Focus Friday: TPRM Insights Into FortiWeb, SolarWinds Serv-U, OAuth2 Proxy, pgAdmin, and W3 Total Cache Vulnerabilities
INTRODUCTION
Note about the emerging Salesforce/Gainsight OAuth breach: the Black Kite Research Group is fast-tracking a new FocusTag to go live on the platform today (Friday, November 21, 2025). A detailed analysis will follow soon. Stay tuned for our full deep dive!
Welcome to this week’s Focus Friday, where we take a close look at several high-impact vulnerabilities that have surfaced across widely used technologies. This edition evaluates critical issues affecting FortiWeb, SolarWinds Serv-U, OAuth2 Proxy, pgAdmin, and the W3 Total Cache WordPress plugin—all of which present meaningful implications for organizations that rely on third-party vendors. Each of these vulnerabilities introduces a unique risk pathway, from remote code execution to authentication bypass and command injection. As always, this blog approaches these incidents from a Third-Party Risk Management (TPRM) perspective, equipping you with the context, questions, and actions needed to engage effectively with your vendors.
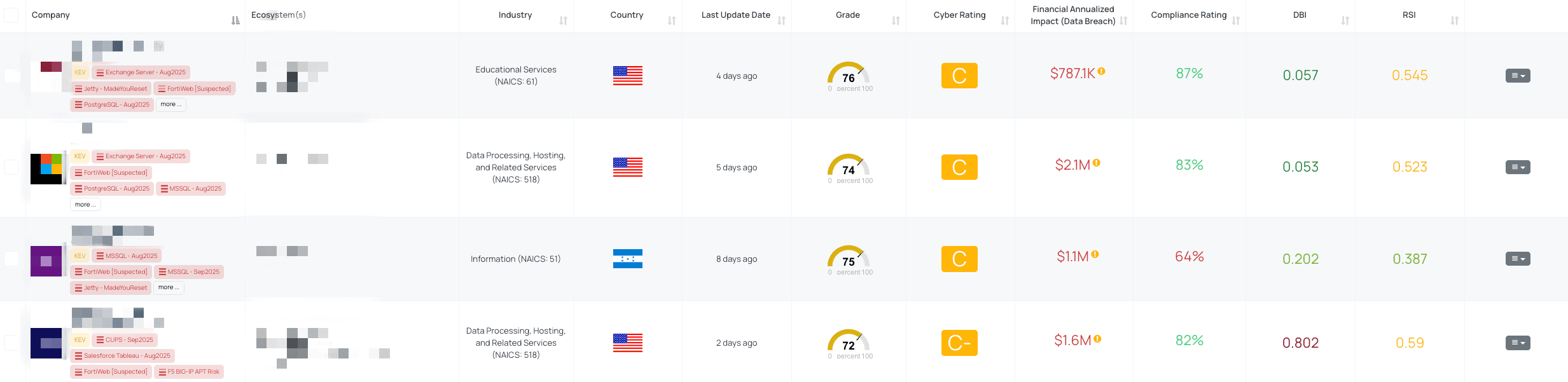
Filtered view of companies with FortiWeb FocusTag™ on the Black Kite platform.
CVE-2025-64446 & CVE-2025-58034 (FortiWeb)
What are the FortiWeb Authentication Bypass and OS Command Injection Vulnerabilities (CVE-2025-64446 & CVE-2025-58034)?
CVE-2025-64446 and CVE-2025-58034 are two high-impact vulnerabilities affecting Fortinet FortiWeb web application firewalls. Together, they create a path from unauthenticated compromise to system-level execution, making this combination particularly dangerous in real-world environments.
CVE-2025-64446
- Type: Authentication Bypass + Relative Path Traversal
- Severity: CVSS 9.8 (Critical)
- EPSS: 82.39%
- Published: November 14, 2025
- Exploited in the wild: Yes
- KEV Status: Added November 14, 2025
CVE-2025-58034
- Type: OS Command Injection (CWE-78)
- Severity: CVSS 7.2 (High)
- EPSS: Not provided
- Published: Late 2025 via vendor advisory
- Exploited in the wild: Yes (per KEV)
- KEV Status: Added November 18, 2025
- Known ransomware use: Unknown
When chained, these vulnerabilities escalate impact significantly:
- CVE-2025-64446 provides unauthenticated attackers full administrative control over FortiWeb.
- CVE-2025-58034 allows OS-level command execution from an authenticated context—making it trivial for attackers who exploited CVE-2025-64446 to elevate into full system compromise.
CVE-2025-64446 technical breakdown
CVE-2025-64446 is a critical pre-authentication vulnerability affecting Fortinet FortiWeb web application firewalls. It combines a relative path traversal flaw with a logic error in the authentication mechanism, enabling a remote, unauthenticated attacker to gain full administrative control of the appliance. The vulnerability carries a CVSS score of 9.8 (Critical) and an EPSS value of 82.39%, reflecting its high likelihood of exploitation.
The issue was publicly disclosed and assigned a CVE identifier on November 14, 2025, coinciding with the publication of Fortinet’s advisory and the release of the National Vulnerability Database entry. On the same day, CISA added CVE-2025-64446 to the Known Exploited Vulnerabilities (KEV) catalog.
This vulnerability is actively exploited in the wild. Research teams observed exploitation attempts as early as October 6, 2025, including unauthorized creation of administrator accounts, access to the CLI through backend interfaces, and automated payloads distributed across multiple regions. ENISA’s EU Vulnerability Database lists the issue under ID EUVD-2025-197613.
The exploit chain relies on two core steps:
Path traversal into the internal CGI backend
Attackers manipulate API paths using directory traversal sequences, redirecting requests from the FortiWeb API into the backend fwbcgi binary. A representative malicious request structure includes sequences that escape the API directory and reach cgi-bin/fwbcgi.
Authentication bypass via a crafted CGIINFO header
Inside the fwbcgi binary, user identity is derived from a Base64-encoded JSON object in a non-standard CGIINFO header. The function intended to handle authentication misinterprets this data as trusted user context, enabling attackers to impersonate any user—including the built-in admin account—without a password. Attackers frequently create persistent administrative accounts (e.g., “Testpoint”, “trader”, “trader1”, “test1234point”) with unrestricted trust hosts.
CVE-2025-58034 technical breakdown
CVE-2025-58034 is an Improper Neutralization of Special Elements used in an OS Command (“OS Command Injection”) vulnerability in Fortinet FortiWeb. An authenticated attacker may execute unauthorized code on the underlying system via crafted HTTP requests or CLI commands.
- Severity: CVSS 7.2 (High)
- CWE: CWE-78
- KEV Status: Added November 18, 2025
- Real-world exploitation: Yes (per KEV)
- Ransomware use: Unknown
While CVE-2025-58034 requires authentication, it becomes critical when paired with CVE-2025-64446. Once authentication is bypassed, attackers gain direct access to exploit OS command injection, giving them complete control over the underlying operating system.
Affected Versions:
CVE-2025-64446 (Authentication Bypass & Path Traversal)
- FortiWeb 8.0: versions before 8.0.2
- FortiWeb 7.6: versions before 7.6.5
- FortiWeb 7.4: versions before 7.4.10
- FortiWeb 7.2: versions before 7.2.12
- FortiWeb 7.0: versions before 7.0.12
- FortiWeb 6.4: versions up to and including 6.4.3
- FortiWeb 6.3: versions up to and including 6.3.23
CVE-2025-58034 (OS Command Injection)
- FortiWeb 8.0.0 through 8.0.1
- FortiWeb 7.6.0 through 7.6.5
- FortiWeb 7.4.0 through 7.4.10
- FortiWeb 7.2.0 through 7.2.11
- FortiWeb 7.0.0 through 7.0.11
Why TPRM professionals should care about CVE-2025-64446 and CVE-2025-58034
FortiWeb appliances act as a front-line security layer for critical web applications, APIs, and customer-facing portals. Compromise of a vendor’s FortiWeb instance has significant third-party risk implications:
Bypassing security controls
An attacker with admin access can weaken or disable WAF rules, whitelist malicious traffic, or introduce configuration changes that expose downstream applications.
