Focus Friday: TPRM Actions for Critical Citrix NetScaler and Salesforce Tableau Vulnerabilities
Welcome to this week’s edition of Focus Friday, where we analyze high-profile cybersecurity events through the lens of Third-Party Risk Management (TPRM). This week’s blog highlights two urgent vulnerability clusters that demand immediate attention: the Citrix NetScaler “CitrixDeelb” flaws (including CVE-2025-7775, now confirmed as exploited in the wild and listed in CISA’s KEV) and multiple Salesforce Tableau vulnerabilities that can lead to remote code execution, path traversal, and improper file handling.
Both Citrix and Salesforce products occupy critical roles in enterprise environments: NetScaler as a gateway for secure remote access and Tableau as a backbone for business analytics. Vulnerabilities in these systems introduce not just technical risk but potential disruption of business operations and exposure of sensitive data across interconnected vendor ecosystems. In this blog, we break down what these vulnerabilities mean, how TPRM professionals should approach them, and how Black Kite’s FocusTags™ simplify the process of pinpointing impacted vendors.

Filtered view of companies with Citrix NetScaler – Aug2025 FocusTag™ on the Black Kite platform.
CVE-2025-7775, CVE-2025-7776, CVE-2025-8424 – CITRIX NETSCALER ADC & GATEWAY
We shared a detailed write-up on the CitrixDeelb vulnerability on August 27, 2025.
What are the vulnerabilities affecting Citrix NetScaler?
On August 26, 2025, Citrix (Cloud Software Group) published a security bulletin addressing three severe flaws in NetScaler ADC and Gateway. These bugs are collectively tracked under the campaign term CitrixDeelb.
- CVE-2025-7775 [Critical] – Memory Overflow, Remote Code Execution & DoS
- CVSS: 9.8 | EPSS: 7.67%
- A memory overflow in multiple NetScaler core functions, exploitable pre-authentication.
- Allows remote, unauthenticated attackers to execute arbitrary code or crash appliances.
- Requires specific configurations (Gateway/AAA vServers; IPv6 load balancing; HDX CR).
- Exploited in the wild: Confirmed. Web-shell drops observed on unpatched devices.
- CISA KEV: Added August 26, 2025 with a patch deadline of August 28, 2025.
- CVE-2025-7776 [High] – Memory Overflow
- CVSS: 8.8 | EPSS: 0.04%
- Another memory overflow bug, primarily causing denial of service.
- Exploitable if a Gateway vServer has a PCoIP profile bound, a setting used in VDI deployments.
- No active exploitation reported as of publication, but disruption risk is high in environments relying on PCoIP.
- CVE-2025-8424 [High] – Improper Access Control
- CVSS: 8.7 | EPSS: 0.03%
- Affects the management interface (NSIP, Cluster Mgmt IP, GSLB Site IP, or SNIP with management access).
- Allows unauthenticated attackers with network access to bypass controls, execute admin commands, or read sensitive configs.
- No confirmed exploitation; not yet in CISA KEV. However, the management-plane nature makes it a high-impact risk.
Affected versions: NetScaler ADC and Gateway 14.1, 13.1 (including FIPS/NDcPP), and 12.1 (FIPS/NDcPP) prior to patched builds (14.1-47.48, 13.1-59.22, 13.1-37.241, 12.1-55.330). Older 12.1 and 13.0 branches are end-of-life and remain unpatched.
ALERT: On 2025-08-26, Shadowserver scans revealed 28,200+ unpatched Citrix NetScaler instancesvulnerable to CVE-2025-7775. Active exploitation was confirmed the same day in CISA KEV. The largest exposures are in the United States and Germany.
