9.4.58, 10.0.26, 11.0.26, 12.0.25, or 12.1.0.beta3 to mitigate the risk of the MadeYouReset DoS vulnerability (CVE-2025-5115)?
- Have you implemented monitoring to detect and alert on high-volume activity related to HTTP/2, specifically looking for an unusual number of `RST_STREAM` frames being sent from the server to clients, which could indicate a MadeYouReset attack is in progress?
- Have you taken steps to limit the rate at which clients can send HTTP/2 control frames like WINDOW_UPDATE and PRIORITY to prevent an attacker from rapidly triggering the MadeYouReset vulnerability and overwhelming the server’s resources?
- If an immediate update was not possible, have you disabled the HTTP/2 protocol on your Jetty server as a temporary workaround to eliminate the attack vector of the MadeYouReset vulnerability?
Remediation recommendations for vendors
- Patch/upgrade immediately to fixed Jetty packages: http2-common 9.4.58 / 10.0.26 / 11.0.26, jetty-http2-common 12.0.25 / 12.1.0.beta3 (or newer). Validate transitive dependencies in build files (Maven/Gradle).
- If patching is delayed, disable HTTP/2 on affected Jetty services as a temporary mitigation.
- Harden protocol handling: cap rates for HTTP/2 control frames and treat repeated flow violations as connection errors to drop abusive clients.
- Instrument detection: add telemetry for server-initiated RST_STREAM bursts and correlate with host resource metrics to flag attack conditions early.
How TPRM teams can leverage Black Kite for this vulnerability
Black Kite’s FocusTag “Jetty ‒ MadeYouReset” gives organizations a way to zero in on which vendors are potentially running vulnerable Eclipse Jetty HTTP/2 components (i.e., versions/builds pre-patch for CVE-2025-5115). Here’s how to operationalize it:
- Use Black Kite’s vendor intelligence/scan data to identify assets (IP addresses, hostnames, subdomains) that correspond to Jetty deployments exposing HTTP/2 and matching vulnerable package ranges.
- For each vendor identified with vulnerable Jetty HTTP/2 assets, initiate follow-ups using the targeted questions above.
- Prioritize patching or temporary mitigations (e.g., disabling HTTP/2) for vendors with externally reachable web apps/APIs or critical partner integrations relying on Jetty.
- Include this FocusTag in your vendor risk framework: treat vendors flagged by this tag as requiring more frequent reviews and time-boxed remediation checkpoints.
