Cuba Ransomware Targets Critical Infrastructure – Warranting FBI and CISA Warning
Written by Ferhat Dikbiyik
Additional Contributors Ekrem Celik and Gizem Toprak
Edited by Haley Williams
Over the last calendar year, Cuba ransomware groups have targeted key critical infrastructure across the United States and the globe. These industries include Financial Services, Government Facilities, Healthcare and Public Health, Critical Manufacturing, and Information Technology.
The FBI and CISA have released a joint advisory about the Cuba ransomware group, stating that they have attacked 49 entities in these critical infrastructure sectors and obtained at least $43.9 million in ransom payments.
What do we know about the attacks?
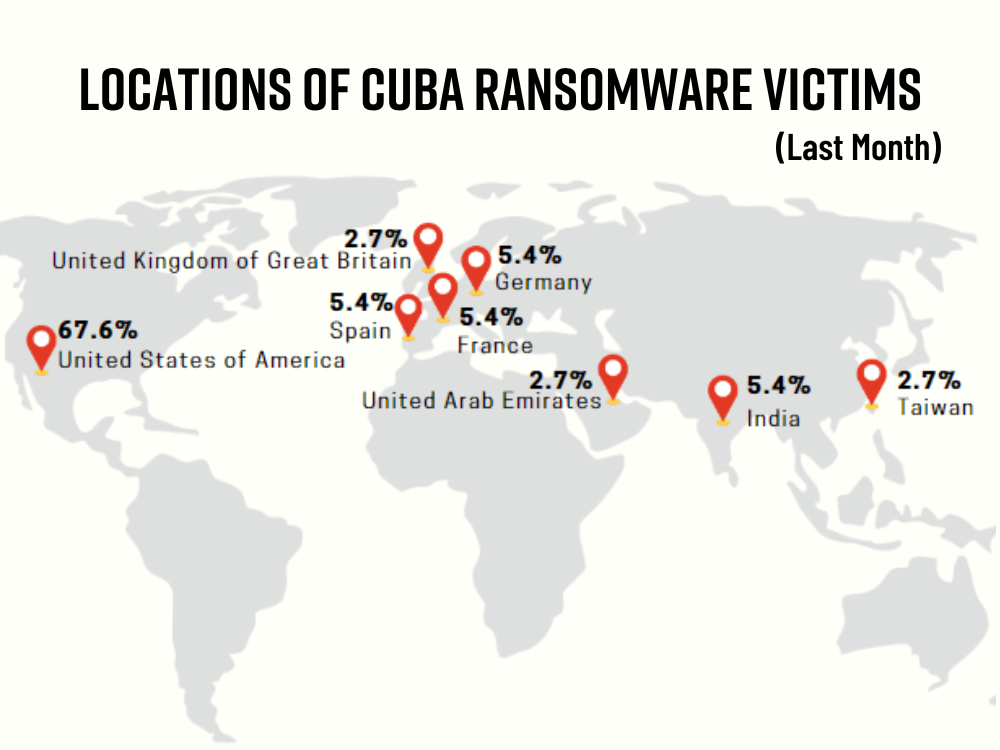
- Roughly 32 victims have been disclosed in the last month, and 23 are from the U.S. entities.
- Cuba ransomware group has attacked 49 critical infrastructure entities and made at least $43.9 million in ransom payments.