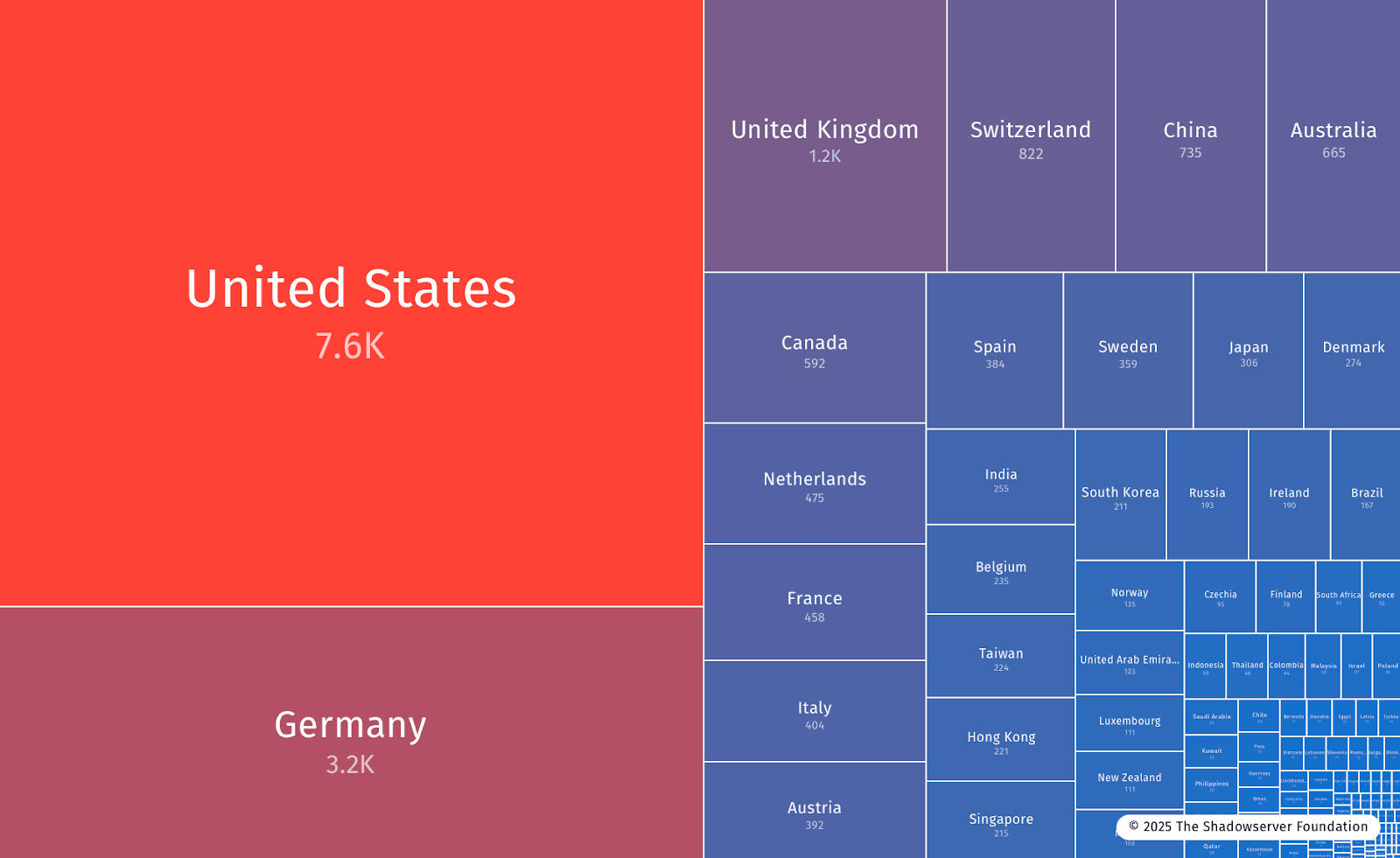
28,200+ unpatched Citrix NetScaler servers hit by CVE-2025-7775, mostly in the U.S. and Germany.
Why should TPRM professionals care about these vulnerabilities?
NetScaler ADC and Gateway devices act as remote access gateways and application delivery controllers—often exposed to the internet. If compromised:
- CVE-2025-7775 could allow adversaries to hijack the appliance pre-auth, implant web shells, and pivot deep into enterprise systems.
- CVE-2025-7776 can disrupt remote access infrastructure, affecting vendors relying on VDI/PCoIP, causing downtime.
- CVE-2025-8424 opens the management plane, risking full administrative takeover of a vendor’s Citrix infrastructure.
From a third-party risk perspective, if a supplier’s NetScaler edge is compromised, attackers gain a foothold into their internal apps and data. That foothold can cascade across supply chains, exposing sensitive session tokens, credentials, and communications.
What questions should TPRM professionals ask vendors?
