Focus Friday: TPRM Insights On Cleo File Transfer, BeyondTrust PRA and RS, and Ivanti Cloud Services Application Vulnerabilities
Welcome to this week’s Focus Friday, where we delve into high-profile vulnerabilities and provide actionable insights from a Third-Party Risk Management (TPRM) perspective. This edition explores critical vulnerabilities in Cleo File Transfer, BeyondTrust PRA RS, and Ivanti Cloud Services Application. These vulnerabilities, including remote code execution and command injection, could potentially compromise sensitive data and disrupt operations across industries. These vulnerabilities demand immediate attention from TPRM professionals to mitigate risks effectively. Let’s explore the risks, the recommended remediations, and how Black Kite’s FocusTags™ streamline the risk management process for these pressing concerns.
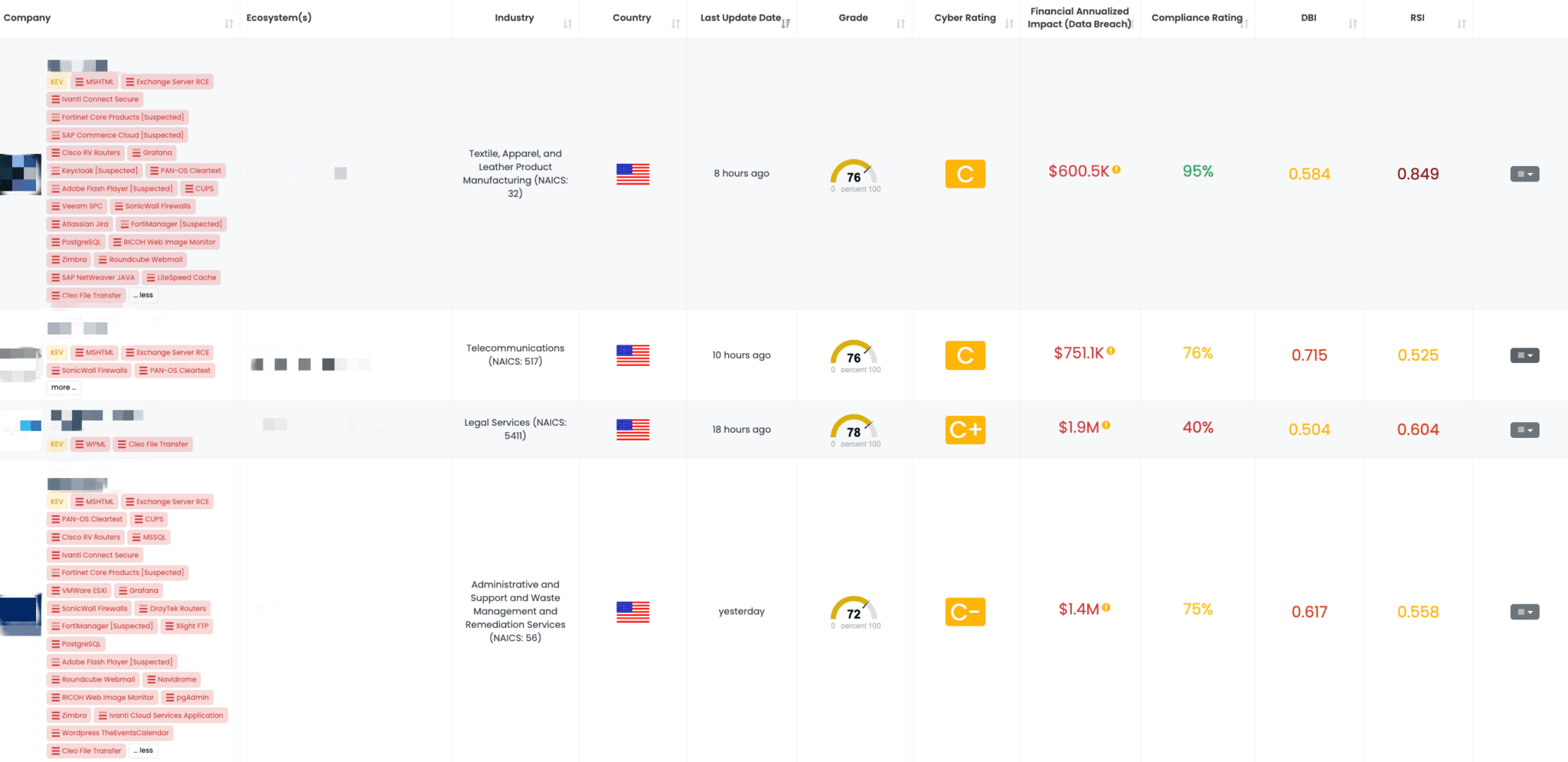
Filtered view of companies with Cleo File Transfer FocusTag™ on the Black Kite platform.