- Monitor for updates to the tag—e.g., newly observed exploit activity, added detections, or inclusion in CISA’s KEV catalog—which would elevate urgency and outreach cadence.
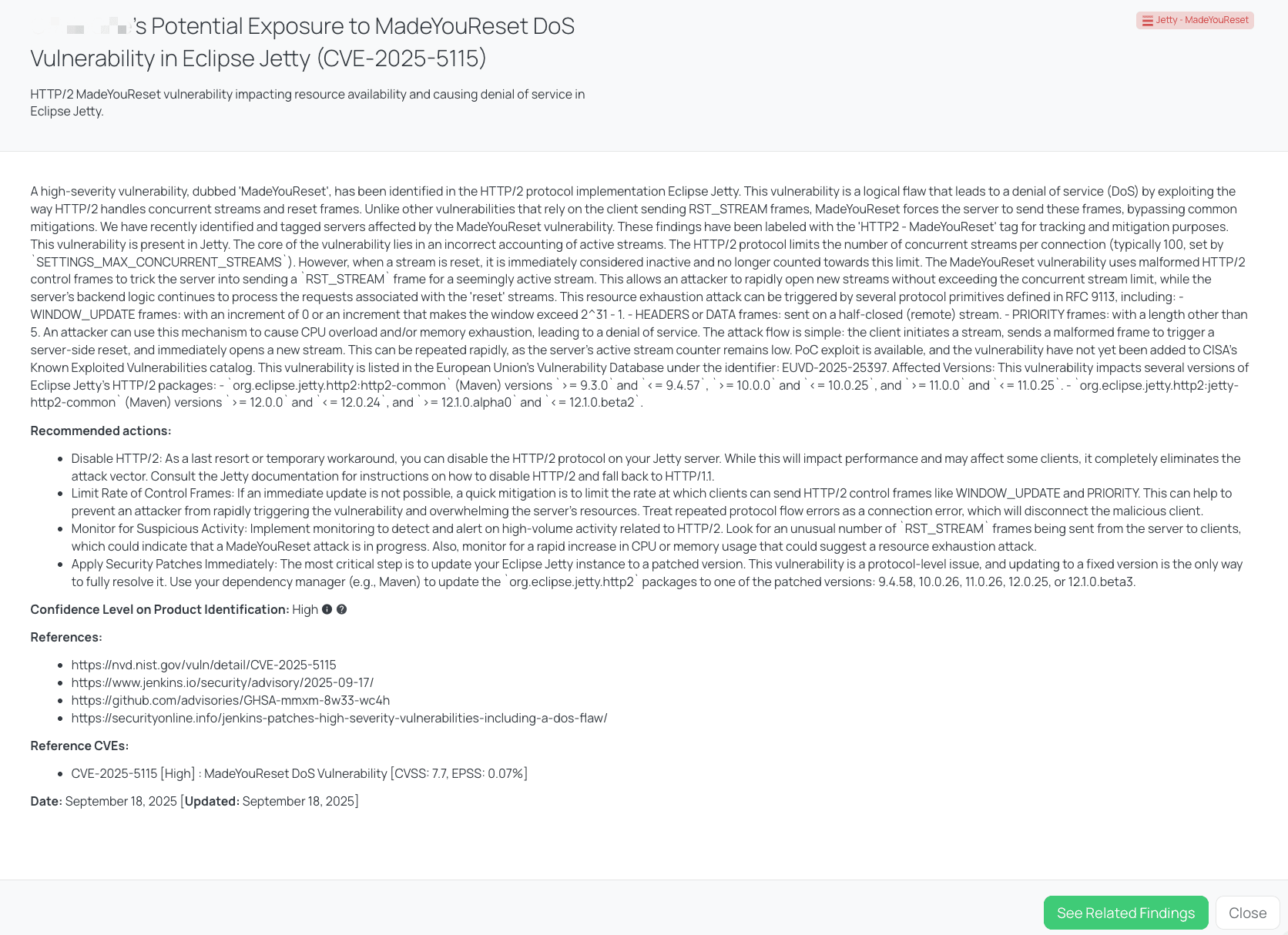
Black Kite’s Jetty – MadeYouReset FocusTagTM details critical insights on the event for TPRM professionals.
CVE-2025-59474/CVE-2025-59475/CVE-2025-59476 – JENKINS
What are the September 2025 Jenkins vulnerabilities?
Three medium-severity issues were disclosed for Jenkins core on 2025-09-17:
- CVE-2025-59474 (Information disclosure) – missing permission check in a sidepanel view lets unauthenticated users enumerate agent (node) names via the executors widget. CVSS 5.3, EPSS 0.02%. Affects Jenkins ≤ 2.527and LTS ≤ 2.516.2; fixed in 2.528 / 2.516.3.
- CVE-2025-59475 (Information disclosure) – missing permission check in the authenticated user profile menu allows limited configuration disclosure (for example, whether Credentials Plugin is installed) without Overall/Read. CVSS 4.3, EPSS 0.02%. Same affected/fixed versions.
- CVE-2025-59476 (Log message injection) – crafted content can inject new lines into logs (for example, jenkins.log) and forge entries; mitigated by adding visible markers ([CR], [LF], [CRLF] >). CVSS 5.3, EPSS 0.02%. Same affected/fixed versions.
As of 2025-09-18, there’s no evidence of in-the-wild exploitation and no CISA KEV listing for these CVEs.
Why should TPRM professionals care?
Jenkins often fronts CI/CD portals and APIs your vendors rely on for builds, releases, and integrations.
- Agent name leakage (59474/59475) gives adversaries reconnaissance—identifying build nodes, naming conventions, or plugin footprints to tailor phishing, lateral movement, or plugin-targeting exploits.
- Log injection (59476) can mislead incident response and obscure audit trails, complicating vendor attestations and your due diligence if an event occurs.
If a vendor’s Jenkins is Internet-accessible or exposed to untrusted SSO tenants/VPNs, these issues elevate business risk (pipeline disruption, tampered evidence, noisy IR).
What questions should TPRM professionals ask vendors?
- Have you updated all instances of Jenkins to version 2.528 or LTS 2.516.3 to mitigate the risk of CVE-2025-59474, CVE-2025-59475, and CVE-2025-59476?