Inspection and manipulation of sensitive traffic
When FortiWeb terminates TLS sessions, an attacker gains visibility into decrypted data, session cookies, credentials, and API traffic, and may modify responses sent to users.
Internal pivoting
FortiWeb appliances typically have direct access to internal application servers, making them attractive pivot points for deeper network compromise.
Stealthy persistence
Attackers often create new admin accounts with broad trust hosts, which can remain unnoticed even after patching unless specifically investigated.
OS-level compromise via CVE-2025-58034
Once CVE-2025-64446 is exploited, attackers can leverage CVE-2025-58034 to run arbitrary OS commands, deploy implants, remove logs, and pivot further into the vendor network.
What questions should TPRM professionals ask vendors about CVE-2025-64446?
When communicating with vendors, targeted questions can help determine whether meaningful remediation and compromise assessment have been performed:
- Can you confirm if you have updated all instances of Fortinet FortiWeb to the patched versions (8.0.2, 7.6.5, 7.4.10, 7.2.12, 7.0.12, or later versions for 6.4 and 6.3 branches) to mitigate the risk of CVE-2025-64446 and CVE-2025-58034?
- Have you implemented measures to detect and prevent Path Traversal attacks, specifically looking for requests containing the substring ../../.. followed by cgi-bin/fwbcgi, as recommended in the advisory for CVE-2025-64446?
- Have you put in place mechanisms to monitor for unauthorized administrative accounts or suspicious login attempts, as this is a known post-exploitation action related to CVE-2025-58034?
- Have you reviewed your network segmentation and access controls to ensure that FortiWeb appliances are properly segmented from critical internal networks and that administrative interfaces are not exposed to the public internet unless absolutely necessary, with strict access controls in place, as recommended in the advisory for CVE-2025-64446 and CVE-2025-58034?
Remediation recommendations for vendors subject to this risk
Vendors should follow these actions to fully address CVE-2025-64446:
- Apply security updates immediately
Upgrade to the fixed versions that resolve both CVE-2025-64446 and CVE-2025-58034. - Restrict management interface exposure
Ensure management portals are not accessible from the public internet. Limit access to dedicated management networks or VPN-secured channels and enforce MFA and IP allowlisting. - Conduct targeted compromise hunting
Review logs for: - Requests reaching cgi-bin/fwbcgi through path traversal
- Presence of non-standard CGIINFO headers
- Any newly created or modified admin accounts with generic or suspicious names, and trust hosts set to 0.0.0.0/0 or ::/0
- Treat evidence of compromise seriously
If indicators are found, rebuild the device from a trusted baseline, rotate admin credentials and TLS keys, and validate WAF policies and downstream systems for tampering. - Harden future deployments
Implement least-privilege administrative models, segment management access, and monitor configuration changes and administrative logins.
How TPRM professionals can leverage Black Kite for this vulnerability
Black Kite’s FortiWeb [Suspected] FocusTag helps organizations quickly determine which vendors may be exposed to CVE-2025-64446. Released on November 17, 2025, the tag reflects a medium confidence level and correlates externally observable data—such as exposed IPs or domains that appear to be hosting FortiWeb—against known vulnerable version ranges and behavioral indicators.
TPRM teams can operationalize this tag by:
- Rapidly reducing scope
Filter the vendor ecosystem to only those marked with the FortiWeb [Suspected] tag, avoiding broad questionnaires. - Prioritizing based on exploitation likelihood
Because the vulnerability is listed in KEV, has a critical CVSS score, and carries a high EPSS value, tagged vendors should be treated as high priority. - Issuing focused, technically specific questionnaires
Ask vendors about exact indicators such as traversal paths to fwbcgi, unauthorized admin accounts, and the presence of CGIINFO headers. - Discussing concrete exposed assets
Black Kite provides asset-level intelligence (IP addresses and subdomains) where FortiWeb exposure appears likely, enabling targeted and informed vendor conversations. - Tracking vendor remediation over time
As vendors patch or remove vulnerable systems, updated external intelligence helps confirm the reduction of exposure.
This approach allows TPRM teams to understand real-world exposure, validate vendor security actions, and focus resources precisely where risk is present.

Black Kite’s FortiWeb [Suspected] FocusTag™ details critical insights on the event for TPRM professionals.
CVE-2025-40547, CVE-2025-40548, CVE-2025-40549 (SolarWinds Serv-U - Nov2025)
What are the latest critical SolarWinds Serv-U vulnerabilities?
CVE-2025-40547, CVE-2025-40548, and CVE-2025-40549 are three critical vulnerabilities in SolarWinds Serv-U (both FTP Server and Managed File Transfer Server) that enable remote code execution (RCE) when abused by an authenticated administrator. All three issues affect Serv-U prior to version 15.5.3, and SolarWinds has released patches to address them, urging customers to upgrade without delay.
Each vulnerability carries a CVSS score of 9.1 (Critical). According to the Focus Tag, the EPSS scores are:
- CVE-2025-40547 – Logic error leading to RCE (EPSS: 0.07%)
- CVE-2025-40548 – Improper authorization / broken access control enabling RCE (EPSS: 0.03%)
- CVE-2025-40549 – Path traversal / path restriction bypass leading to RCE (EPSS: 0.07%)
While these EPSS values are modest compared to widely exploited bugs, they still indicate non-trivial exploitation likelihood and must be watched as Serv-U remains a high-value target in managed file transfer (MFT) environments.
SolarWinds’ security update and public reporting on these three CVEs were released on 2025-11-19, describing how:
- CVE-2025-40547 is a logic error that, when triggered by an authenticated administrator, allows arbitrary code execution under the Serv-U service context.
- CVE-2025-40548 is a missing validation / broken access control issue; an admin can exploit flawed authorization checks to run arbitrary code.
- CVE-2025-40549 is a path traversal / path restriction bypass, permitting an authenticated administrator to bypass directory limitations and execute code within directories that should be off-limits.
SolarWinds notes that on default Windows deployments, Serv-U services often run under less-privileged accounts, reducing practical impact in some configurations, though the vulnerabilities are still rated critical overall.
As of 2025-11-19:
- There is no public proof-of-concept exploit specifically released for these three CVEs.
- The Focus Tag and independent search both indicate that CISA’s Known Exploited Vulnerabilities (KEV) Catalog does not list CVE-2025-40547, CVE-2025-40548, or CVE-2025-40549, and there is no dedicated CISA advisory for these CVEs yet.
- These vulnerabilities are tracked in the EU Vulnerability Database (EUVD) as EUVD-2025-197930, EUVD-2025-197929, and EUVD-2025-197928, respectively, confirming their critical classification and association with Serv-U.
There is currently no public evidence that these three 2025 CVEs are being exploited in the wild. However, Serv-U has a history of exploitation for earlier directory traversal and RCE issues, such as CVE-2024-28995, which did attract active exploitation and KEV designation. That track record significantly raises concern that these newer flaws could become attractive to attackers once any reliable exploit techniques emerge.
Why should TPRM professionals care about these Serv-U vulnerabilities?
SolarWinds Serv-U is a managed file transfer and FTP platform used to move and store files across enterprise environments and between organizations. It often handles sensitive business data, including customer records, financial information, design documents, and other regulated or proprietary content.
From a third-party risk angle, several aspects matter:
- High-value role in data exchange
Serv-U frequently sits at the center of business-to-business file flows—exactly where your vendors exchange data with you or with your downstream partners. If an authenticated admin account on a vendor’s Serv-U instance is compromised, an attacker can leverage these vulnerabilities to run code on the server, manipulate files in transit, or stage follow-on attacks. - Admin requirement does not eliminate risk
All three vulnerabilities require an authenticated administrator. That might sound comforting at first, but in practice, attackers routinely obtain admin-level access via: - Phishing or credential theft,
- Password reuse across services,
- Exploitation of earlier Serv-U flaws (for example, path traversal issues that reveal logs, configuration files, or credentials), or
- Compromise of the underlying OS or identity provider.