CVE-2024-55956 in Cleo File Transfer Software
What are the critical vulnerabilities in Cleo File Transfer software?
In our Focus Friday blog post last week, we discussed Cleo’s critical vulnerability, CVE-2024-50623. This week, we need to focus on CVE-2024-55956, which affects Cleo File Transfer products, and the systemic risks these vulnerabilities pose.
In our December 18 article titled “CL0P’s Exploitation of Cleo Directly Endangers the Supply Chain,” we detailed how the CL0P ransomware group has been exploiting vulnerabilities in Cleo’s software to threaten supply chains.
Two critical vulnerabilities have been identified in Cleo Harmony®, Cleo VLTrader®, and Cleo LexiCom® products:
CVE-2024-55956 is the Remote Code Execution Vulnerability in Cleo Harmony, VLTrader, and LexiCom versions prior to 5.8.0.24, enabling unauthenticated users to execute arbitrary Bash or PowerShell commands by exploiting default settings in the Autorun directory.
Both vulnerabilities have been actively exploited. CVE-2024-50623 was added to CISA’s Known Exploited Vulnerabilities catalog on December 13, 2024. CISA CVE-2024-55956 was added on December 17, 2024. Cleo has released patches to address these issues, and users are strongly advised to update to the latest versions to mitigate potential risks.
Both vulnerabilities have public PoC exploit codes, and exploitation has been observed targeting industries like logistics and shipping. They enable unauthorized file uploads and remote execution of malicious commands.
Why should TPRM professionals care about these vulnerabilities?
These vulnerabilities represent significant risks for organizations relying on Cleo file transfer solutions:
- Critical Operational Risk: Exploitation could lead to compromised file transfers, impacting supply chain and logistics operations.
- Sensitive Data Exposure: Malicious actors could access and exfiltrate confidential business data.
- Unauthorized Access: Successful exploitation provides attackers with system-level access, enabling further attacks on connected systems.
For organizations utilizing Cleo products, timely mitigation is essential to avoid disruption and ensure data security.
What questions should TPRM professionals ask vendors about these vulnerabilities?
- Have you updated all instances of Cleo Harmony, VLTrader, and LexiCom to version 5.8.0.24 or later to mitigate the risk of CVE-2024-50623 and CVE-2024-55956?
- Have you reviewed and appropriately configured the Autorun directory’s default settings to prevent unauthorized command execution related to CVE-2024-55956?
- Can you confirm if you have blocked the attacker IPs mentioned in the advisory shared last week, including 176[.]123[.]5[.]126, 5[.]149[.]249[.]226, 185[.]181[.]230[.]103, 209[.]127[.]12[.]38, 181[.]214[.]147[.]164, and 192[.]119[.]99[.]42, to prevent further exploitation of CVE-2024-50623 and CVE-2024-55956?
- Have you disabled the Autorun functionality in the ‘Configure’ menu of LexiCom, Harmony, or VLTrader to stop processing autorun files and mitigate the risk of CVE-2024-55956?
Remediation recommendations for vendors subject to this risk
To address these vulnerabilities, vendors should:
- Immediate Software Update: Upgrade all instances of Cleo Harmony, VLTrader, and LexiCom to version 5.8.0.24 or later to mitigate the vulnerability.
- Review Autorun Directory Settings: Ensure that the Autorun directory’s default settings are appropriately configured to prevent unauthorized command execution.
- Block Malicious IPs: Consider blocking attacker IPs, including 176.123.5.126, 5.149.249.226, 185.181.230.103, 209.127.12.38, 181.214.147.164, 192.119.99.42.
- Monitor for Indicators of Compromise (IOCs): Check if suspicious files, such as main.xml or 60282967-dc91-40ef-a34c-38e992509c2c.xml, healthchecktemplate.txt, or healthcheck.txt, contain encoded malicious commands. The attack also utilizes reconnaissance tools like nltest.exe for Active Directory enumeration.