- Have you implemented network-level controls such as VPNs, IP whitelisting, or firewall rules to limit Jenkins exposure as recommended in the advisory?
- Are you actively monitoring and investigating unusual or unauthorized network traffic targeting Jenkins to detect potential exploitation of these vulnerabilities?
- Have you reviewed and adjusted Jenkins user permissions to align with the principle of least privilege, specifically in relation to the sidepanel executors widget where the permission bypass vulnerabilities were identified?
Remediation recommendations for vendors
- Patch immediately to 2.528 / 2.516.3 (or newer). This removes the vulnerable views/behaviors and adds log-injection indicators.
- Tighten access until patched: restrict exposure to trusted networks; ensure Overall/Read isn’t granted to anonymous or broad groups; review authorization strategy.
- Harden logging pipelines: ensure SIEM/collectors preserve special-character markers and alert on anomalous line breaks or sudden spikes in agent-enumeration requests.
- Validate plugin surface post-upgrade (especially Credentials-adjacent plugins) to avoid compounding risks noted in prior advisories.
How TPRM professionals can leverage Black Kite for this vulnerability
Black Kite’s FocusTag “Jenkins – Sep2025” gives organizations a way to zero in on vendors potentially running affected Jenkins core versions (≤ 2.527 / LTS ≤ 2.516.2). Here’s how to operationalize it:
- Use Black Kite’s vendor intelligence/scan data to identify assets (IP addresses, hostnames, subdomains) exposing Jenkins controllers consistent with the affected versions.
- For each vendor identified, initiate follow-ups using the targeted questions above and request a post-patch attestation (version, date/time, change ticket).
- Prioritize additional controls for vendors with Internet-reachable Jenkins or pipelines tied to sensitive workloads(for example, software releases to your environment).
- Embed this FocusTag in your vendor-risk playbook: vendors flagged by the tag should get accelerated review cycles and time-boxed remediation checkpoints.
- Monitor the tag for updates (for example, if public exploitation emerges or CISA KEV adds these CVEs, raise urgency). Black Kite published this tag on 2025-09-18, and the platform’s asset-level evidence helps narrow outreach.v
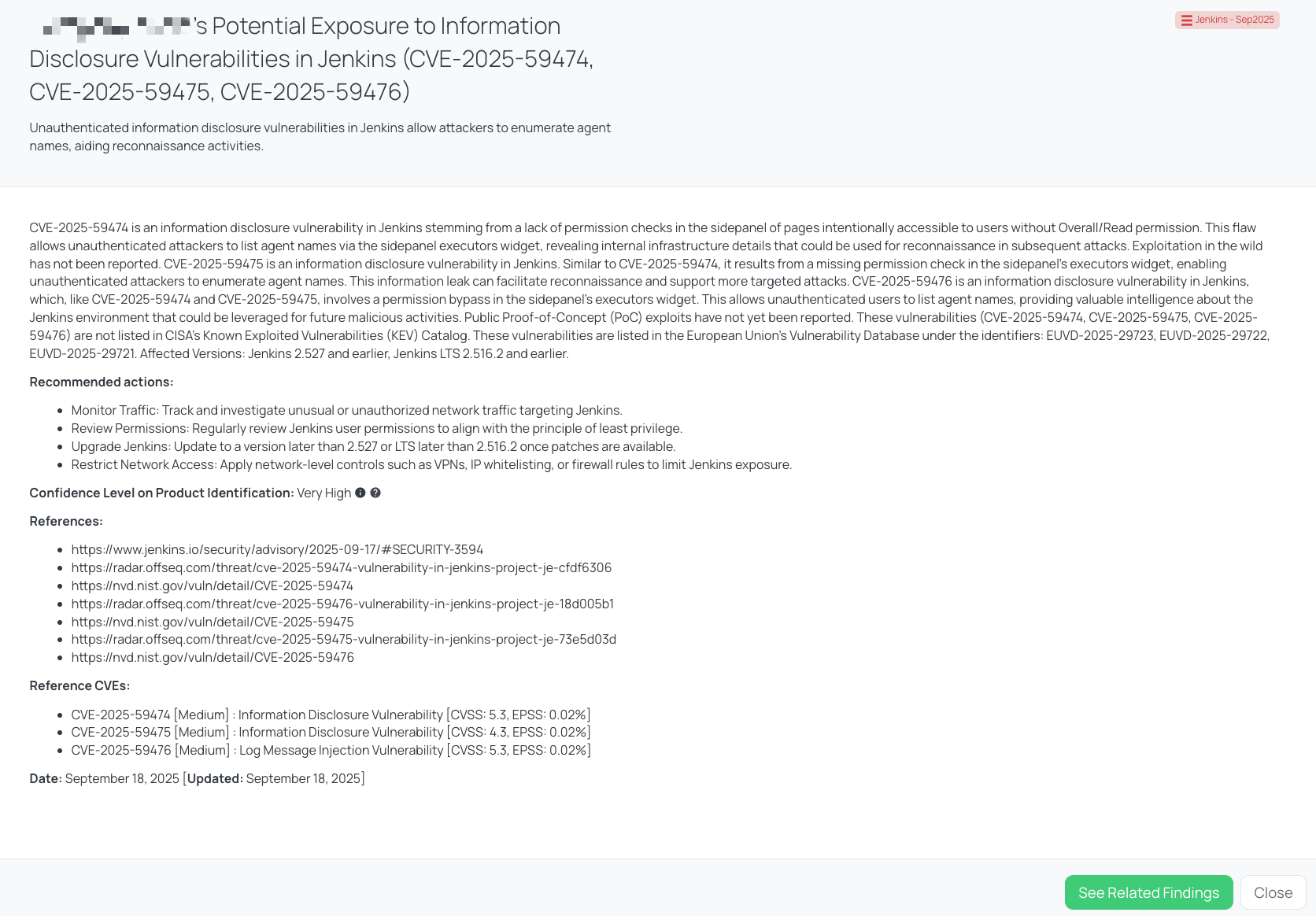
Black Kite’s Jenkins – Sep2025 FocusTagTM details critical insights on the event for TPRM professionals.