- Once attackers have those privileges, these CVEs turn Serv-U into a ready-made RCE platform.
- Potential impact on shared data and workflows
A compromised Serv-U instance at a vendor can lead to: - Unauthorized access to files your organization has uploaded,
- Tampering or replacement of files that your systems subsequently download and trust (e.g., invoices, software packages, configuration files),
- Use of the file-transfer channel to deliver malware or backdoored files directly into your environment,
- Disruption of critical file-based workflows (e.g., nightly batch exchanges, data feeds, regulatory report transfers).
- Chaining with other MFT-targeting attacks
File transfer products have repeatedly been targeted by ransomware groups and data-extortion operations. Serv-U sits in the same family of products that adversaries have historically pursued for large-scale extortion and supply-chain access.
For TPRM professionals, the key takeaway is: any vendor operating Serv-U without upgrading to 15.5.3 and without strong controls around admin accounts is carrying more risk than the CVSS score alone would suggest, even if these specific CVEs are not yet known to be exploited.
What questions should TPRM professionals ask vendors about these Serv-U vulnerabilities?
When you reach out to vendors that may run Serv-U, targeted questions can quickly surface whether they have taken these issues seriously:
- Have you upgraded all instances of SolarWinds Serv-U to version 15.5.3 or later to mitigate the risk of CVE-2025-40547, CVE-2025-40548, and CVE-2025-40549?
- Can you confirm if you have implemented the Principle of Least Privilege to limit the attack surface by reducing the number of administrative accounts and strictly managing their permissions?
- Are you continuously monitoring Serv-U logs and underlying server systems for any unusual activity, such as attempts to execute unauthorized code, access restricted directories, or suspicious login patterns, even from authenticated administrative accounts?
- Have you reviewed and reinforced system hardening best practices to ensure Serv-U services run under less-privileged service accounts by default, especially on Windows deployments where the severity of these vulnerabilities is noted to be lower due to privilege separation?
These questions help you differentiate vendors who only applied a patch from those who have also looked at how the product is configured, who can control it, and how its logs are monitored.
Remediation recommendations for vendors subject to this risk
Vendors using Serv-U should address these vulnerabilities as a configuration and operations problem, not just a patch ticket. Recommended steps include:
- Upgrade to Serv-U 15.5.3 or later on all instances
Ensure every Serv-U FTP Server and Managed File Transfer Server deployment is upgraded to version 15.5.3 or higher, including test, development, and DR environments. Confirm upgrade success by checking version information on each instance, rather than assuming central deployment completed everywhere. - Reduce and constrain administrator accounts
Apply strict least privilege: - Minimize the number of Serv-U admin accounts,
- Use individual, named accounts rather than shared logins,
- Enforce multi-factor authentication where possible,
- Regularly review which accounts truly require administrator capabilities.
- Harden the service context and OS environment
- On Windows, run Serv-U as a dedicated low-privilege service account, not as a local administrator or highly privileged account.
- On Linux, ensure the Serv-U process runs under a restricted user with limited file-system and system-level rights.
- Limit Serv-U’s ability to access directories beyond those strictly needed for business operations.
- Monitor for misuse and anomalous behavior
- Review Serv-U’s audit logs for unusual file operations initiated by administrative accounts, particularly attempts to reach directories outside configured home paths.
- Correlate Serv-U events with OS logs (for example, unexpected process launches, script execution, or changes to file ownership/permissions originating from the Serv-U service account).
- Strengthen overall Serv-U posture
- Restrict network access so Serv-U management interfaces are not exposed broadly.
- Ensure encryption is enforced for file transfers wherever possible.
- Apply regular change-control for configuration updates and administrative actions, with alerts or approvals for sensitive changes.
Implementing these actions reduces both the likelihood that an admin account can be abused and the impact if it is.
How TPRM professionals can leverage Black Kite for these Serv-U vulnerabilities
Black Kite’s “SolarWinds Serv-U - Nov2025” FocusTag is designed to help you quickly identify which vendors are likely to be affected by CVE-2025-40547, CVE-2025-40548, and CVE-2025-40549 and prioritize outreach accordingly.
Key characteristics of this Focus Tag:
- Confidence Level: VERY HIGH
The tag is based on strong external indicators that the vendor operates SolarWinds Serv-U in ways that may intersect with the vulnerable versions. - Timing and context
The tag is dated 2025-11-19, aligned with the public disclosure of these vulnerabilities and SolarWinds’ Serv-U 15.5.3 security update, so it becomes available early in the response window. - Coverage of relevant assets
The tag associates vendors with externally observable assets (such as IP addresses and hostnames) that appear to expose Serv-U services or related infrastructure. This asset-level view lets you start conversations with vendors about specific systems rather than generic “Do you use Serv-U?” questions.
For TPRM teams, this Focus Tag enables a practical workflow:
- Filter to likely-affected vendors
Use the “SolarWinds Serv-U - Nov2025” FocusTag to shrink your vendor list down to organizations where Serv-U exposure is suspected or confirmed. - Prioritize by criticality and exploit context
Even though these CVEs are not currently in KEV and their EPSS scores are moderate, the combination of RCE and the product’s role in handling sensitive file transfers justifies prioritizing tagged vendors—especially those that provide core services or process regulated data on your behalf. - Align questionnaires with technical reality
Base your outreach on the specific questions above, tying them directly to the Serv-U instances and assets Black Kite has identified. This helps vendors respond with concrete details instead of generic assurances.
Track remediation at the asset level
As vendors upgrade to Serv-U 15.5.3 or decommission exposed instances, Black Kite’s external intelligence will reflect those changes at the IP/hostname level. You can use this to verify that vendors’ statements about patching are consistent with what is actually visible from the internet.
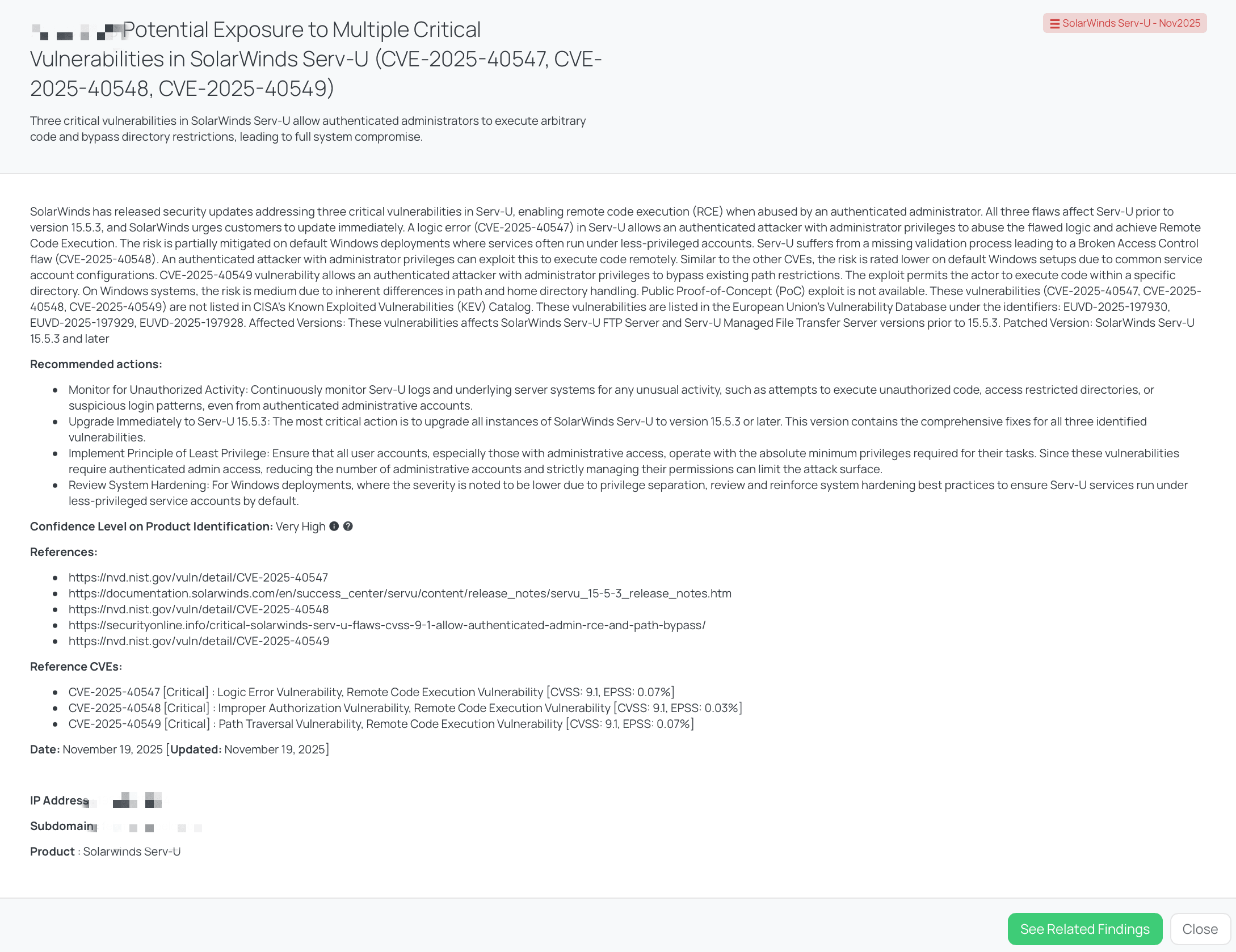
Black Kite’s SolarWinds Serv-U - Nov2025 FocusTag™ details critical insights on the event for TPRM professionals.
