Expert Insights: U.S. Federal Government Risk in 2022
By Katherine Desy, with insights from Mike Brown, Tony Monell, and Bob Maley
As the largest consumer in the world, the U.S. Government spends over $650 billion annually on products and services through private sector companies, creating an indivisible connection between public and private sector organizations. The public sector relies heavily on private innovation, allowing them to keep pace with technological advancement, but equally creates cybersecurity challenges that are becoming more difficult to overcome.
Last month, Black Kite Research released Centralizing Supply Chain Cybersecurity: U.S. Federal Government Risk in 2022 where we asked four experts to weigh in on the state of national cybersecurity and the safety of critical infrastructure. Three of those four came together last week for a live discussion – Here are a few takeaways.
Watch On-Demand
Is the Government Doing Enough?
Our experts agree on one thing: The government is doing a lot, but not enough of the right thing. Through initiatives from Executive Orders, new policies and regulations to comply with, and resources like stopransomware.gov, there is no shortage of guidance. Unfortunately much of the guidance out there today is contradictory and often leaves organizations unsure of where to invest time and resources. Retired US Navy Rear Admiral Mike Brown believes this has caused organizations to lose track of the fundamentals, i.e. basic cyber hygiene.
“In both my public and private sector experience, I’ve found that most cybersecurity issues lead to the road of cyber hygiene. I believe we will never get ahead of the wave if we don’t have visibility into potential vulnerabilities and activities on an ongoing basis, prioritize them, and make genuine efforts to fix them.”
The Department of Defense and Defense Industrial Base companies are some of the most well-resourced and capable organizations in the world, so it is imperative that senior cyber leaders work to create a set of executable rules that deliver capability for all organizations.
“Left of Bang”
Born from the Marine Corps’ Combat Hunter Program, being “left of bang” means ingesting information about your existing environment and analyzing it on the fly to predict what’s going to happen. Being left of bang/boom is a common theme in cybersecurity these days, making sure you are ahead of attack vectors before they become available for exploitation.
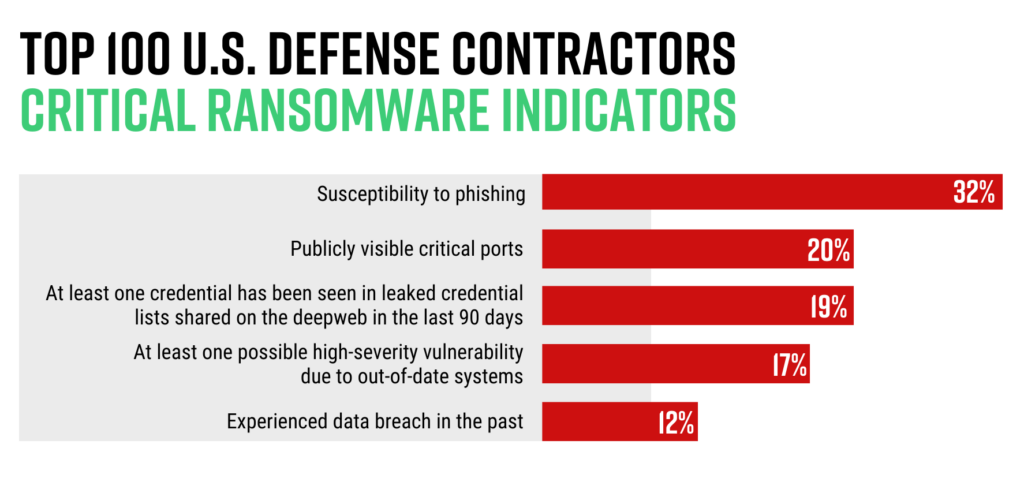
A key example of this? Compromised credentials. According to Black Kite Research, 72% of the top 100 U.S. defense contractors have had at least one credential leak in the last 90 days, and 19% have at least one credential that was shared on the deep/dark web in the last 90 days. When lost, stolen or exposed, credentials give attackers unobstructed access. There are a number of ways to better protect employee credentials, like password managers or single sign-on applications, but it is also imperative to have continuous visibility into your supply chain risks.
Keep a Finger on the Pulse
While the government continues to work on simplifying standards and best practices, there are some important steps you can take to stay ahead of adversaries. Tony Monell, Black Kite’s VP of Public Sector recommends:
- Start with a service that incorporates all vendor data into one analytical tool – Make sure it’s based on globally-recognized standards, like those from MITRE and NIST
- Ensure the platform is able to scale deeply within your vendor base – Know your third parties deeply and thoroughly, but also have a sense of who their third parties are, i.e. your fourth parties
- Stay left of bang with step-by-step vulnerability remediation guidance – Especially helpful for your small to mid-sized vendors and partners who may not have robust cybersecurity support
Black Kite uses non-intrusive, powerful scans that tap a vast data lake, accessing information on 34 million public and private companies — 4x that of our competitors. We can help you illuminate your entire supply chain in minutes and manage current regulatory requirements with the industry’s largest repository of threat intelligence.
See the Platform in Action