CVE-2025-58060 & CVE-2025-58364 — CUPS
CUPS (Common Unix Printing System) is the open-source service that lets Unix-like systems (including Linux and macOS) find printers, accept print jobs, and manage them over the network. It uses IPP on port 631, with a cupsdscheduler plus libcups, filters, and backends so apps can print to local or network devices. Modern setups support driverless printing (IPP Everywhere/AirPrint).
What are the new CUPS vulnerabilities?
Two issues disclosed on 2025-09-11 affect CUPS:
- CVE-2025-58060 – Authentication bypass (High). When AuthType is anything other than Basic, sending an Authorization: Basic … header skips password verification in cupsdAuthorize, allowing unauthenticated access to admin endpoints. CVSS: 8.0, EPSS: 0.02%. Affects CUPS < 2.4.13; fixed in 2.4.13.
- CVE-2025-58364 – Remote DoS via null dereference (Medium). Crafted IPP printer-attributes responses can trigger a NULL dereference through ipp_read_io() and ippValidateAttributes(), crashing cups/cups-browsedon local networks. CVSS: 6.5, EPSS: 0.03%. Affects CUPS < 2.4.12; fixed in 2.4.12.
Public PoC exists for the DoS (58364); the auth bypass (58060) is trivially reproducible with a crafted Authorization: Basic header when a non-Basic auth method is configured.
As of 2025-09-18, there’s no public evidence of in-the-wild exploitation and no CISA KEV listing for these CVEs. No CISA advisory has been issued at this time.
Why should TPRM professionals care?
CUPS underpins print and scanning workflows across Linux, BSD, Solaris, ChromeOS, and others.
- CVE-2025-58060 can enable unauthorized admin access where non-Basic authentication (e.g., Negotiate/Kerberos) is used, risking configuration tampering and privilege abuse.
- CVE-2025-58364 can disrupt printing services across a local network, affecting operations and helpdesk workloads; exposure may extend beyond the LAN if IPP is reachable from untrusted networks.
What questions should TPRM professionals ask vendors?
- Have you updated all instances of CUPS to version 2.4.13 or later to mitigate the risk of CVE-2025-58060 and CVE-2025-58364?
- Can you confirm if you have implemented network-level controls, specifically blocking all incoming traffic to CUPS on UDP port 631 from untrusted external networks, to prevent remote exploitation of CVE-2025-58364?
- Have you disabled the cups-browsed service, a common attack vector, to reduce the system’s attack surface and mitigate the risk of CVE-2025-58364?