CVE-2025-64484 (OAuth2 Proxy)
What is the OAuth2 Proxy header smuggling vulnerability (CVE-2025-64484)?
CVE-2025-64484 is a high-severity header smuggling and injection vulnerability in OAuth2 Proxy, affecting all versions prior to 7.13.0. OAuth2 Proxy is widely used as a reverse proxy or middleware in front of web applications to enforce SSO and centralized authentication.
Technically, the issue is classified under CWE-644: Improper Neutralization of HTTP Headers for Scripting Syntax. In affected versions, OAuth2 Proxy strips and validates certain forwarding headers (such as X-Forwarded-For and X-Forwarded-Proto), but this filtering can be bypassed when upstream frameworks normalize header names differently. Many frameworks (Django, Flask, FastAPI, PHP stacks, and other WSGI-based services) treat different header spellings as equivalent, while the proxy does not.
An authenticated user can craft alternative header names (for example, using the _ character in place of -) that pass through OAuth2 Proxy’s stripping logic but are folded back into trusted X-Forwarded-* headers by the upstream application. This mismatch can enable that user to:
- Inject fake client IP information (X-Forwarded-For).
- Influence scheme or protocol assumptions (X-Forwarded-Proto).
- Manipulate other forwarding-related headers relied on for identity, access control, or trust decisions in the upstream app.
The vulnerability does not break OAuth2 Proxy’s core authentication or authorization flows. Instead, it compromises the integrity of metadata that many applications use as a second layer of trust—such as “is this coming from an internal network?” or “is this user really tied to this client IP?”. When upstream applications tie roles, tenant scopes, or administrative access to these headers, this becomes a privilege escalation issue in the application behind the proxy.
Scoring:
- CVSS v3.1: 8.5 (High)
- EPSS: ~0.06%
Timeline:
- Disclosed on 2025-11-08 through OAuth2 Proxy security channels.
- Published in NVD on 2025-11-10, updated on 2025-11-12.
- Listed in the EU Vulnerability Database under ID EUVD-2025-50825.
OAuth2 Proxy version 7.13.0 fully resolves the issue by normalizing configured headers consistently, ensuring case, dash, and underscore variants are treated equivalently. A new configuration field, InsecureSkipHeaderNormalization, was added for compatibility edge cases, though using it weakens protections and should be avoided unless absolutely required.
Exploitation Status:
- Not listed in CISA KEV as of 2025-11-19.
- No known real-world exploitation campaigns or attributed threat actors.
- Public proof-of-concept exploit code exists and demonstrates the header-smuggling behavior.
This combination—high functional impact, wide deployment footprint, and presence of a public PoC—makes CVE-2025-64484 a high-priority issue for TPRM teams despite the lack of KEV designation.
Why does CVE-2025-64484 matter for TPRM teams?
OAuth2 Proxy is frequently deployed at the entry point of applications, handling authentication, SSO enforcement, and policy decisions. When used in front of tenant-aware systems, admin portals, customer portals, or API gateways, weakened trust boundaries caused by misinterpreted headers can directly affect how a vendor protects your data.
Key considerations include:
Trust at the edge, impact deeper in the stack
Although the issue exists in the proxy layer, the damage unfolds in the application behind it. If a vendor’s upstream system treats forwarded headers as authoritative, a malicious authenticated user could impersonate trusted internal traffic, elevate privileges, or bypass important controls.
Multi-tenant and B2B environments
Many vendors use OAuth2 Proxy in front of shared systems. A low-privilege user associated with another customer—or an internal user with limited rights—could manipulate forwarding headers to gain visibility into other tenants or sensitive administrative functions.
Authenticated-only does not mean low risk
Because OAuth2 Proxy enforces authentication before access is granted, vendors often allow self-registration, partner accounts, or numerous internal identities. In such environments, a low-privilege authenticated user can exploit header-based trust assumptions.
Data exposure and integrity risks
Upstream applications may:
- Treat a request as internal-only based on forwarded IP metadata.
- Grant access to privileged administrative routes.
- Switch tenant or role contexts incorrectly.
- Leak sensitive data intended for trusted internal systems.
For TPRM professionals, this means any vendor operating OAuth2 Proxy before version 7.13.0 and using header-normalizing frameworks should be evaluated carefully.
What questions should TPRM professionals ask vendors about CVE-2025-64484?
- Have you updated all instances of OAuth2-Proxy to version 7.13.0 or later to mitigate the risk of CVE-2025-64484?
- Can you confirm if you have implemented logging and detection for unexpected underscore-based X_Forwarded-* headers or unusual combinations of X-Forwarded-* values that may indicate attempted exploitation or privilege escalation?
- Have you reviewed how your upstream applications such as Django, Flask, FastAPI, WSGI-based services, and PHP applications consume X-Forwarded-* values for identity, protocol, or access-control decisions?
- Can you confirm if you have avoided configuring InsecureSkipHeaderNormalization unless there is a documented and justified compatibility requirement? If it is enabled, what compensating controls and monitoring measures have you enforced?
Remediation recommendations for vendors facing this OAuth2 Proxy risk
To fully mitigate exposure:
Upgrade all deployments
Ensure every instance—production, staging, development, and DR—runs OAuth2 Proxy 7.13.0 or newer. Validate the live version directly on each deployment.
Preserve secure header normalization
Keep the default header-normalization behavior enabled. Avoid using InsecureSkipHeaderNormalization unless absolutely necessary and only with documented justification.
Strengthen upstream trust logic
Review how applications use X-Forwarded-For, X-Forwarded-Proto, and related metadata. Enforce role and tenant selection using authenticated session context, not solely forwarded header values.
Harden administrative behavior
Ensure admin-only functionality cannot be accessed based solely on forwarded header metadata, even if the request seems to originate from a trusted source.
Improve monitoring
Add logging and alerting for unusual header structures, especially variations in header spelling.
Handled comprehensively, these steps reduce both immediate and long-term exposure.
How TPRM professionals can leverage Black Kite for CVE-2025-64484
Black Kite’s OAuth2 Proxy FocusTag enables organizations to rapidly identify which vendors may be exposed to this vulnerability.