When engaging vendors, targeted technical questions should be asked:
- Have you upgraded all instances of NetScaler ADC and NetScaler Gateway to the patched versions (14.1-47.48, 13.1-59.22, 13.1-37.241, and 12.1-55.330) to mitigate the risk of CVE-2025-7775, CVE-2025-7776, and CVE-2025-8424?
- Can you confirm if your NetScaler appliances are configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, or RDP Proxy) or an AAA virtual server, or a load balancing virtual server of type HTTP, SSL, or HTTP_QUIC that’s configured with IPv6 services or service groups, or a Content Routing virtual server of type HDX, which are the specific configurations vulnerable to CVE-2025-7775?
- Is your NetScaler appliance configured as a Gateway (VPN virtual server) with a PCoIP Profile bound to it, which is the specific configuration vulnerable to CVE-2025-7776?
- 4. Have you reviewed and restricted access to the NSIP, Cluster Management IP, Local GSLB Site IP, or a SNIP with management access, which are the specific configurations vulnerable to CVE-2025-8424?
Remediation recommendations for vendors subject to this risk
Vendors should take the following urgent actions:
- Apply patches immediately to fixed builds (14.1-47.48, 13.1-59.22, 13.1-37.241, 12.1-55.330).
- Restrict management plane access—enforce IP allowlists, use jump hosts, and eliminate internet exposure of NSIP/Cluster/GSLB IPs.
- Terminate active ICA/PCoIP sessions post-upgrade where PCoIP is used.
- Conduct retroactive hunts in logs for suspicious requests to /vpn/, /cgi/, or /menu/, as well as unexpected file creation.
- Remove unsupported builds (12.1, 13.0 EOL) from production; migrate to supported releases.
- Monitor for persistence: confirm no web shells or unauthorized files exist after patching.
How can TPRM professionals leverage Black Kite for this vulnerability?
Black Kite published the Citrix NetScaler – Aug 2025 FocusTag on August 27, 2025. The tag provides:
- Vendor identification: Highlights organizations running vulnerable NetScaler assets, including external IPs and subdomains.
- Attack surface context: Differentiates between internet-facing gateways and internal-only instances.
- Operational tracking: Updates when Citrix releases advisories or when KEV/CISA changes status.
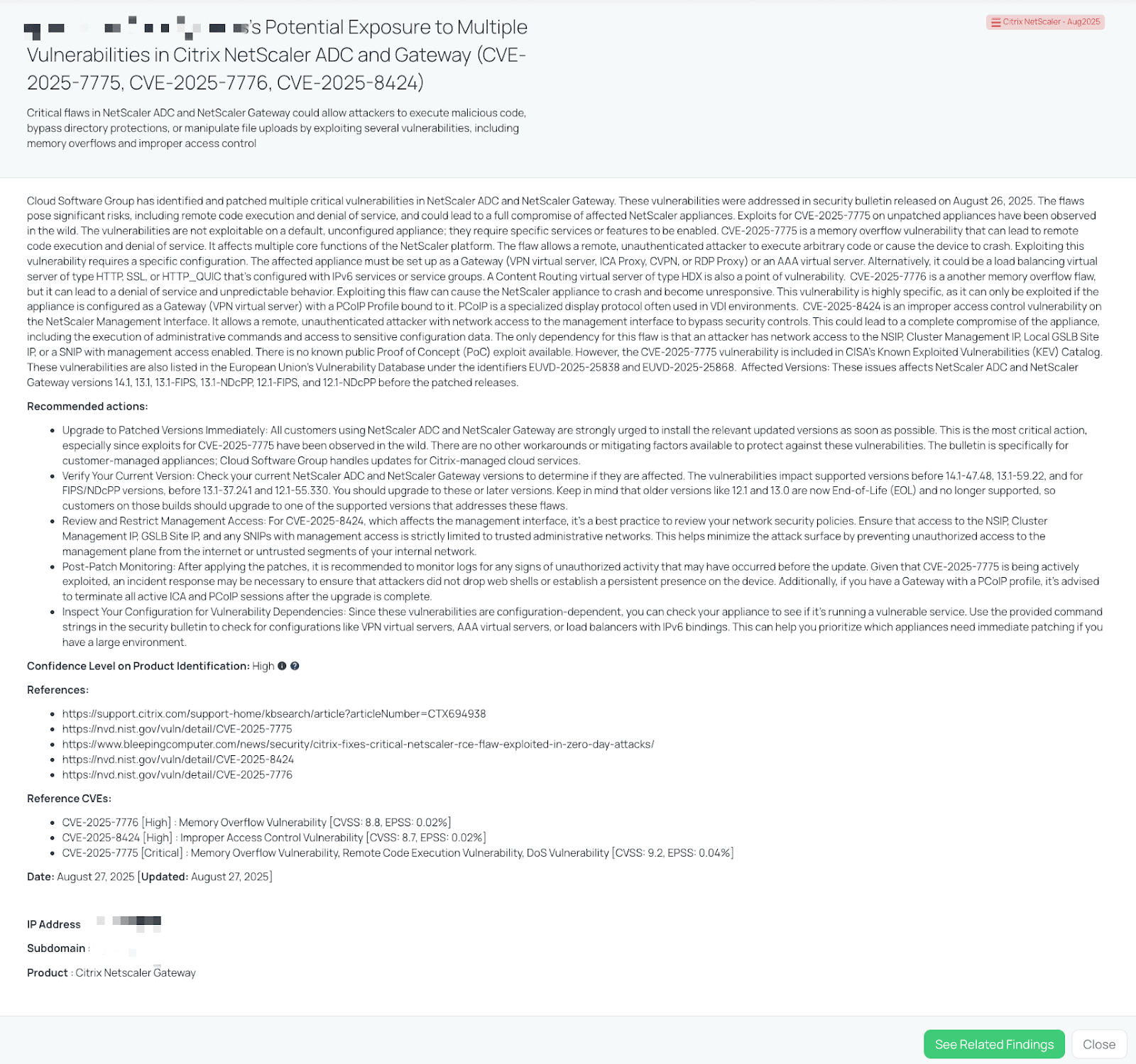
Black Kite’s Citrix NetScaler – Aug2025 Attack FocusTag™ details critical insights on the event for TPRM professionals.
CVE-2025-26496, CVE-2025-26497, CVE-2025-26498, CVE-2025-52450, CVE-2025-52451 – SALESFORCE TABLEAU