- Monitor Updates: Cleo is actively working on a new patch expected soon. Monitor updates from Cleo to ensure you apply the latest mitigations as they are released.
- Reconfigure Software Settings: Disable the autorun feature by clearing the ‘Autorun Directory’ field in configuration settings to prevent automatic execution of malicious files.
- Place Systems Behind a Firewall: Ensure internet-facing Cleo systems are placed behind a firewall to limit exposure to potential attacks.
- Implement Strong Security Practices: Enforce strong, unique passwords and enable multi-factor authentication (MFA) to enhance security.
- Disable Autorun Functionality: Access the “Configure” menu in LexiCom, Harmony, or VLTrader. Select “Options” and navigate to the “Other” pane. Delete the contents of the “Autorun Directory” field to stop processing autorun files.
- Address Remaining Exposure: Note that this mitigates part of the attack but does not address the root cause of the vulnerability.
How TPRM professionals can leverage Black Kite for this vulnerability
Black Kite published the Cleo File Transfer FocusTag™ on December 13, 2024, providing actionable insights for TPRM professionals. This tag identifies vendors using affected versions and details exposed assets like subdomains and IP addresses.
With Black Kite, TPRM professionals can:
- Prioritize vendors requiring urgent remediation based on exposure.
- Streamline risk assessments using targeted questions and vendor-specific intelligence.
- Enhance oversight by monitoring identified vulnerable assets.
This FocusTag™ ensures efficient vendor management and proactive risk mitigation, empowering TPRM professionals to address critical vulnerabilities effectively.
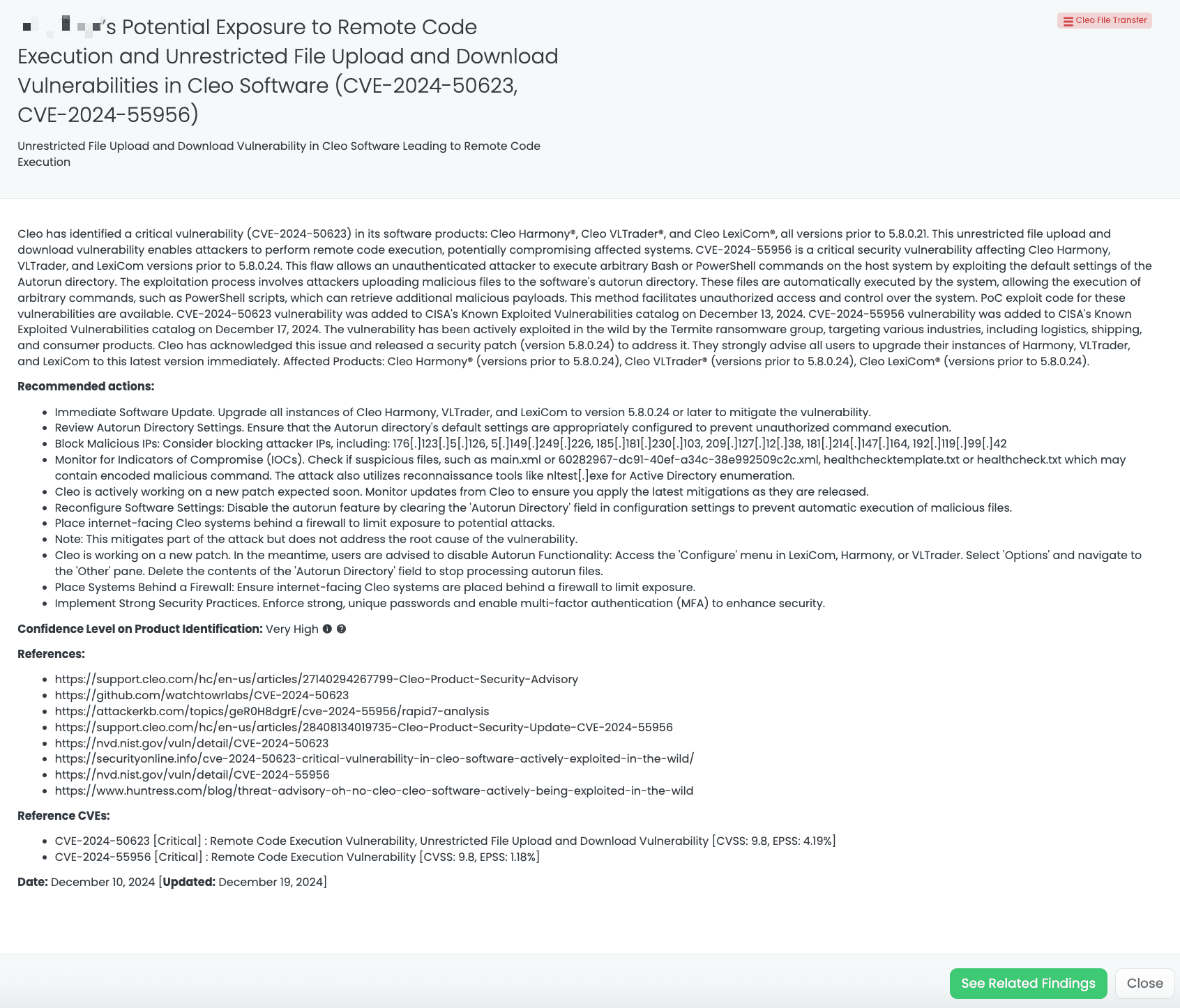
Black Kite’s Cleo File Transfer FocusTagTM details critical insights on the event for TPRM professionals.