Key advantages:
- The tag is published with HIGH confidence, indicating strong external evidence that the vendor operates OAuth2 Proxy.
- The tag incorporates the vulnerability's CVSS 8.5 rating and EPSS 0.06% probability.
- Published on 2025-11-17, the tag also includes the EUVD identifier EUVD-2025-50825.
How TPRM teams can operationalize it:
- Reduce outreach scope: Immediately narrow vendor engagement to the subset flagged by Black Kite.
- Use asset-level intelligence: Black Kite provides the specific hostnames and IP addresses where OAuth2 Proxy appears deployed, enabling precise, evidence-based vendor questioning.
- Prioritize based on exposure: Even without a KEV listing, the existence of public PoC code and the role of OAuth2 Proxy in authentication flows justify prioritizing affected vendors.
- Track remediation over time: As vendors update or decommission vulnerable systems, Black Kite’s continuous scanning reflects those changes, giving assurance of real remediation.
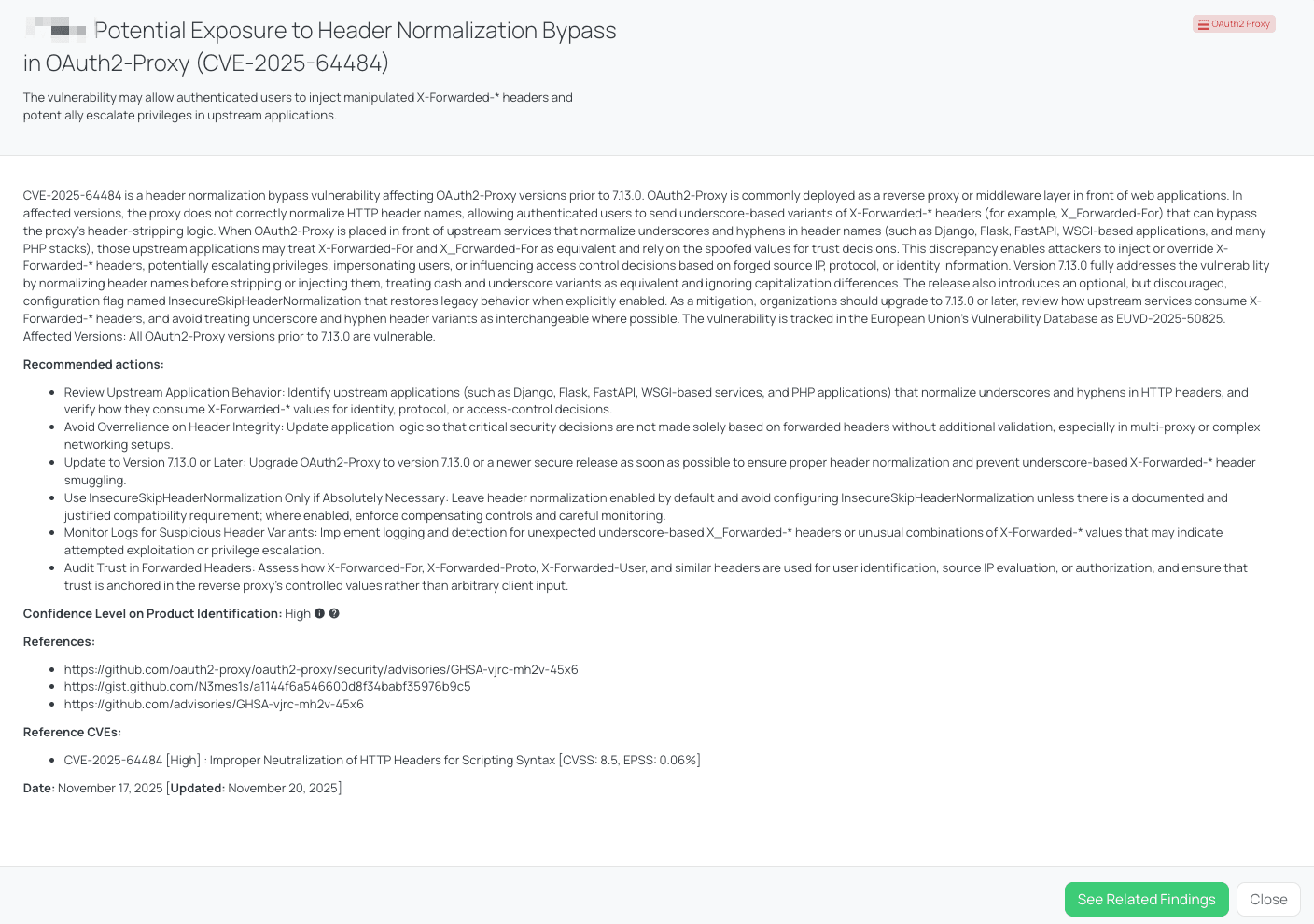
Black Kite’s OAuth2 Proxy FocusTag™ details critical insights on the event for TPRM professionals.
CVE-2025-12762, CVE-2025-12763, CVE-2025-12764, CVE-2025-12765 (pgAdmin - Nov2025)
What are the pgAdmin Multiple Vulnerabilities?
The Focus Tag for pgAdmin covers four distinct security flaws affecting versions up to 9.9 of the pgAdmin tool when used in server-mode or enterprise environments. These include:
- CVE-2025-12762 – A critical Remote Code Execution (RCE) vulnerability (CVSS 9.1, EPSS 0.08%) affecting pgAdmin when operating in server mode and performing restore operations from PLAIN-format PostgreSQL dump files. Attackers can craft malicious dump files that execute arbitrary system commands on the host.
- CVE-2025-12763 – A command-injection vulnerability (CVSS 6.8, EPSS 0.11%) for pgAdmin 4 on Windows systems. The flaw stems from unsafe shell parameter usage during backup and restore, allowing crafted file paths to execute arbitrary Windows system commands.
- CVE-2025-12764 – A high-severity LDAP injection vulnerability (CVSS 7.5, EPSS 0.06%) found in the LDAP authentication flow of pgAdmin. Attackers may inject malformed LDAP characters into the username field, which can cause denial-of-service conditions.
- CVE-2025-12765 – A high-severity TLS certificate-validation bypass within the LDAP module of pgAdmin (CVSS 7.5, EPSS 0.02%). If exploited, an attacker could intercept or alter communications between pgAdmin and the LDAP server, enabling credential theft or man-in-the-middle attacks.
These vulnerabilities were disclosed in mid-November 2025 and are also listed in the European Union Vulnerability Database. The Focus Tag indicates that none of these vulnerabilities are currently listed in CISA’s Known Exploited Vulnerabilities (KEV) catalog.
Why should TPRM professionals care about these pgAdmin vulnerabilities?
pgAdmin is widely used by organizations for PostgreSQL database administration, often in production environments that handle sensitive or business-critical data. From a third-party risk management perspective:
- Critical code-execution risk: CVE-2025-12762 enables full Remote Code Execution when restoring PLAIN-format dumps in server mode. If a vendor uses pgAdmin to manage databases tied to your organization, this can directly impact data confidentiality and integrity.
- Windows-specific command injection: CVE-2025-12763 specifically affects Windows installations. Many vendors run pgAdmin on Windows for backup or administration—if unpatched, attacker-controlled file paths can lead to full system compromise.
- Authentication and identity risks: CVE-2025-12764 and CVE-2025-12765 undermine LDAP authentication and TLS certificate verification. Exploitation may enable impersonation, privilege escalation, or unauthorized access to functions believed to be protected.
- Vendor environment trust chain: If a vendor uses pgAdmin within a data environment supporting your services, these vulnerabilities present a significant path to compromise. A breach in the vendor’s pgAdmin layer can cascade into the environments of multiple downstream customers.
What questions should TPRM professionals ask vendors about CVE-2025-12762, CVE-2025-12763, CVE-2025-12764, and CVE-2025-12765?
When assessing potentially affected vendors, targeted questions help determine whether they have truly mitigated these flaws:
- Have you updated all instances of pgAdmin to version 9.10 or later to mitigate the risk of CVE-2025-12762, CVE-2025-12763, CVE-2025-12764, and CVE-2025-12765?