What are the vulnerabilities affecting Salesforce Tableau?
Salesforce’s July 22, 2025, maintenance release addressed multiple critical and high-severity flaws in Tableau Server and Tableau Desktop.
- CVE-2025-26496 (Critical, CVSS 9.3, EPSS 0.01%) – A type confusion vulnerability in the File Upload modules, enabling remote code execution through local code inclusion. No authentication is required, which raises the exposure level considerably. It has been cataloged in the EUVD under ID EUVD-2025-22744.
- CVE-2025-26497 & CVE-2025-26498 (High, CVSS 7.3, EPSS 0.04%) – Unrestricted file upload flaws in the Flow Editor and establish-connection-no-undo modules. These enable absolute path traversal, potentially allowing overwrites of system files or malicious file placement.
- CVE-2025-52450 (High, CVSS 6.5, EPSS 0.02%) – A path traversal flaw within the tabdoc API file upload process, allowing bypass of directory restrictions.
- CVE-2025-52451 (High, CVSS 8.5, EPSS 0.02%) – An improper input validation issue in the same API, permitting absolute path traversal and unauthorized file access.
These vulnerabilities affect Tableau Server prior to versions 2025.1.4, 2024.2.13, and 2023.3.20, as well as Tableau Desktop versions prior to the same releases. No public proof-of-concept exploit is known, and none of these CVEs are currently listed in CISA’s KEV catalog. Salesforce confirmed that exploitation in the wild has not been observed to date.
Why should TPRM professionals care about these vulnerabilities?
Tableau is a widely used analytics and reporting solution, meaning a successful exploit could compromise sensitive business intelligence data, financial reports, or regulated customer datasets. Unauthorized file uploads or path traversal could give attackers persistence on analytics servers or backdoor access to enterprise systems. Because Tableau often integrates with broader data lakes and databases, a compromise in this layer could cascade to connected environments, expanding the impact beyond reporting to core business operations.
What questions should TPRM professionals ask vendors about the vulnerabilities?
When assessing exposure, TPRM professionals should focus on both patch management and evidence of monitoring controls. Suggested questions include:
- Have you updated all instances of Salesforce Tableau Server and Tableau Desktop to versions 2025.1.4, 2024.2.13, or 2023.3.20 or later to mitigate the risk of CVE-2025-26496, CVE-2025-26497, CVE-2025-26498, CVE-2025-52450, and CVE-2025-52451?