CVE-2024-11639, CVE-2024-11772, and CVE-2024-11773 in Ivanti Cloud Services Application
The Ivanti Cloud Services Appliance (CSA) is an internet-facing device that facilitates secure communication between remote endpoints and the central Ivanti Endpoint Manager core server. It enables organizations to manage devices outside their corporate network, ensuring that endpoints can receive updates, patches, and policies regardless of their location. The key features of the Ivanti Cloud Services Appliance (CSA) include: Secure Remote Management, Certificate-Based Authentication, Support for Multiple Appliances, and Virtual Appliance Option.
What are the critical vulnerabilities in Ivanti Cloud Services Application?
These vulnerabilities impact versions of Ivanti CSA prior to 5.0.3 and include the following:
CVE-2024-11639 is an authentication bypass vulnerability in the admin web console of Ivanti Cloud Services Appliance (CSA) versions before 5.0.3, allowing remote unauthenticated attackers to gain administrative access.
CVE-2024-11772 is a command injection vulnerability in the admin web console of Ivanti CSA before version 5.0.3, enabling remote authenticated attackers with administrative privileges to execute arbitrary code on the server.
CVE-2024-11773 is an SQL injection vulnerability in the admin web console of Ivanti CSA before version 5.0.3, allowing remote authenticated attackers with administrative privileges to execute arbitrary SQL statements.
All three vulnerabilities are critical, with CVE-2024-11639 having a CVSS score of 10.0, and both CVE-2024-11772 and CVE-2024-11773 each having a CVSS score of 9.1.
These vulnerabilities were first disclosed on December 10, 2024, with no current evidence of exploitation in the wild. However, considering the history of rapid exploitation of Ivanti vulnerabilities, immediate action is advised. They are not yet listed in CISA’s KEV catalog.
Why should TPRM professionals care about these vulnerabilities?
For TPRM professionals, these vulnerabilities in Ivanti CSA could lead to severe business risks:
- Compromised Administrative Access: Unauthorized access to the admin web console may result in full control of systems managing critical IT infrastructure.
- Arbitrary Code Execution: Attackers could deploy malicious software, escalating risks to other connected systems.
- SQL Injection Risks: Exploited vulnerabilities could enable attackers to manipulate databases, potentially exposing sensitive organizational data.
Organizations leveraging Ivanti CSA for IT management need to ensure their vendors have addressed these risks to prevent potential disruptions and data breaches.
What questions should TPRM professionals ask vendors about these vulnerabilities?
- Have you updated all instances of Ivanti CSA to version 5.0.3 or later to mitigate the risk of CVE-2024-11639, CVE-2024-11772, and CVE-2024-11773?
- Can you confirm if you have implemented continuous monitoring for unusual activities in the admin web console to detect potential exploitation of the authentication bypass, command injection, and SQL injection vulnerabilities?
- Have you enforced strong, unique passwords and enabled multi-factor authentication for all administrative accounts to prevent unauthorized administrative access related to CVE-2024-11639?
- Can you confirm if you have restricted administrative access to the CSA to only authorized personnel to prevent potential exploitation of CVE-2024-11772 and CVE-2024-11773?