- Are you regularly reviewing network logs for unusual activity, especially on ports used by CUPS (TCP/UDP 631), to detect any high volume of IPP requests or connection attempts from unknown sources, which could indicate an ongoing attack exploiting CVE-2025-58060 or CVE-2025-58364?
Remediation recommendations for vendors
- Patch promptly. Upgrade to CUPS 2.4.13+ (auth bypass) and 2.4.12+ (DoS). Verify the specific upstream fixes are present in your distro’s builds.
- Limit exposure. Block external access to IPP (631) except from trusted subnets/VPN; where feasible, restrict to server-side printing proxies.
- Harden auth. Prefer strong auth paths; ensure AuthType policies are enforced and that Basic is disabled where not explicitly required. Add request filters to drop unexpected Authorization: Basic headers when non-Basic is configured.
- Reduce attack surface. If not required, disable cups-browsed to curb unauthenticated discovery on local networks.
- Detect & respond. Instrument logs for repetitive IPP attribute responses and service crashes; alert on repeated daemon restarts and anomalous IPP request patterns.
How TPRM professionals can leverage Black Kite for this vulnerability
Black Kite’s FocusTag “CUPS – Sep2025” helps you identify vendors potentially running affected CUPS versions or exposing IPP endpoints. Here’s how to operationalize it:
- Use Black Kite’s vendor intelligence/scan data to pinpoint assets (IP addresses, hostnames, subdomains) tied to CUPS/IPP (port 631) and match them against vulnerable version ranges (<2.4.13 for 58060; <2.4.12 for 58364).
- For each vendor identified, kick off follow-ups using the questions above and request post-patch attestations(package version, build, and change ticket).
- Prioritize additional safeguards for vendors with externally reachable IPP or those supporting business-critical print workflows (e.g., logistics, healthcare orders).
- Add this FocusTag to your vendor risk playbook: treat flagged vendors as requiring accelerated review cycles and time-boxed remediation.
- Track FocusTag updates (e.g., if KEV status changes or new PoCs emerge) to adjust urgency and outreach cadence.
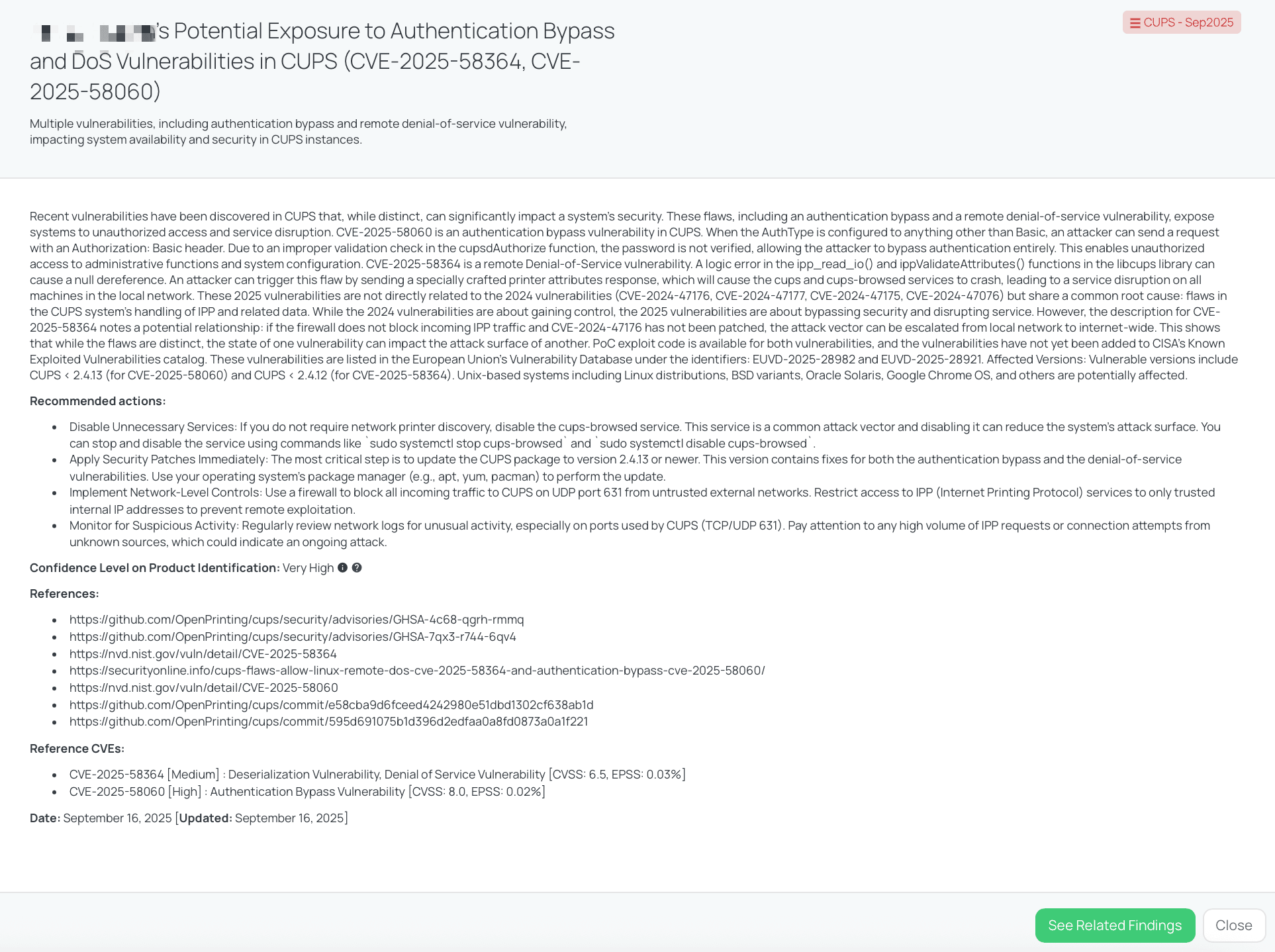
Black Kite’s CUPS – Sep2025 FocusTagTM details critical insights on the event for TPRM professionals.
ENHANCING TPRM OUTCOMES WITH BLACK KITE'S FOCUSTAGS™