- Can you confirm if you have implemented measures to block the restore if the PLAIN SQL file contains any meta-commands as recommended in the GitHub advisory for CVE-2025-12762?
- For CVE-2025-12763, have you reviewed and updated the shell parameter usage (`shell=True`) during backup and restore operations in pgAdmin 4 installations on Windows systems to prevent command injection?
- Regarding CVE-2025-12765, have you taken steps to rectify the TLS certificate verification bypass vulnerability within the LDAP authentication mechanism of pgAdmin to prevent potential man-in-the-middle (MitM) attacks?
Remediation recommendations for vendors subject to this risk
To fully address the four pgAdmin vulnerabilities, vendors should:
- Upgrade immediately to pgAdmin 9.10 or later, covering all instances across the organization.
- Secure restore operations by restricting or validating PLAIN-format dump file usage and ensuring that dump files originate from trusted sources.
- Harden Windows deployments by removing unsafe shell execution pathways and applying least-privilege configurations.
- Strengthen LDAP/TLS authentication by enforcing strict certificate validation and sanitizing all LDAP input fields.
- Limit access to pgAdmin through network segmentation, VPN-only access, and strong authentication, while monitoring administrative actions and backups.
How TPRM professionals can leverage Black Kite for this vulnerability
Black Kite’s pgAdmin – Nov2025 FocusTag allows TPRM teams to quickly identify vendors running potentially vulnerable pgAdmin deployments. The tag was published with HIGH confidence, indicating strong external signals of pgAdmin usage in vendor environments.
TPRM teams can leverage the FocusTag to:
- Reduce outreach scope, contacting only the vendors flagged as using pgAdmin.
- Prioritize assessments by combining tag visibility with business-critical vendor tiers.
- Ask more precise questions using the vulnerabilities and vectors outlined above.
- Reference asset-level intelligence, since Black Kite provides visibility into exposed hosts and domains associated with pgAdmin deployments.
- Track remediation progress as vendors patch or decommission vulnerable instances, reflected in updated external observations.
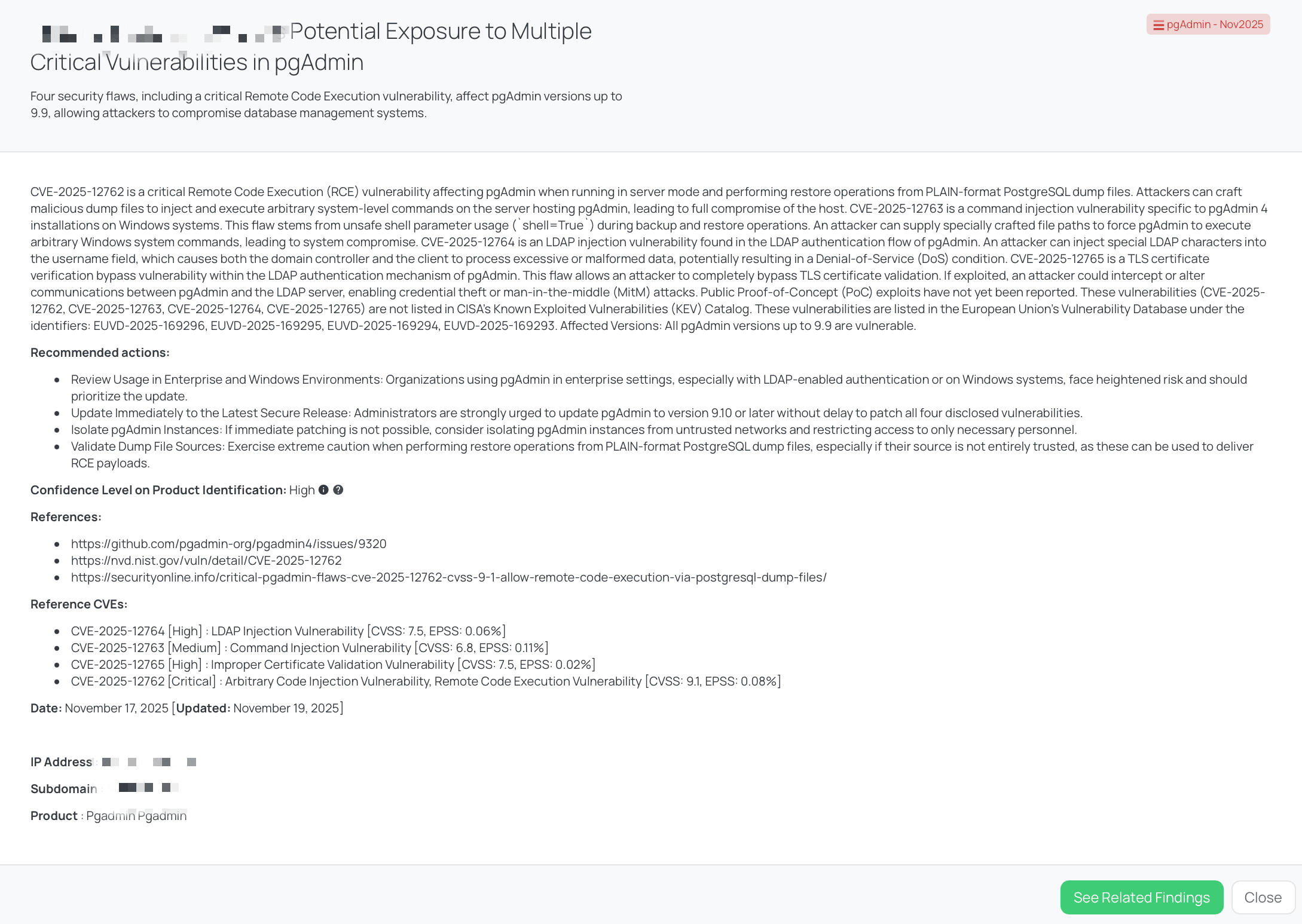
Black Kite’s pgAdmin - Nov2025 FocusTag™ details critical insights on the event for TPRM professionals.