Remediation recommendations for vendors subject to this risk
Vendors using Ivanti CSA should implement the following recommendations:
- Upgrade to Ivanti CSA version 5.0.3: This update resolves these vulnerabilities and is available via the Ivanti download portal.
- Restrict Administrative Access: Limit access to authorized personnel only and enforce MFA.
- Monitor for Unusual Activity: Implement continuous monitoring for signs of exploitation in the admin web console.
- Review Database Activity: Ensure SQL queries are logged and anomalous activity is flagged.
How TPRM professionals can leverage Black Kite for this vulnerability
Black Kite published the Ivanti Cloud Services Application FocusTag™ on December 13, 2024, providing actionable insights. This tag identifies vendors potentially exposed to these vulnerabilities, detailing the affected assets, including subdomains and IP addresses.
By leveraging these insights, TPRM professionals can:
- Narrow the scope to vendors with confirmed exposure to affected Ivanti CSA versions.
- Prioritize outreach to these vendors using the specific questions provided.
- Address potential risks more efficiently with the detailed intelligence provided.
Black Kite’s FocusTags™ eliminate the guesswork in identifying vulnerable vendors, streamlining the risk assessment process for TPRM professionals.
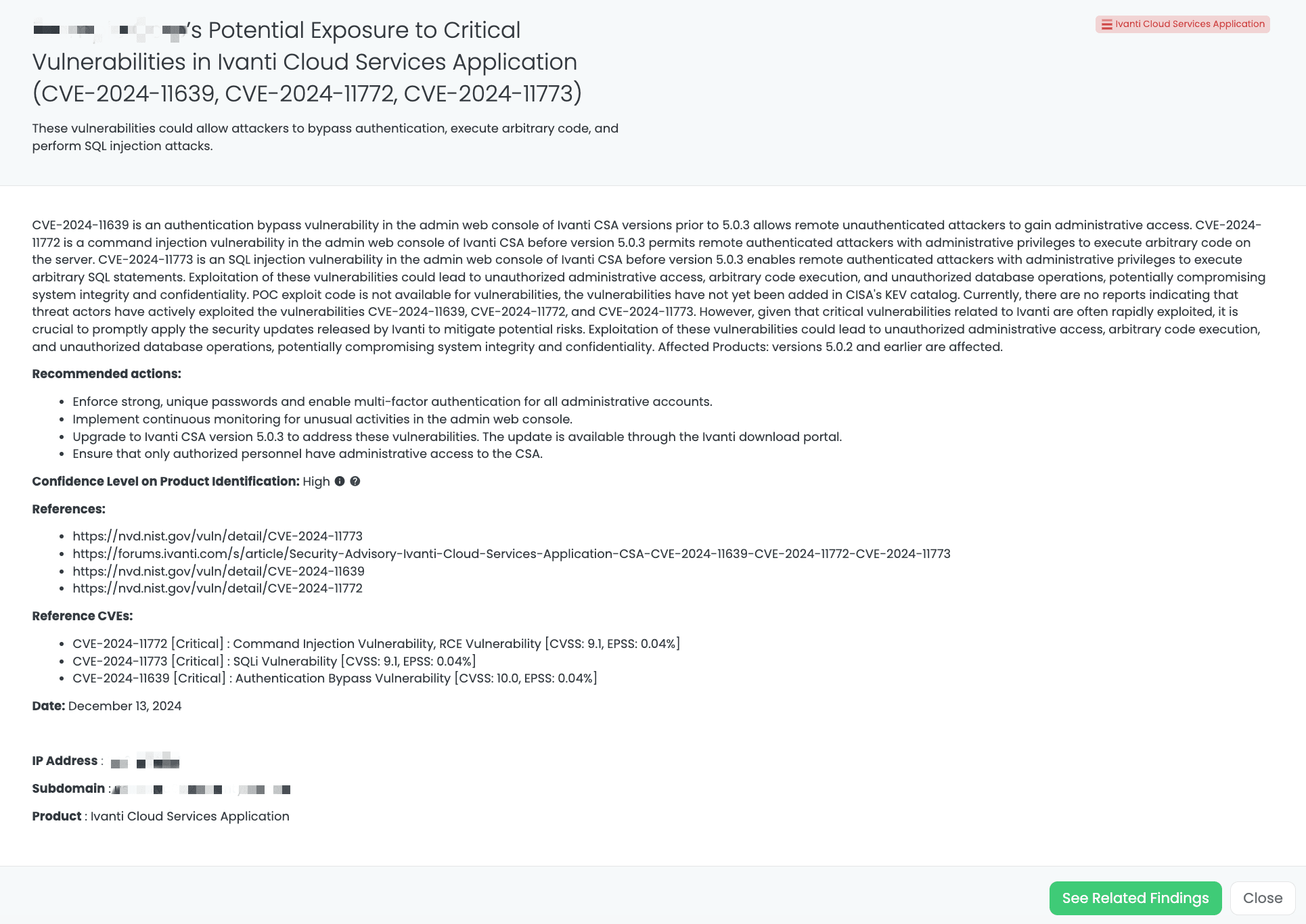
Black Kite’s Ivanti Cloud Services Application FocusTagTM details critical insights on the event for TPRM professionals.