- 2. Can you confirm if you have implemented the patches provided in the July 22, 2025, maintenance release to address the type confusion flaw in the File Upload modules of Tableau Server and Tableau Desktop, specifically related to CVE-2025-26496?
- Have you taken measures to address the Unrestricted Upload of File with Dangerous Type vulnerabilities (CVE-2025-26497 and CVE-2025-26498) in the Flow Editor and establish-connection-no-undo modules of Tableau Server, which could lead to unauthorized file overwrites or the creation of malicious files in arbitrary locations on the server?
- Can you confirm if you have addressed the path traversal and improper input validation vulnerabilities (CVE-2025-52450 and CVE-2025-52451) in the `tabdoc` API’s file upload mechanisms, which could enable attackers to bypass directory restrictions and gain unauthorized access to sensitive files?
Remediation recommendations for vendors subject to this risk
Vendors running Tableau should act promptly:
- Upgrade immediately to Tableau Server 2025.1.4 / 2024.2.13 / 2023.3.20 or Tableau Desktop versions at or above these levels.
- Review file handling policies in analytics workflows, tightening controls on uploads and user permissions.
- Monitor and audit logs for unusual file-related activity, especially signs of attempted file overwrites or path traversal exploitation.
- Harden server exposure by restricting access to Tableau from internal networks only, or enforcing authentication if external access is required.
- Apply compensating controls such as web application firewalls with upload inspection rules until patching is verified.
How can TPRM professionals leverage Black Kite for these vulnerabilities?
Black Kite published the Salesforce Tableau – Aug 2025 FocusTag on August 25, 2025. Customers can use this FocusTag to immediately identify vendors operating vulnerable Tableau assets, including affected subdomains and IP addresses. This targeted intelligence eliminates the need to broadly query all vendors, enabling teams to prioritize those demonstrably at risk.
By operationalizing this tag, organizations can:
- Receive an instant inventory of vendors with exposed Tableau environments.
- Prioritize vendor outreach with the precise versions and assets identified by Black Kite.
- Track updates: if Salesforce or CISA releases new information (such as KEV additions), Black Kite updates the tag accordingly.