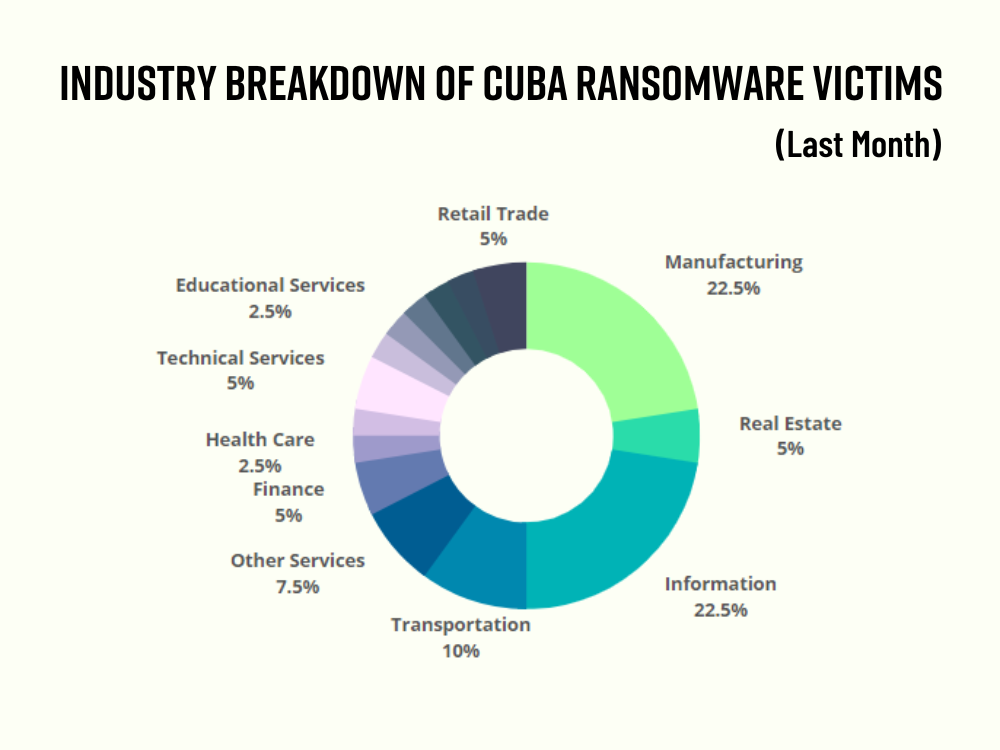
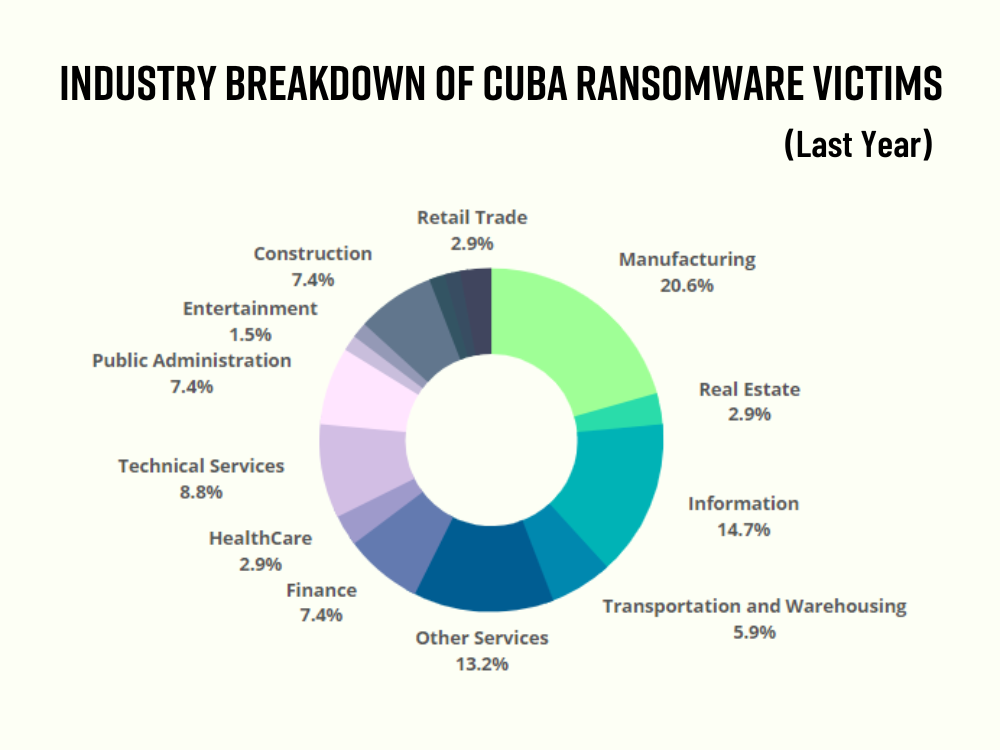
- Of the 32 victims, ten are in IT, and nine are in manufacturing.
- Over 100 entities worldwide have been compromised
- Threat actors have demanded over $145 million in ransom payments.
What do we know about Cuba ransomware?
Cuba ransomware is a Windows malware written in C++ that surfaced in late 2019. Despite being silent for a long time, the Cuba ransomware group, which has been on the rise recently, has managed to attract attention in the cyber security community.

Black Kite Research monitors ransomware groups and victims closely. Cuba ransomware group is one the infamous groups under the radar of Black Kite. We analyzed their recent victims to shed more light on their recent operations and the current cybersecurity postures of the victims.