CVE-2024-12356 in BeyondTrust PRA and RS
What is the BeyondTrust PRA and RS Command Injection Vulnerability?
CVE-2024-12356 is a critical command injection vulnerability affecting BeyondTrust’s Privileged Remote Access (PRA) and Remote Support (RS) solutions. It allows unauthenticated remote attackers to execute operating system commands as the site user by sending malicious client requests. A vulnerability with a CVSS score of 9.8 has been identified, affecting PRA and RS software versions up to and including 24.3.1. Publicly disclosed on December 16, 2024, this vulnerability poses a significant security risk due to the availability of PoC exploit code, making it a high-priority target for attackers despite no reports of active exploitation thus far. The vulnerability’s critical nature has also led to its inclusion in the CISA Known Exploited Vulnerabilities (KEV) Catalog on December 19, 2024. With an EPSS score of 0.05%, organizations using the affected versions are urged to address this issue promptly to mitigate potential risks.
The vulnerability stems from improper neutralization of special elements used in commands, making it exploitable via a low-complexity attack. BeyondTrust has released patches for all supported versions (22.1.x and above).
Why should TPRM professionals care about this vulnerability?
BeyondTrust’s PRA and RS solutions are widely used for privileged remote access and IT support, making them an attractive target for attackers. Exploitation of this vulnerability could:
- Compromise Sensitive Systems: Grant unauthorized access to critical infrastructure and systems.
- Enable Further Attacks: Attackers could escalate privileges, deploy malware, or steal sensitive information.
- Disrupt Operations: Unauthorized access to IT management systems could lead to downtime or operational disruption.
Organizations using BeyondTrust products need to address this vulnerability urgently to protect against potential exploitation.
What questions should TPRM professionals ask vendors about this vulnerability?
- Can you confirm if you have upgraded all instances of BeyondTrust’s Privileged Remote Access (PRA) and Remote Support (RS) products to a version higher than 24.3.1 to mitigate the risk of CVE-2024-12356?
- If you are operating on a version older than 22.1, have you upgraded to a supported version to access the patches for the command injection vulnerability identified as CVE-2024-12356?
- Have you applied the appropriate patch (BT24-10-ONPREM1 or BT24-10-ONPREM2, depending on the version) via the /appliance interface to address the CVE-2024-12356 vulnerability in BeyondTrust’s PRA and RS products?
- Have you implemented continuous monitoring systems to detect any unusual activity that may indicate attempted exploitation of the CVE-2024-12356 vulnerability in BeyondTrust’s PRA and RS products?
Remediation recommendations for vendors subject to this risk
To mitigate the risks associated with CVE-2024-12356, vendors should:
- Apply the Patch: Install BT24-10-ONPREM1 or BT24-10-ONPREM2 for versions 22.1.x or above.
- Upgrade Older Versions: For unsupported versions (older than 22.1), upgrade to a supported version before applying the patch.
- Verify Patch Application: Ensure successful deployment of the patch, particularly for on-premise instances.
- Monitor for Indicators: Regularly review logs for suspicious activity tied to command injection attempts.
- Implement Security Best Practices: Enforce multi-factor authentication (MFA) and use strong, unique passwords to secure administrative accounts.
How TPRM professionals can leverage Black Kite for this vulnerability
Black Kite released the BeyondTrust PRA RS FocusTag™ on December 19, 2024, offering detailed insights into vendors potentially impacted by CVE-2024-12356. The tag provides:
- Identification of affected vendors with PRA and RS deployments.