This granular vendor-level intelligence helps TPRM professionals respond swiftly, focusing on vendors that matter instead of exhausting resources across their entire supply chain.
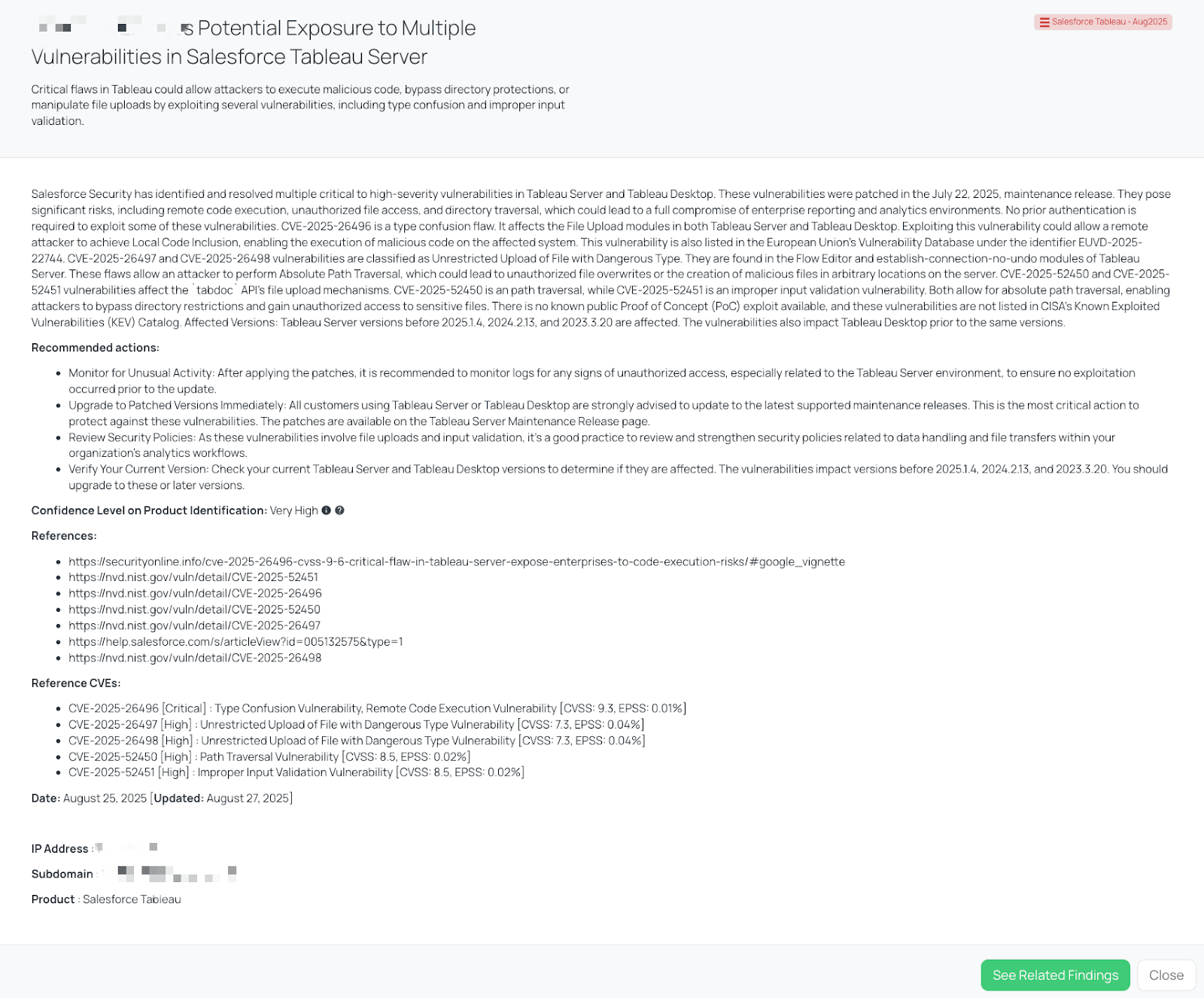
Black Kite’s Salesforce Tableau – Aug2025 FocusTag™ details critical insights on the event for TPRM professionals.
ENHANCING THIRD-PARTY RISK MANAGEMENT WITH BLACK KITE'S FOCUSTAGS™
In light of the recent Citrix and Salesforce vulnerabilities, the value of Black Kite’s FocusTags™ becomes even clearer. These tags transform complex, rapidly evolving vulnerability data into actionable intelligence for TPRM teams by:
- Immediate Risk Identification – Highlighting which vendors are directly impacted by Citrix NetScaler and Salesforce Tableau exposures, enabling precise and timely outreach.
- Risk Prioritization – Allowing organizations to concentrate resources on the vendors and vulnerabilities that present the highest operational and data security risks.
- Informed Vendor Engagement – Equipping TPRM teams with targeted questions about patch status, configuration settings, and mitigation measures specific to Citrix and Salesforce products.
- Operational Insight – Providing context such as external-facing IP addresses and subdomains associated with vulnerable assets, helping organizations verify vendor exposure in real time.
By leveraging FocusTags™, organizations can cut through the noise of mass vendor questionnaires and zero in on the entities most at risk from these two pressing vulnerability clusters. This approach not only saves time but also strengthens resilience across the vendor ecosystem, ensuring that response efforts are focused where they will have the greatest impact.
ABOUT FOCUS FRIDAY
Every week, we delve into the realms of critical vulnerabilities and their implications from a Third-Party Risk Management (TPRM) perspective. This series is dedicated to shedding light on pressing cybersecurity threats, offering in-depth analyses, and providing actionable insights.
FOCUSTAGS™ IN THE LAST 30 DAYS:
- Citrix NetScaler – Aug2025 : CVE-2025-7775, CVE-2025-7776, CVE-2025-8424, Memory Overflow Vulnerability, Remote Code Execution Vulnerability, DoS Vulnerability, Improper Access Control Vulnerability in Citrix NetScaler ADC/Gateway.
- Salesforce Tableau – Aug2025 : CVE-2025-26496, CVE-2025-26497, CVE-2025-26498, CVE-2025-52450, CVE-2025-52451, Type Confusion Vulnerability, Remote Code Execution Vulnerability, Unrestricted File Upload Vulnerability, Path Traversal Vulnerability, Improper Input Validation Vulnerability in Salesforce Tableau.