Black Kite’s FocusTags™ convert fast-moving technical disclosures into prioritized third-party actions—especially useful with this week’s mix of service availability (Jetty/CUPS) and CI/CD exposure (Jenkins):
- Immediate vendor pinpointing: Identify which third parties are likely exposed—complete with asset-level evidence (IPs, hostnames, subdomains) tied to Jetty HTTP/2 endpoints, Internet-reachable Jenkins controllers, or CUPS/IPP services.
- Actionable outreach, not noise: Instead of blanketing your entire vendor catalog, engage only those flagged by the relevant tags with targeted questions and request post-patch attestations (version/build, change ticket, date).
- Risk-based prioritization: Elevate vendors whose exposed assets are Internet-facing or business-critical (public APIs, production CI/CD, print services in operational environments).
- Operational workflows: Create vendor segments by tag, set time-boxed remediation checkpoints, and track status changes as tags are updated (e.g., new PoCs, patch releases, or KEV entries).
- TPRM reporting made practical: Roll up remediation progress by tag to give stakeholders a clear view of residual exposure across your supplier ecosystem.
Applied to this week’s tags—Jetty – MadeYouReset, Jenkins – Sep2025, and CUPS – Sep2025—FocusTags™ help your team move from awareness to measurable reduction in third-party risk, quickly and with precision.
ABOUT FOCUS FRIDAY
Every week, we delve into the realms of critical vulnerabilities and their implications from a Third-Party Risk Management (TPRM) perspective. This series is dedicated to shedding light on pressing cybersecurity threats, offering in-depth analyses, and providing actionable insights.
FOCUSTAGS™ IN THE LAST 30 DAYS:
- Jetty – MadeYouReset: CVE-2025-5115, MadeYouReset DoS Vulnerability in Eclipse’s Jetty.
- Jenkins – Sep2025: CVE-2025-59474, CVE-2025-59475, CVE-2025-59476, Information Disclosure Vulnerability, Log Message Injection Vulnerability in Jenkins.
- CUPS – Sep2025: CVE-2025-58364, CVE-2025-58060, Deserialization Vulnerability, Denial of Service Vulnerability, Authentication Bypass Vulnerability in CUPS.
- SharePoint – Sep2025: CVE-2025-54897, CVE-2025-53760, CVE-2025-53760, Deserialization Vulnerability, Code Execution Vulnerability, Server-Side Request Forgery (SSRF) Vulnerability in Microsoft SharePoint.
- MSSQL – Sep2025: CVE-2025-47997, CVE-2025-55227, Race Condition Vulnerability, Command Injection Vulnerability in Microsoft SQL Server.