- Details on exposed assets, including IP addresses and subdomains.
TPRM professionals can use these insights to:
- Narrow down their scope to vendors with confirmed exposure.
- Prioritize outreach to affected vendors and provide actionable guidance.
- Leverage asset data to enhance risk assessments and address vulnerabilities proactively.
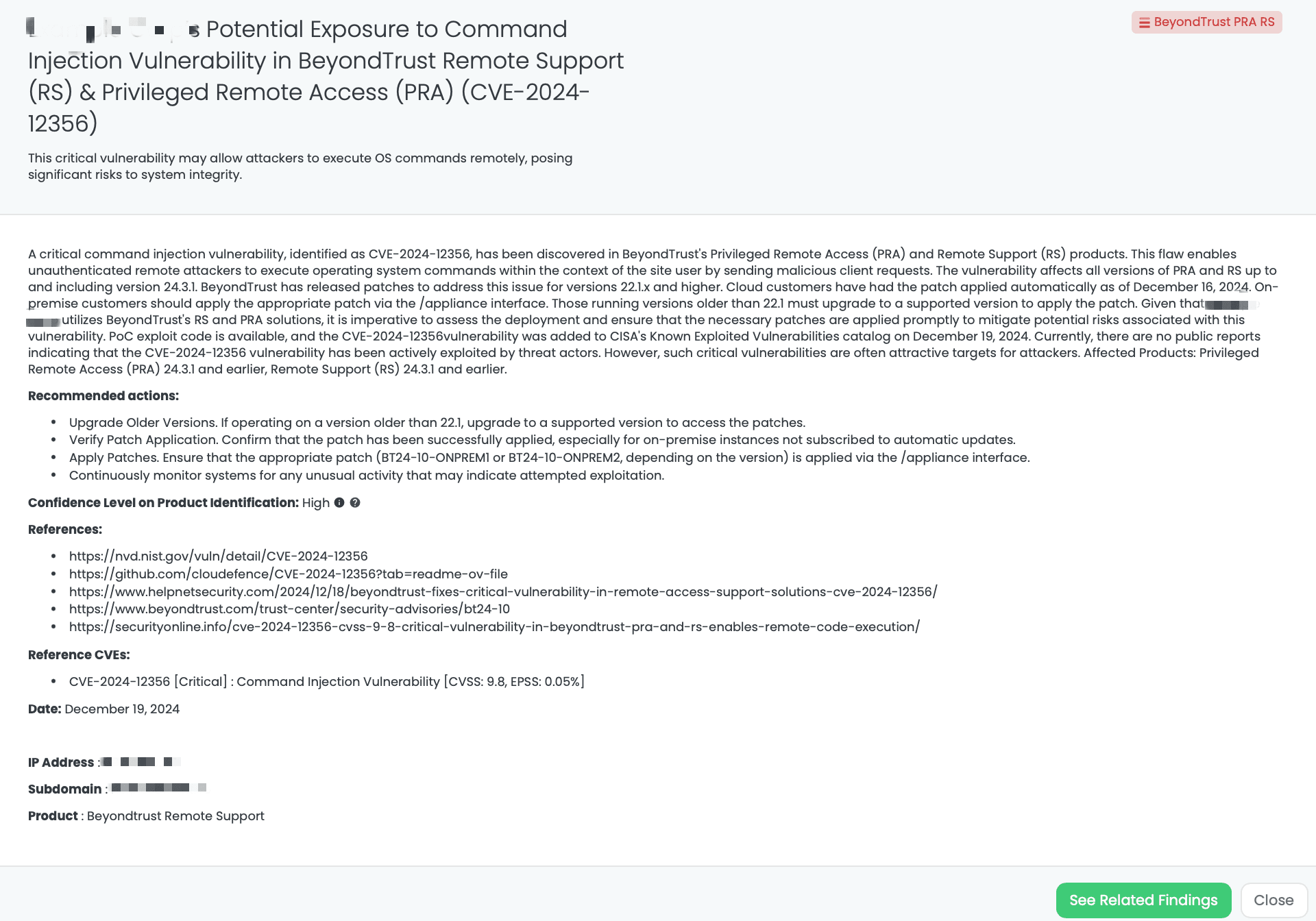
Black Kite’s BeyondTrust PRA RS FocusTagTM details critical insights on the event for TPRM professionals.