- MadeYouReset HTTP/2 DoS Attack : CVE-2025-8671, CVE-2025-48989, CVE-2025-54500, CVE-2025-55163, CVE-2025-36047, MadeYouReset DoS Vulnerability in HTTP/2.
- Ivanti Connect Secure – Aug2025 : CVE-2025-5456, CVE-2025-5462, Out-of-bound Read Vulnerability, DoS Vulnerability, Buffer Overflow Vulnerability in Ivanti Connect Secure (ICS), Ivanti Policy Secure (IPS), Ivanti ZTA Gateway, Ivanti Neurons for Secure Access.
- PostgreSQL – Aug2025 : CVE-2025-8713, CVE-2025-8714, CVE-2025-8715, Arbitrary Code Injection Vulnerability, Exposure of Sensitive Information Vulnerability in PostgreSQL.
- Plesk Obsidian : CVE-2025-54336, Incorrect Comparison Vulnerability in Plesk Obsidian.
- Exchange Server – Aug2025 : CVE-2025-53786, CVE-2025-25005, CVE-2025-25006, CVE-2025-25007, CVE-2025-33051, Improper Authentication, Input Validation, and Information Disclosure Vulnerabilities.
- MSSQL – Aug2025 : CVE-2025-49758, CVE-2025-24999, CVE-2025-53727, CVE-2025-49759, CVE-2025-47954, Privilege Escalation and SQL Injection Vulnerabilities.
- N-able N-Central RMM : CVE-2025-8875, CVE-2025-8876, Command Injection Vulnerability in N-able N-Central RMM.
- Squid Proxy – Aug2025 : CVE-2025-54574, Buffer Overflow Vulnerability in Squid Proxy.
- SonicWall SSL VPN – Jul2025 : CVE-2025-40600, Denial of Service Vulnerability in SonicWall SSL VPN.
- Sophos Firewall : CVE-2025-7382, CVE-2024-13973, and CVE-2024-13974, OS Command Injection Vulnerability, SQL Injection Vulnerability, Remote Code Execution Vulnerability in Sophos Firewall.
- Salesforce Tableau : CVE-2025-52446, CVE-2025-52447, CVE-2025-52448, CVE-2025-52449, CVE-2025-52452, CVE-2025-52453, CVE-2025-52454, and CVE-2025-52455, Authorization Bypass Vulnerability, Unrestricted File Upload Vulnerability, Path Traversal Vulnerability, Server-Side Request Forgery (SSRF) Vulnerability in Salesforce Tableau.
- SharePoint ToolShell : CVE-2025-49704, CVE-2025-49706, CVE-2025-53770, and CVE-2025-53771, Code Injection Vulnerability, Improper Authentication Vulnerability, Remote Code Execution Vulnerability, Path Traversal Vulnerability in Microsoft SharePoint.
- Grafana – Jul2025 : CVE-2025-6023, CVE-2025-6197, Cross-site Scripting (XSS) Vulnerability and Open Redirect Vulnerability in Grafana.
See Black Kite’s full CVE Database and the critical TPRM vulnerabilities that have an applied FocusTagTM at https://blackkite.com/cve-database.
REFERENCES
https://blackkite.com/blog/citrixdeelb-what-the-latest-citrix-vulnerabilities-mean-for-tprm
https://support.citrix.com/support-home/kbsearch/article?articleNumber=CTX694938
https://nvd.nist.gov/vuln/detail/CVE-2025-7775
https://nvd.nist.gov/vuln/detail/CVE-2025-7776
https://nvd.nist.gov/vuln/detail/CVE-2025-8424
https://www.infosecurity-magazine.com/news/citrix-patch-netscaler-zero-days
https://thehackernews.com/2025/08/citrix-patches-three-netscaler-flaws.html
https://www.darkreading.com/vulnerabilities-threats/citrix-zero-day-under-active-attack
https://github.com/NCSC-NL/citrix-2025
https://help.salesforce.com/s/articleView?id=005132575&type=1
https://nvd.nist.gov/vuln/detail/CVE-2025-52450
https://nvd.nist.gov/vuln/detail/CVE-2025-52451
https://nvd.nist.gov/vuln/detail/CVE-2025-26498