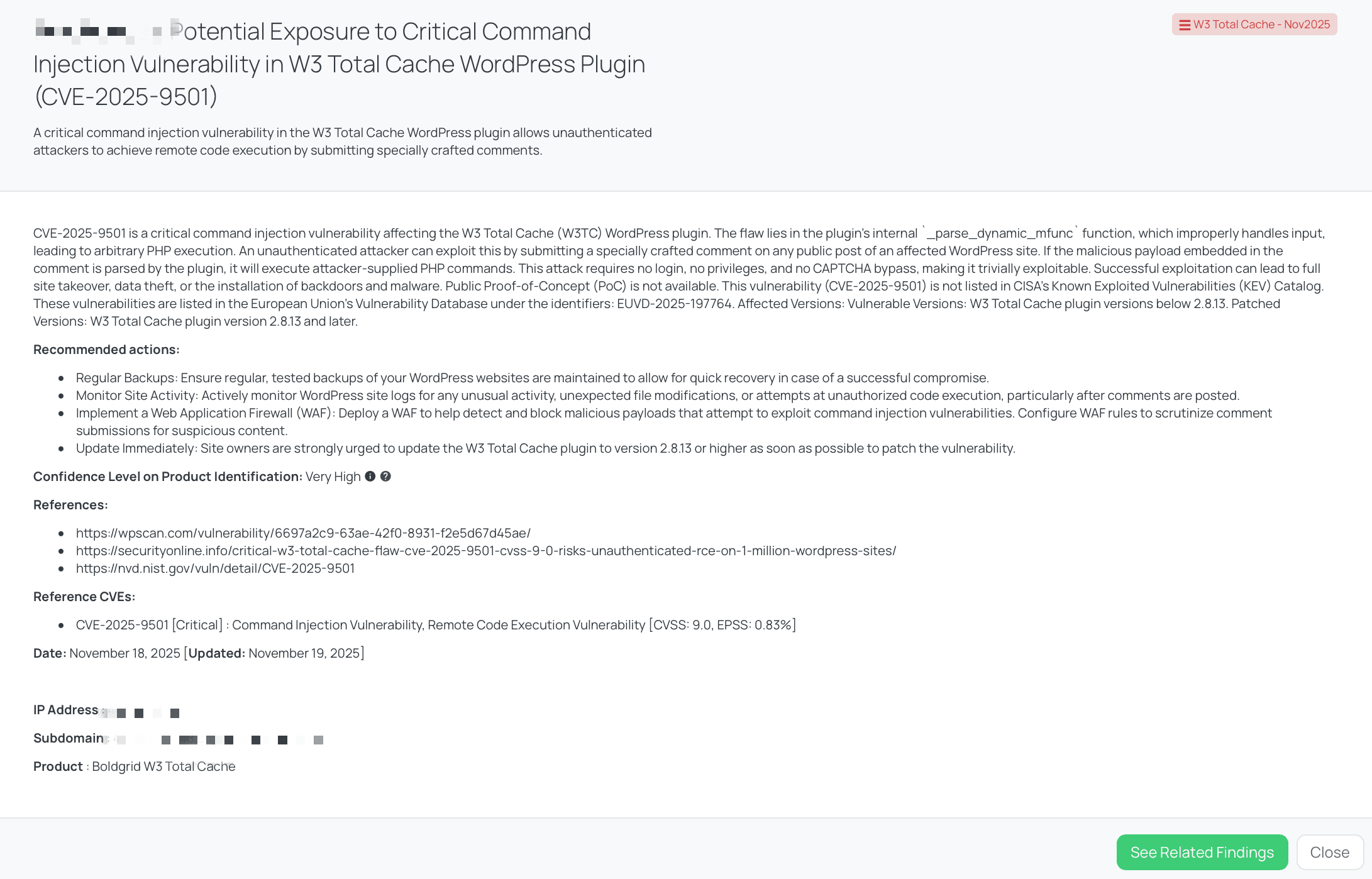
CVE-2025-9501 (W3 Total Cache - Nov2025)
What is the W3 Total Cache command injection vulnerability (CVE-2025-9501)?
CVE-2025-9501 is a critical command injection vulnerability affecting the W3 Total Cache (W3TC) WordPress plugin. The flaw resides in the plugin’s internal _parse_dynamic_mfunc function, which fails to properly sanitize input, enabling an unauthenticated attacker to submit a specially crafted comment on any public post and execute arbitrary PHP commands on the hosting WordPress site. That means no login, no user privileges and no CAPTCHA bypass are required. The vulnerability carries a CVSS score of 9.0 (Critical) and an EPSS of 0.83%. It was disclosed around November 18, 2025. There is not yet a publicly known Proof-of-Concept exploit and the vulnerability is not listed in CISA’s Known Exploited Vulnerabilities (KEV) catalog. It is tracked within the EU Vulnerability Database (EUVD-2025-197764). Affected versions include W3 Total Cache versions below 2.8.13; the patched version is 2.8.13 or later.
Why should TPRM professionals care about this vulnerability?
Because W3 Total Cache is widely deployed across WordPress sites—including many vendor/third-party sites—this vulnerability presents a serious risk within third-party risk management contexts. Specifically:
- Unauthenticated remote compromise: An attacker needs only to submit a crafted comment on a page protected by the plugin. If the vendor uses W3TC on a site interacting with or exposing data to your organization, the path to takeover is extremely short.
- Full site takeover potential: Execution of arbitrary PHP allows attackers to install backdoors, modify content, pivot into other parts of the infrastructure, or exfiltrate data.
- Shared infrastructure risk: Many vendors host multiple clients or manage WordPress multisite installations; a compromise of a single W3TC-vulnerable site can lead to broader lateral or supply-chain impacts.
- Critical plugin in web stack: Because caching plugins like W3TC sit near the front of the web stack and impact performance, they may not always receive the same scrutiny as traditional security tools—presenting an under-recognized risk exposure in vendor environments.
In your vendor-assurance dialogues, a vendor’s use of W3 Total Cache with site versions older than 2.8.13 should trigger a high-priority risk pathway.
What questions should TPRM professionals ask vendors about CVE-2025-9501?
Here are four targeted questions you may include when assessing a vendor’s exposure:
- Can you confirm if you have updated all instances of the W3 Total Cache WordPress plugin to version 2.8.13 or later to mitigate the risk of CVE-2025-9501?
- Have you implemented a Web Application Firewall (WAF) with rules specifically designed to scrutinize comment submissions for suspicious content that could exploit the command injection vulnerability in the W3 Total Cache plugin?
- Are you actively monitoring your WordPress site logs for any unusual activity, unexpected file modifications, or attempts at unauthorized code execution, particularly after comments are posted, as a measure against the CVE-2025-9501 vulnerability?
- Have you ensured regular, tested backups of your WordPress websites to allow for quick recovery in case of a successful compromise due to the CVE-2025-9501 vulnerability?
Remediation Recommendations for Vendors subject to this risk
To address this vulnerability effectively, vendors should:
- Update immediately to W3 Total Cache version 2.8.13 or later across all WordPress installations.
- Restrict access to comment-submission functionality when possible, especially on high-risk or public-facing posts, and consider disabling comments on pages not intended to receive them.
- Implement web-application firewall (WAF) rules that inspect comment payloads and filter suspicious PHP or dynamic-script content, especially on sites using W3TC.
- Monitor site integrity by reviewing logs for unexpected file modifications, PHP command execution, or upload of PHP files via comment fields.
- Enforce segmentation and least-privilege: ensure each WordPress instance is isolated; a vulnerability in one plugin instance should not permit lateral movement into other client workloads.
How TPRM professionals can leverage Black Kite for this vulnerability
The Black Kite “W3 Total Cache – Nov 2025” FocusTag comes with a VERY_HIGH confidence level, indicating strong external signals of vendor exposure to this plugin vulnerability. It allows TPRM teams to:
- Rapidly identify vendor sites running W3TC and narrow outreach to those with version exposure (<2.8.13).
- Use asset-level intelligence (exposed hostnames or domains) flagged by Black Kite to ask vendors about specific WordPress instances rather than generic “Do you use W3TC?” questions.
- Prioritize remediation: since the vulnerability is unauthenticated and RCE-capable, flagged vendors should move to the “high risk” remediation queue.
- Track vendor remediation progress: as vendors patch or remove vulnerable plugin versions, external signals captured by Black Kite will reflect this change and allow you to monitor until the exposure disappears.
Black Kite’s W3 Total Cache - Nov2025 FocusTag™ details critical insights on the event for TPRM professionals.
ENHANCING THIRD-PARTY RISK MANAGEMENT WITH BLACK KITE’S FOCUS TAGS™
As demonstrated by this week’s vulnerabilities—spanning web application firewalls, file transfer services, authentication middleware, database administration tools, and WordPress plugins—modern vendor ecosystems frequently incorporate diverse and complex technologies that can rapidly introduce risk. Black Kite’s FocusTags™ help TPRM teams stay ahead of these challenges by delivering targeted, actionable intelligence.
Immediate Exposure Identification:
FocusTags™ highlight vendors affected by vulnerabilities such as these FortiWeb, Serv-U, OAuth2 Proxy, pgAdmin, and W3 Total Cache issues. Instead of sending broad questionnaires to hundreds of vendors, TPRM teams can immediately narrow their scope to those with confirmed exposure.
Strategic Prioritization of Vendor Outreach:
By combining vulnerability severity with vendor criticality, FocusTags™ guide practitioners toward the most urgent remediation pathways—ensuring high-impact risks receive prompt attention while minimizing unnecessary vendor friction.
Sharper, More Efficient Vendor Engagement:
Each FocusTag™ provides precise context, enabling TPRM professionals to ask informed, relevant questions based on the specific vulnerability affecting a vendor’s environment. This leads to more efficient review cycles and reduces the fatigue that often accompanies repetitive or generic security questionnaires.