ENHANCING TPRM STRATEGIES WITH BLACK KITE’S FocusTags™
In the face of increasingly sophisticated cyber threats, Black Kite’s FocusTags™ stand as a beacon for proactive Third-Party Risk Management (TPRM). This week’s vulnerabilities—spanning critical systems like Cleo File Transfer, BeyondTrust PRA RS, and Ivanti Cloud Services Application—highlight the pressing need for targeted, efficient, and informed risk management strategies. Here’s how FocusTags™ enhance TPRM practices:
- Real-Time Risk Identification: Instantly pinpoint vendors impacted by the latest vulnerabilities, enabling rapid responses that mitigate potential threats.
- Strategic Risk Prioritization: Evaluate risks based on the criticality of vendors and the severity of vulnerabilities, ensuring focused efforts where they matter most.
- Informed Vendor Conversations: Provide the intelligence necessary to engage vendors in detailed discussions about their exposure and response strategies, fostering transparency and collaboration.
- Strengthened Cybersecurity Ecosystems: Deliver a comprehensive view of the evolving threat landscape, empowering organizations to build resilient and adaptive security frameworks.
By transforming complex cybersecurity data into actionable insights, Black Kite’s FocusTags™ revolutionize TPRM, ensuring businesses can protect their supply chains and partners against even the most sophisticated cyber threats. As vulnerabilities continue to emerge, these tags provide the clarity and precision needed for proactive and effective risk management.
Want to take a closer look at FocusTags™?
Take our platform for a test drive and request a demo today.
Request a Demo
About Focus Friday
Every week, we delve into the realms of critical vulnerabilities and their implications from a Third-Party Risk Management (TPRM) perspective. This series is dedicated to shedding light on pressing cybersecurity threats, offering in-depth analyses, and providing actionable insights.
FocusTagsTM in the Last 30 Days:
- BeyondTrust PRA RS: CVE-2024-12356, Command Injection Vulnerability in BeyondTrust’s Privileged Remote Access (PRA), Remote Support (RS).
- Ivanti Cloud Services Application: CVE-2024-11639, CVE-2024-11772, CVE-2024-11772, Authentication Bypass Vulnerability Command Injection Vulnerability, and RCE Vulnerability SQLi Vulnerability in Ivanti Cloud Services Application.
- Cleo File Transfer: CVE-2024-50623, CVE-2024-55956, Remote Code Execution Vulnerability, Unrestricted File Upload and Download Vulnerability in Cleo Harmony, VLTrader, LexiCom.
- Qlik Sense Enterprise: CVE-2024-55579, CVE-2024-55580, Arbitrary EXE Execution Vulnerability Remote Code Execution Vulnerability in Qlik Sense Enterprise.
- SAP NetWeaver JAVA: CVE-2024-47578, Server-Side Request Forgery (SSRF) Vulnerability in SAP NetWeaver AS for JAVA (Adobe Document Services).
- PAN-OS: CVE-2024-0012, CVE-2024-9474, Authentication Bypass Vulnerability and Privilege Escalation Vulnerability in Palo Alto’s PAN-OS.
- PostgreSQL: CVE-2024-10979, Arbitrary Code Execution Vulnerability in PostgreSQL.
- Apache Airflow: CVE-2024-45784, Debug Messages Revealing Unnecessary Information in Apache Airflow.
- Atlassian Jira: CVE-2021-26086, Path Traversal Vulnerability in Atlassian Jira Server and Data Center.
- Ivanti Connect Secure: CVE-2024-9420, CVE-2024-47906, CVE-2024-38655, CVE-2024-38656, CVE-2024-39710, CVE-2024-11007, CVE-2024-11006, CVE-2024-11005, and CVE-2024-11004, Use-After-Free, Stack-Based Buffer Overflow, Argument Injection, and Reflected XSS Vulnerabilities in Ivanti Connect Secure.
References
https://nvd.nist.gov/vuln/detail/CVE-2024-55956
https://attackerkb.com/topics/geR0H8dgrE/cve-2024-55956/rapid7-analysis
https://nvd.nist.gov/vuln/detail/CVE-2024-11639
https://nvd.nist.gov/vuln/detail/CVE-2024-11772
https://nvd.nist.gov/vuln/detail/CVE-2024-11773
https://www.beyondtrust.com/trust-center/security-advisories/bt24-10