U.S. Companies are top target
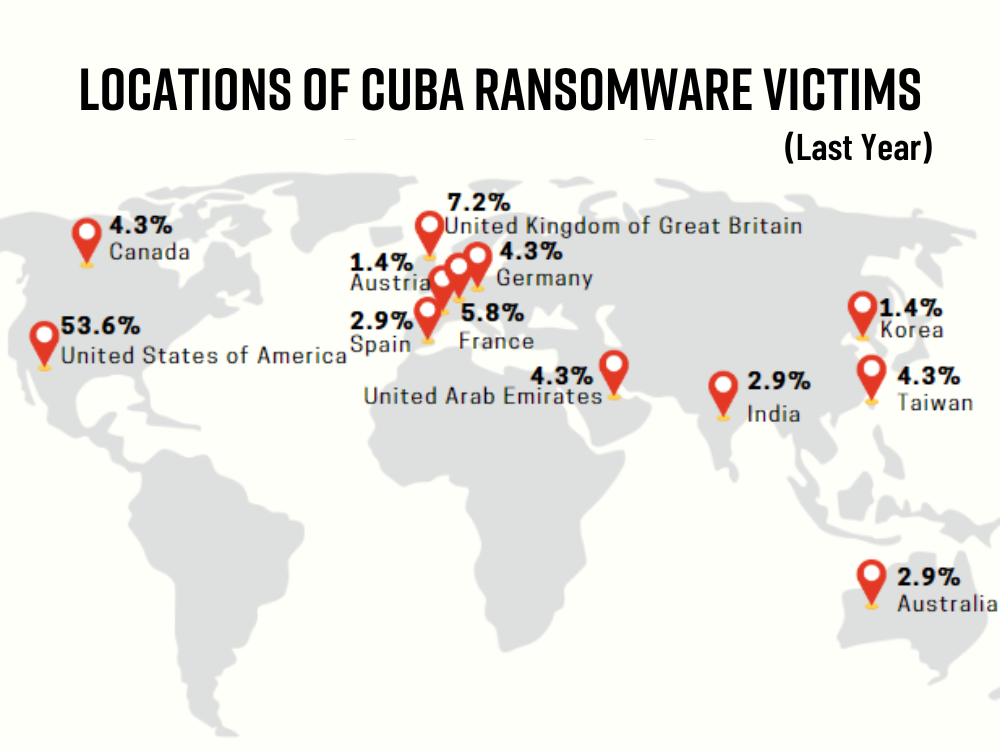
About 32 victims have been disclosed in the last 30 days, and 23 of them are U.S. based companies. Despite the group’s adoption of Cuban ideals and Cuban leaders, there is no indication that Cuba ransomware actors have any connection or affiliation with the Republic of Cuba. According to several sources, it is thought to be a Russian-based group, based on the language they use in negotiations with companies. Recently, the ratio of US victims has increased.
IT and Manufacturing sectors suffered the most
Of the 32 victims, 10 were in the IT industry and 9 were in the manufacturing industry. Apart from these two sectors, which are also on the list of industries that FBI alerted about, finance, government, and healthcare were warned.
Techniques, Tactics, and Procedures (TTPs) of Cuba Ransomware Group
Cuba ransomware actors have continued to target US entities in critical infrastructure sectors such as financial services, healthcare and public health, critical manufacturing, information technology, and government facilities.
As of August 2022, FBI has identified that the actors have compromised over 100 entities worldwide and demanded over $145 million in ransom payments. Since spring 2022, the actors have modified their tactics and tools to exploit known vulnerabilities and elevate privileges on compromised systems.
They have also used “double extortion” techniques, exfiltrating data and threatening to release it if a ransom payment is not made. According to the CISA report, there is an apparent link between the Cuba ransomware actors and RomCom RAT and Industrial Spy ransomware actors.

Example of Powershell Script code used by Cuba ransomware group
The Cuba ransomware group has been using spam campaigns to deliver their ransomware. In these campaigns, they send emails containing a link that pretends to be for a popular document signing service. When users interact with this link, they download a Word document containing a Hancitor payload. Hancitor then downloads additional tools via a command and control server to facilitate lateral movement and data extraction. It then delivers and installs the Cuba ransomware payload on compromised systems.
In earlier campaigns, it was unclear how the group delivered their ransomware, though there have been unconfirmed reports suggesting it may have been distributed through spear-phishing attacks.
Once the action is executed, the Cuba ransomware uses a hardcoded list to identify and terminate certain SQL and Microsoft Exchange services and processes. It then scans all directories and files on the host system, encrypting any files that are not on a hardcoded whitelist of exempt files.
The ransomware uses a hybrid ChaCha20 and RSA encryption method, appending the .cuba file extension to each encrypted file and dropping a ransom note in each directory where files have been encrypted. Cuba campaigns often use “double extortion,” a technique where data is stolen and encrypted, and then publicly exposed on a Tor data leak site if the ransom is not paid.