Strengthening Overall Risk Posture:
With a clear view of how vulnerabilities propagate across the supply chain, organizations can make better strategic decisions. FocusTags™ help security and risk teams understand where systems like authentication proxies, caching plugins, or database tools may introduce systemic weaknesses, allowing proactive mitigation and long-term strengthening of security practices.
Black Kite’s FocusTags™ transform raw vulnerability data into meaningful intelligence, enabling organizations to manage third-party cyber risks with greater clarity, speed, and precision—an essential advantage in a landscape where new vulnerabilities continue to emerge across diverse vendor technologies.
About Focus Friday
Every week, we delve into the realms of critical vulnerabilities and their implications from a Third-Party Risk Management (TPRM) perspective. This series is dedicated to shedding light on pressing cybersecurity threats, offering in-depth analyses, and providing actionable insights.
FocusTags™ in the Last 30 Days:
- FortiWeb [Suspected] : CVE-2025-64446, CVE-2025-58034, Authentication Bypass Vulnerability, Path Traversal Vulnerability, OS Command Injection Vulnerability in Fortinet FortiWeb Web Application Firewall.
- SolarWinds Serv-U - Nov2025 : CVE-2025-40547, CVE-2025-40548, CVE-2025-40549, Logic Error Vulnerability, Improper Authorization Vulnerability, Path Traversal Vulnerability, Remote Code Execution Vulnerabilities in SolarWinds Serv-U.
- OAuth2 Proxy : CVE-2025-64484, Improper Neutralization Of HTTP Headers For Scripting Syntax Vulnerability, Header Smuggling Vulnerability, Potential Privilege Escalation Vulnerability in OAuth2 Proxy.
- pgAdmin - Nov2025 : CVE-2025-12762, CVE-2025-12763, CVE-2025-12764, CVE-2025-12765, Remote Code Execution Vulnerability, Command Injection Vulnerability, LDAP Injection Vulnerability, TLS Certificate Verification Bypass Vulnerability in pgAdmin.
- W3 Total Cache - Nov2025 : CVE-2025-9501, Command Injection Vulnerability, Remote Code Execution Vulnerability in W3 Total Cache WordPress Plugin.
- Microsoft SharePoint - Nov2025 : CVE-2025-62204, Deserialization of Untrusted Data Vulnerability, Remote Code Execution Vulnerability in Microsoft Office SharePoint.
- MSSQL - Nov2025 : CVE-2025-59499, Improper Neutralization of Special Elements in SQL Commands, SQL Injection Vulnerability, Privilege Escalation Vulnerability in Microsoft SQL Server.
- Elastic Kibana - Nov2025 : CVE-2025-37734, CVE-2025-59840, Server-Side Request Forgery (SSRF) Vulnerability, DOM-based Cross-site Scripting (XSS) Vulnerability, Improper Input Validation Vulnerability in Elastic Kibana.
- Django - Nov2025 : CVE-2025-59681, CVE-2025-59682, SQL Injection Vulnerability, Directory Traversal Vulnerability, Improper Input Sanitization Vulnerability in Django Web Framework.
- Open WebUI - Nov2025 : CVE-2025-64495, Stored DOM XSS Vulnerability, Account Takeover Vulnerability, Remote Code Execution Vulnerability in Open WebUI.
- MOVEit - Oct2025 : CVE-2025-10932, Uncontrolled Resource Consumption Vulnerability, Denial of Service Vulnerability in Progress MOVEit Transfer.
- Redis - Nov2025 : CVE-2025-62507, Improper Input Validation Vulnerability, Stack-based Buffer Overflow Vulnerability, Remote Code Execution Vulnerability in Redis.
- Control Web Panel (CWP) : CVE-2025-48703, Remote Code Execution Vulnerability, OS Command Injection Vulnerability in CentOS Control Web Panel.
- DNN Software - Oct2025 : CVE-2025-64095, Improper Access Control Vulnerability, Unrestricted Upload of File Vulnerability, Arbitrary File Write Vulnerability, Remote Code Execution Vulnerability, Cross-site Scripting Vulnerability in DNN Software.
- XWiki Platform : CVE-2025-24893, Remote Code Execution Vulnerability in XWiki Platform.
- MikroTik RouterOS & SwOS : CVE-2025-61481, Arbitrary Code Execution Vulnerability, Man-in-the-Middle (MITM) Attack Vulnerability in MikroTik RouterOS & SwOS.
- Apache Tomcat - Oct2025 : CVE-2025-55752, CVE-2025-55754, CVE-2025-61795, Remote Code Execution, Authorization Bypass, Path Traversal, File Upload, Improper Neutralization of Escape, Meta, or Control Sequences, Improper Resource Shutdown or Release, Improper Input Validation, Authentication Bypass, Denial of Service Vulnerabilities in Apache Tomcat.
- Vault - Oct2025 : CVE-2025-12044, CVE-2025-11621, Denial of Service, Allocation of Resources Without Limits or Throttling, Authentication Bypass, Improper Authentication Vulnerabilities in Vault.
- LiteSpeed - Oct2025 : CVE-2025-12450, Cross-site Scripting (XSS) Vulnerability in LiteSpeed.
- Samba Server : CVE-2025-10230, Remote Code Execution Vulnerability in Samba servers.
- Atlassian Jira - Oct2025 : CVE-2025-22167, CVE-2025-58057, CVE-2025-58056, CVE-2025-7962, CVE-2025-48989, Path Traversal, Arbitrary File Write, Remote Code Execution (RCE), Denial of Service (DoS), Request Smuggling, SMTP Injection, Improper Resource Shutdown or Release (MadeYouReset DDoS) vulnerabilities in Atlassian Jira Software and Jira Service Management.
- TP-Link Omada Gateways : CVE-2025-6541, CVE-2025-6542, CVE-2025-7850, CVE-2025-7851, OS Command Injection vulnerabilities and Unauthorized Root Access via Debug Functionality in TP-Link Omada Gateways.
See Black Kite’s full CVE Database and the critical TPRM vulnerabilities that have an applied FocusTag™ at https://blackkite.com/cve-database.
References
https://nvd.nist.gov/vuln/detail/CVE-2025-64446
https://labs.watchtowr.com/when-the-impersonation-function-gets-used-to-impersonate-users-fortinet-fortiweb-auth-bypass/
https://securityonline.info/zero-day-attack-warning-fortinet-fortiweb-exploit-grants-unauthenticated-admin-access/
https://fortiguard.fortinet.com/psirt/FG-IR-25-910
https://securityonline.info/critical-solarwinds-serv-u-flaws-cvss-9-1-allow-authenticated-admin-rce-and-path-bypass/
https://documentation.solarwinds.com/en/success_center/servu/content/release_notes/servu_15-5-3_release_notes.htm
https://www.cve.org/CVERecord?id=CVE-2025-40547
https://www.cve.org/CVERecord?id=CVE-2025-40548
https://www.cve.org/CVERecord?id=CVE-2025-40549
https://github.com/advisories/GHSA-vjrc-mh2v-45x6
https://gist.github.com/N3mes1s/a1144f6a546600d8f34babf35976b9c5
https://github.com/oauth2-proxy/oauth2-proxy/security/advisories/GHSA-vjrc-mh2v-45x6
https://nvd.nist.gov/vuln/detail/CVE-2025-12762
https://securityonline.info/critical-pgadmin-flaws-cve-2025-12762-cvss-9-1-allow-remote-code-execution-via-postgresql-dump-files/
https://github.com/pgadmin-org/pgadmin4/issues/9320
https://nvd.nist.gov/vuln/detail/CVE-2025-9501
https://securityonline.info/critical-w3-total-cache-flaw-cve-2025-9501-cvss-9-0-risks-unauthenticated-rce-on-1-million-wordpress-sites/
https://wpscan.com/vulnerability/6697a2c9-63ae-42f0-8931-f2e5d67d45ae/