- SAP NetWeaver – Sep2025: CVE-2025-42944, CVE-2025-42922, CVE-2025-42958, Insecure Deserialization Vulnerability, Insecure File Operations Vulnerability, Missing Authentication Check Vulnerability in SAP NetWeaver.
- Django : CVE-2025-57833, SQL Injection Vulnerability in Django.
- FreePBX : CVE-2025-57819, Remote Code Execution Vulnerability in Sangoma’s FreePBX.
- Vault – Sep2025 : CVE-2025-6203, DoS Vulnerability in HashiCorp Vault.
- Citrix NetScaler – Aug2025 : CVE-2025-7775, CVE-2025-7776, CVE-2025-8424, Memory Overflow Vulnerability, Remote Code Execution Vulnerability, DoS Vulnerability, Improper Access Control Vulnerability in Citrix NetScaler ADC/Gateway.
- Salesforce Tableau – Aug2025 : CVE-2025-26496, CVE-2025-26497, CVE-2025-26498, CVE-2025-52450, CVE-2025-52451, Type Confusion Vulnerability, Remote Code Execution Vulnerability, Unrestricted File Upload Vulnerability, Path Traversal Vulnerability, Improper Input Validation Vulnerability in Salesforce Tableau.
- MadeYouReset HTTP/2 DoS Attack : CVE-2025-8671, CVE-2025-48989, CVE-2025-54500, CVE-2025-55163, CVE-2025-36047, MadeYouReset DoS Vulnerability in HTTP/2.
- Ivanti Connect Secure – Aug2025 : CVE-2025-5456, CVE-2025-5462, Out-of-bound Read Vulnerability, DoS Vulnerability, Buffer Overflow Vulnerability in Ivanti Connect Secure (ICS), Ivanti Policy Secure (IPS), Ivanti ZTA Gateway, Ivanti Neurons for Secure Access.
- PostgreSQL – Aug2025 : CVE-2025-8713, CVE-2025-8714, CVE-2025-8715, Arbitrary Code Injection Vulnerability, Exposure of Sensitive Information Vulnerability in PostgreSQL.
- Plesk Obsidian : CVE-2025-54336, Incorrect Comparison Vulnerability in Plesk Obsidian.
- Exchange Server – Aug2025 : CVE-2025-53786, CVE-2025-25005, CVE-2025-25006, CVE-2025-25007, CVE-2025-33051, Improper Authentication, Input Validation, and Information Disclosure Vulnerabilities.
- MSSQL – Aug2025 : CVE-2025-49758, CVE-2025-24999, CVE-2025-53727, CVE-2025-49759, CVE-2025-47954, Privilege Escalation and SQL Injection Vulnerabilities.
See Black Kite’s full CVE Database and the critical TPRM vulnerabilities that have an applied FocusTagTM at https://blackkite.com/cve-database.
REFERENCES
https://nvd.nist.gov/vuln/detail/CVE-2025-5115
https://www.jenkins.io/security/advisory/2025-09-17
https://github.com/advisories/GHSA-mmxm-8w33-wc4h
https://securityonline.info/jenkins-patches-high-severity-vulnerabilities-including-a-dos-flaw
https://radar.offseq.com/threat/cve-2025-59474-vulnerability-in-jenkins-project-je-cfdf6306
https://radar.offseq.com/threat/cve-2025-59475-vulnerability-in-jenkins-project-je-73e5d03d
https://radar.offseq.com/threat/cve-2025-59476-vulnerability-in-jenkins-project-je-18d005b1
https://nvd.nist.gov/vuln/detail/CVE-2025-59474
https://nvd.nist.gov/vuln/detail/CVE-2025-59475
https://nvd.nist.gov/vuln/detail/CVE-2025-59476
https://www.jenkins.io/security/advisory/2025-09-17/#SECURITY-3594
https://github.com/OpenPrinting/cups/security/advisories/GHSA-4c68-qgrh-rmmq
https://github.com/OpenPrinting/cups/security/advisories/GHSA-7qx3-r744-6qv4
https://nvd.nist.gov/vuln/detail/CVE-2025-58364
https://nvd.nist.gov/vuln/detail/CVE-2025-58060
https://github.com/OpenPrinting/cups/commit/e58cba9d6fceed4242980e51dbd1302cf638ab1d
https://github.com/OpenPrinting/cups/commit/595d691075b1d396d2edfaa0a8fd0873a0a1f221