Example of encrypted with .cuba files
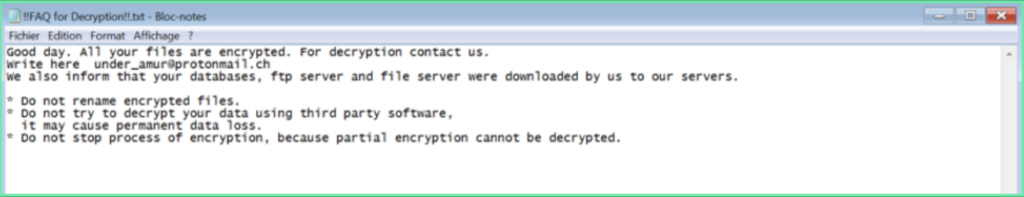
Every encrypted file contains this information
TTPs listed on CISA advisory:
- Known vulnerabilities in commercial software [T1190]
- Phishing campaigns [T1566]
- Compromised credentials [T1078]
- Legitimate remote desktop protocol (RDP) tools [T1563.002]
Some of the known vulnerabilities used by the group are:
- CVE-2022-24521 in the Windows Common Log File System (CLFS) driver
- CVE-2020-1472 (also known as “ZeroLogon”)
- CVE-2021-34527 (also known as “PrintNightmare”) – Windows Print Spooler RCE Vulnerability
The current cybersecurity posture of Cuba Ransomware victims
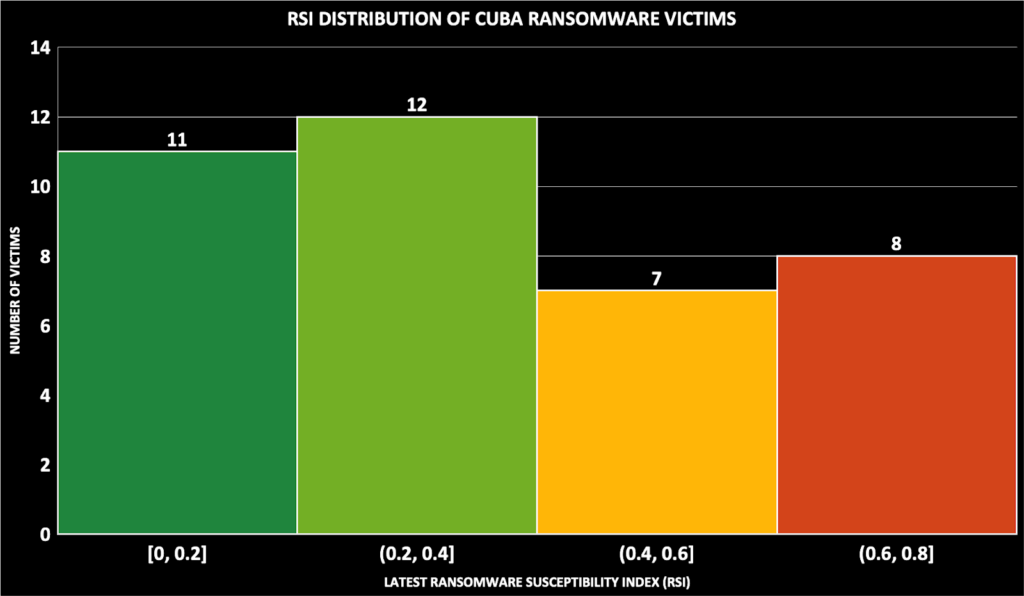
The current cybersecurity posture of the Cuba Ransomware victims have weaknesses matching the TTPs of Cuba ransomware. For instance, 46% of the victims attacked in the last 90 days have possible critical vulnerabilities due to the use of out-of-date systems. Almost 20% still have at least one credential leaked in the last 90 days.
Both critical vulnerabilities with high exploitability and leaked credentials are part of Black Kite’s Ransomware Susceptibility Index® (RSI™) metric and other indicators such as poor email configuration, industrial risk, etc. RSI™ discovers the likelihood that an organization will experience a ransomware attack.
Even after the ransomware attacks, we still see that 41% of the victims have an RSI™ score of 0.4 and 22% are over the critical threshold of 0.6.
How should your team approach the risk of Cuba ransomware attacks?
The FBI and CISA joint advisory provides information about the group’s tactics, techniques, and procedures, plus their apparent link to other ransomware groups. They also include recommendations for protecting against other ransomware attacks.
CISA and FBI have also issued recommendations for reducing the risk of attacks using Cuba ransomware. Some specific mitigations recommended by CISA and the FBI include regularly backing up important files, implementing strong security measures, and educating employees on recognizing and avoiding potential ransomware attacks.
- Companies should provide cybersecurity awareness training for employees, which should be repeated regularly.
- Back-up files frequently.
- Restrict employees’ access to the internal network; if someone makes a mistake, it is easier to bounce back without significant consequences.
- Keep software and systems used in the company up-to-date and new
- Use software that requires remote access more carefully and do not make it public if possible.